If you’re in charge of cybersecurity for a United States government agency, you’re already familiar with Memorandum M-22-09, “Moving the[…]
Leggi di più
If you’re in charge of cybersecurity for a United States government agency, you’re already familiar with Memorandum M-22-09, “Moving the[…]
Leggi di più
For the second year, the Microsoft AI Tour will bring together security practitioners, developers, and other technology professionals to learn[…]
Leggi di più
Today’s remote workforce has become the standard. But the security challenges created by remote work continue to be a key[…]
Leggi di più
Get ready to ignite your passion for innovation at the 2024 Power Platform Community Conference (PPCC). This year, we’re bringing[…]
Leggi di più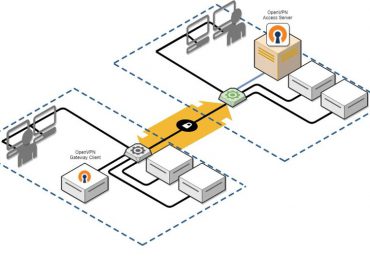
Microsoft researchers recently identified multiple medium severity vulnerabilities in OpenVPN, an open-source project with binaries integrated into routers, firmware, PCs,[…]
Leggi di più
We are announcing the release of the recently published Zero Trust practice guide in collaboration between Microsoft and the National[…]
Leggi di più
AI is driving unprecedented opportunities for businesses. With advancements in AI and low-code development platforms, organizations are finding new ways[…]
Leggi di più
The era of AI brings many opportunities to companies, from boosts in productivity to generative AI applications and more. As[…]
Leggi di più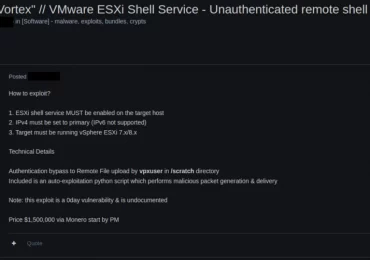
Microsoft researchers have uncovered a vulnerability in ESXi hypervisors being exploited by several ransomware operators to obtain full administrative permissions[…]
Leggi di più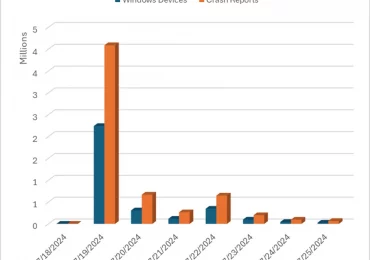
Windows is an open and flexible platform used by many of the world’s top businesses for high availability use cases[…]
Leggi di più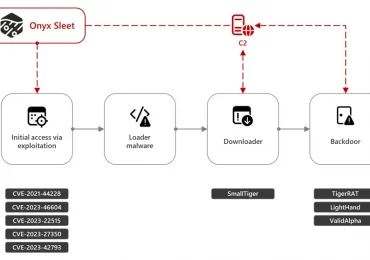
On July 25, 2024, the United States Department of Justice (DOJ) indicted an individual linked to the North Korean threat[…]
Leggi di più