
Numerous cybersecurity tools exist to help organizations protect their data, people, and systems. There are different tools that check emails for phishing attempts, secure infrastructure and cloud, and provide generative AI to detect threats and uplevel response beyond human ability. While each of these tools is valuable on[…]
Read More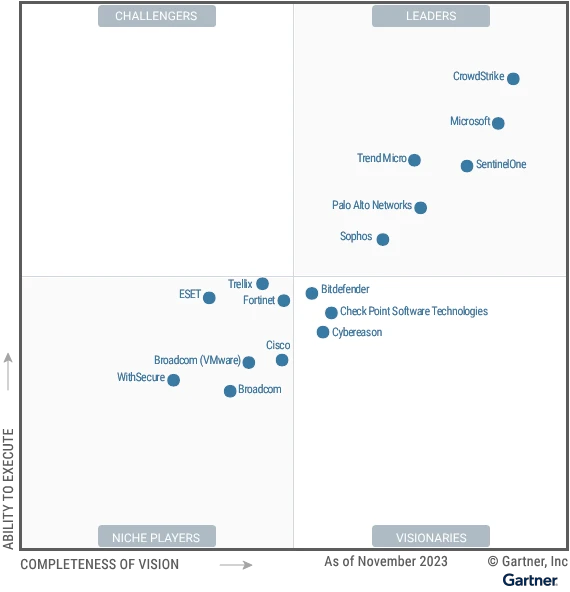
It’s no secret that ransomware is top of mind for many chief information security officers (CISOs) as the number of attacks has increased exponentially. As seen in the latest Microsoft Digital Defense Report, our “telemetry indicates that organizations faced an increased rate of ransomware attacks compared to last[…]
Read More
The security landscape is changing fast. In 2023, we saw a record-high 30 billion attempted password attacks per month, a 35% increase in demand for cybersecurity experts, and a 23% annual rise in cases processed by the Microsoft Security Response Center and Security Operations Center teams.1 This increase[…]
Read More
Since mid-November 2023, Microsoft Threat Intelligence has observed threat actors, including financially motivated actors like Storm-0569, Storm-1113, Sangria Tempest, and Storm-1674, utilizing the ms-appinstaller URI scheme (App Installer) to distribute malware. In addition to ensuring that customers are protected from observed attacker activity, Microsoft investigated the use of[…]
Read More
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Along with every merger and acquisition between two companies comes the need to combine and strengthen their IT infrastructure. In particular, there is an immediate and profound impact on the identity and[…]
