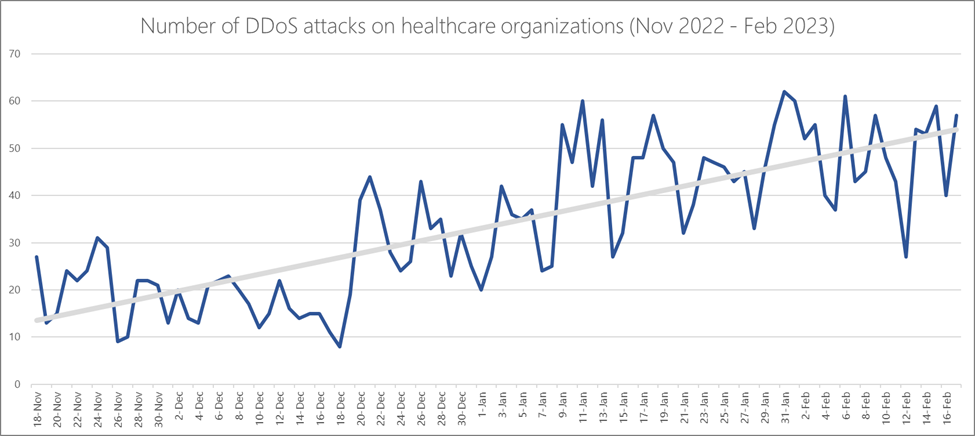
In the last year, geopolitical tension has led to an uptick of reported cybercrime events fueled by hacktivist groups. The US Cybersecurity and Infrastructure Security Agency (CISA) published an advisory to warn organizations about these attacks and teamed with the FBI on a distributed denial-of-service (DDoS) response strategy[…]
Read MoreMicrosoft Secure is our first flagship event designed just for security professionals. On March 28, 2023, we will bring together security professionals from around the world to explore security information and event management (SIEM) and extended detection and response (XDR), threat intelligence, AI, data security, multicloud security, and[…]
Read More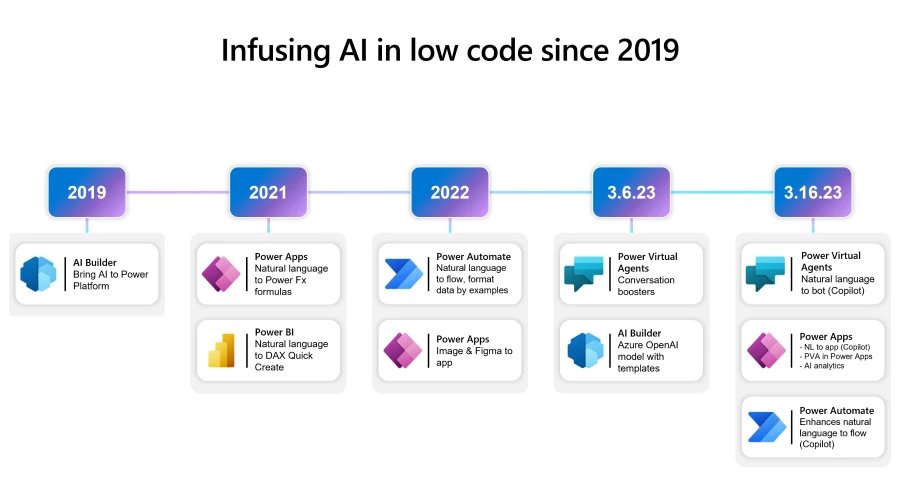
Microsoft Power Platform is reinventing software development with AI-powered no-code development. Today, Microsoft Power Platform is announcing Copilot in Power Apps, Power Automate, and Power Virtual Agents further democratizing development and enabling even more people to create innovative solutions through natural language. Now, if you can imagine your solution,[…]
