
The Deputy CISO blog series is where Microsoft Deputy Chief Information Security Officers (CISOs) share their thoughts on what is most[…]
Leggi di più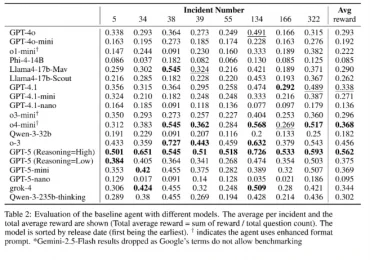
ExCyTIn-Bench is Microsoft’s newest open-source benchmarking tool designed to evaluate how well AI systems perform real-world cybersecurity investigations.1 It helps[…]
Leggi di più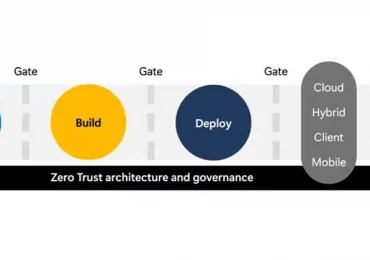
At Microsoft, building a lasting security culture is more than a strategic priority—it is a call to action. Security begins[…]
Leggi di piùProfessional developers building on Power Pages often rely on the productivity and performance of Power Pages Visual Studio Code for[…]
Leggi di più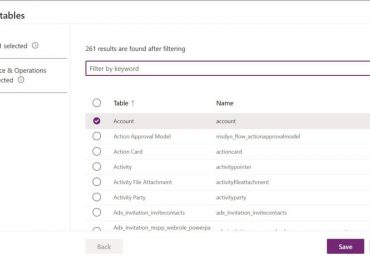
We’re committed to making data integration between Microsoft Dataverse and Microsoft Fabric faster, simpler, and more secure. These new capabilities address the most common customer[…]
Leggi di più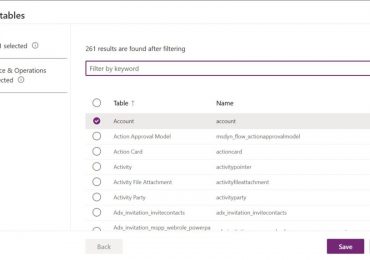
We’re committed to making data integration between Microsoft Dataverse and Microsoft Fabric faster, simpler, and more secure. These new capabilities address the most common customer[…]
Leggi di più
Security is a core focus at Microsoft Ignite 2025, reflected in dedicated sessions and hands-on experiences designed for security professionals[…]
Leggi di più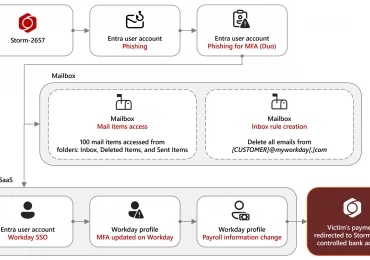
Microsoft Threat Intelligence has observed a financially motivated threat actor that we track as Storm-2657 compromising employee accounts to gain[…]
Leggi di più
As innovation speeds up, staying agile is essential. To keep your business ahead of the curve with innovation across Microsoft Dynamics[…]
Leggi di più
As innovation speeds up, staying agile is essential. To keep your business ahead of the curve with innovation across Microsoft Dynamics[…]
Leggi di più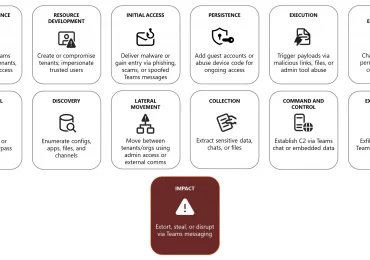
The extensive collaboration features and global adoption of Microsoft Teams make it a high-value target for both cybercriminals and state-sponsored[…]
Leggi di piùBuilding on the momentum of our initial launch of the Microsoft Secure Future Initiative (SFI) patterns and practices, this second[…]
Leggi di più