Read More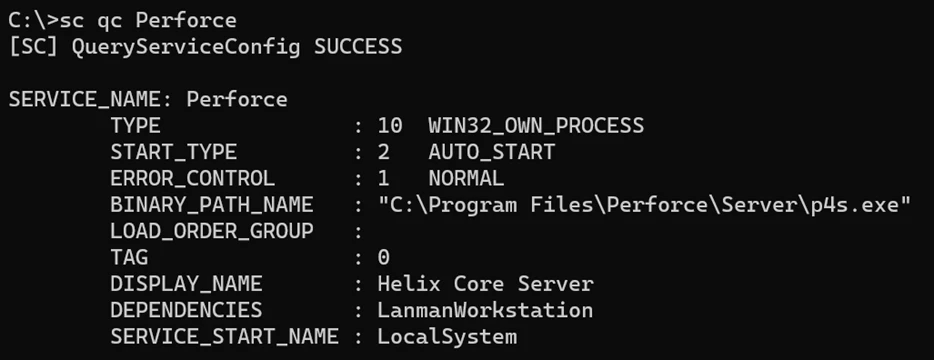
Microsoft discovered, responsibly disclosed, and helped remediate four vulnerabilities that could be remotely exploited by unauthenticated attackers in Perforce Helix Core Server (“Perforce Server”), a source code management platform largely used in the videogame industry and by multiple organizations spanning government, military, technology, retail, and more. Perforce Server[…]
Read More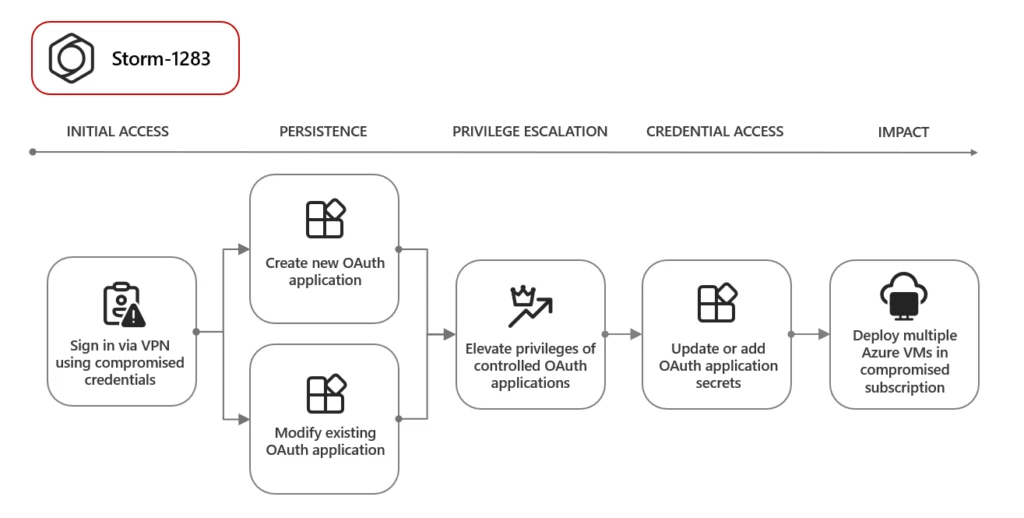
Threat actors are misusing OAuth applications as an automation tool in financially motivated attacks. OAuth is an open standard for token-based authentication and authorization that enables applications to get access to data and resources based on permissions set by a user. Threat actors compromise user accounts to create,[…]
Read MoreThe post Strengthening identity protection in the face of highly sophisticated attacks appeared first on Microsoft Security Blog. Source: Microsoft Security
Read More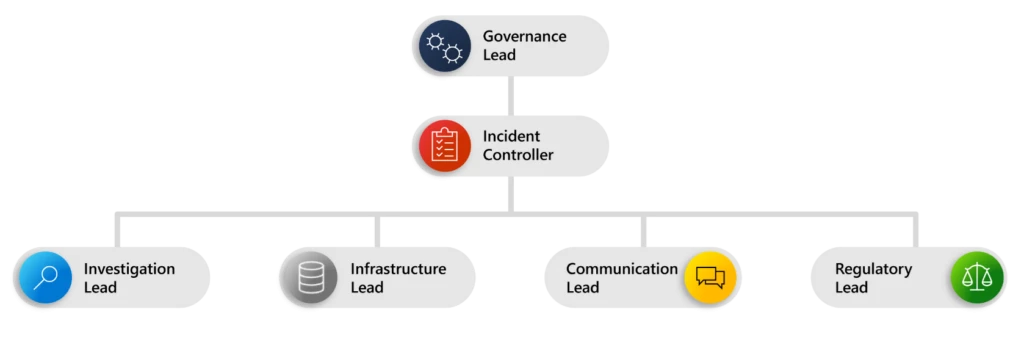
As enterprise networks grow in both size and complexity, securing them from motivated cyberthreat actors becomes more challenging. The incident response process can be a maze that security professionals must quickly learn to navigate—which is no easy task. Surprisingly, many organizations still lack a coordinated incident response plan,[…]
Read More
In the past few years, we have witnessed how digital and cloud transformation has accelerated the growth of data. With more and more customers moving to the cloud, and with the rise of hybrid work, data usage has moved beyond the traditional borders of business. Data is now[…]
Read More