Read MoreWe’re living in a seismic era for data security. Chief information security officers (CISOs) have to contend with a digital landscape that seems to shift daily as more organizations move to remote and hybrid work, redrawing the boundaries for how data is used and shared. The cloud has[…]
Read More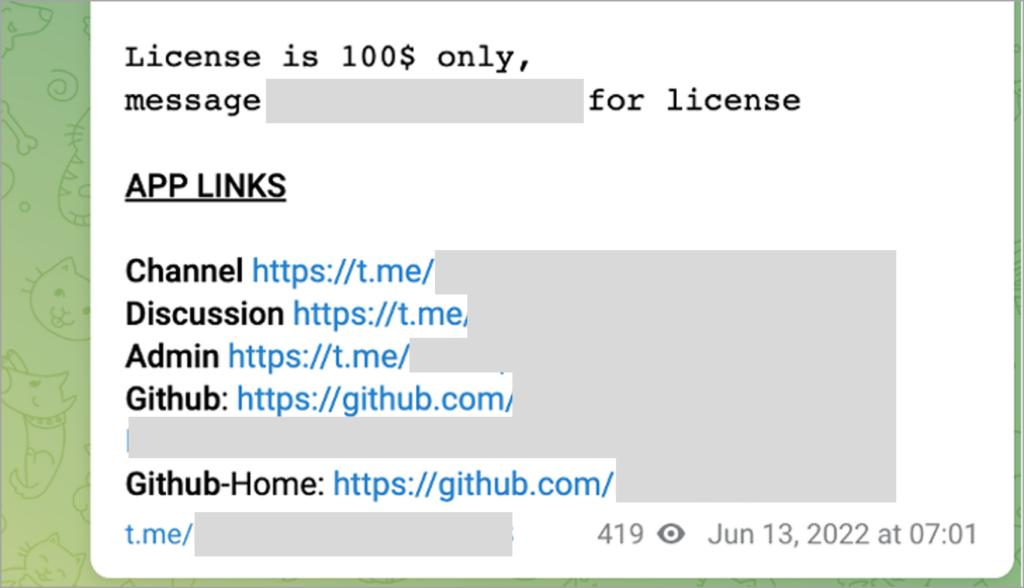
Adversary-in-the-middle (AiTM) phishing kits are part of an increasing trend that is observed supplanting many other less advanced forms of phishing. AiTM phishing is capable of circumventing multifactor authentication (MFA) through reverse-proxy functionality. DEV-1101 is an actor tracked by Microsoft responsible for the development, support, and advertising of[…]
Read MoreWomen’s History Month is a special time for me as I reflect on all the great innovations women have made over the years. Women have driven technology forward throughout history. Notable women in cybersecurity like cryptologists Agnes Meyer Driscoll and Genevieve Grotjan Feinstein worked behind the scenes of[…]
Read More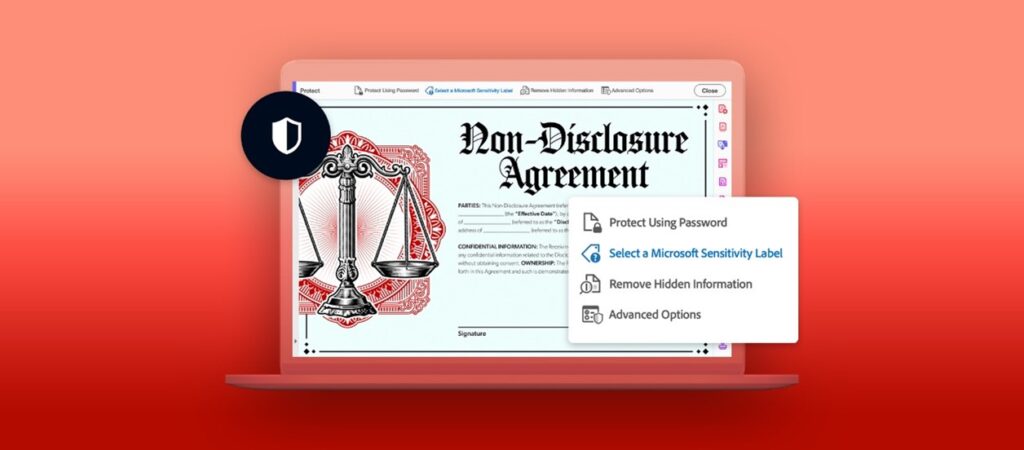
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Data security and compliance are a top priority for leaders as cyberattacks are on the rise. In fact, attacks have increased by 32 percent in the past year, and 1 in 40[…]
Read More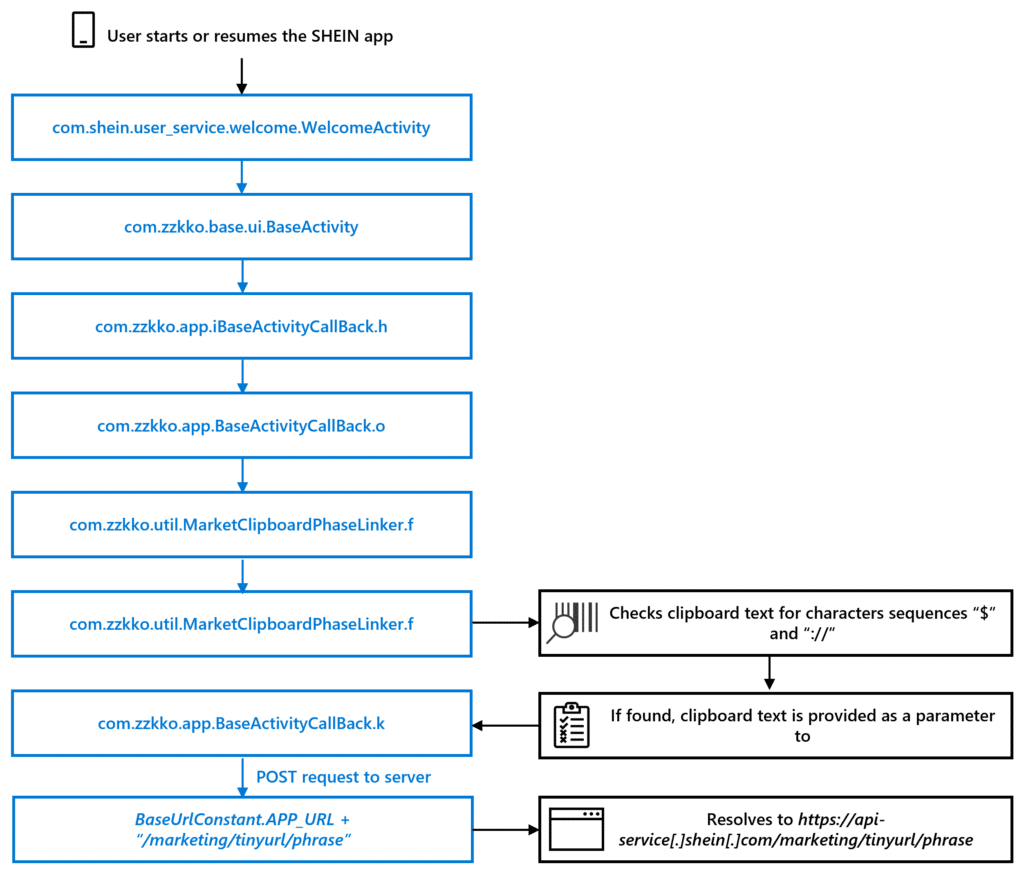
Considering mobile users often use the clipboard to copy and paste sensitive information, like passwords or payment information, clipboard contents can be an attractive target for cyberattacks. Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. Examples even exist of attackers hijacking and replacing[…]
Read More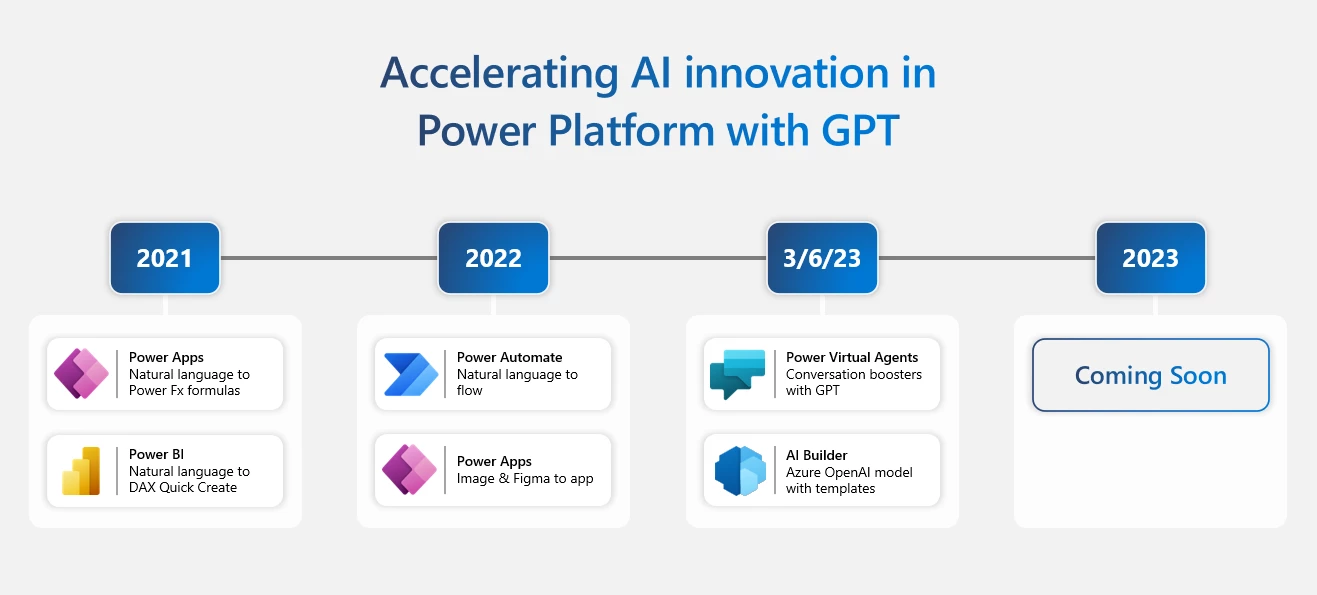
Low-code technology is radically changing the traditional development landscape. And with Microsoft Power Platform and next-generation AI, Microsoft is providing both a new way for developers to solve business problems and a new way for end users to use AI in the flow of their work to be[…]
Read More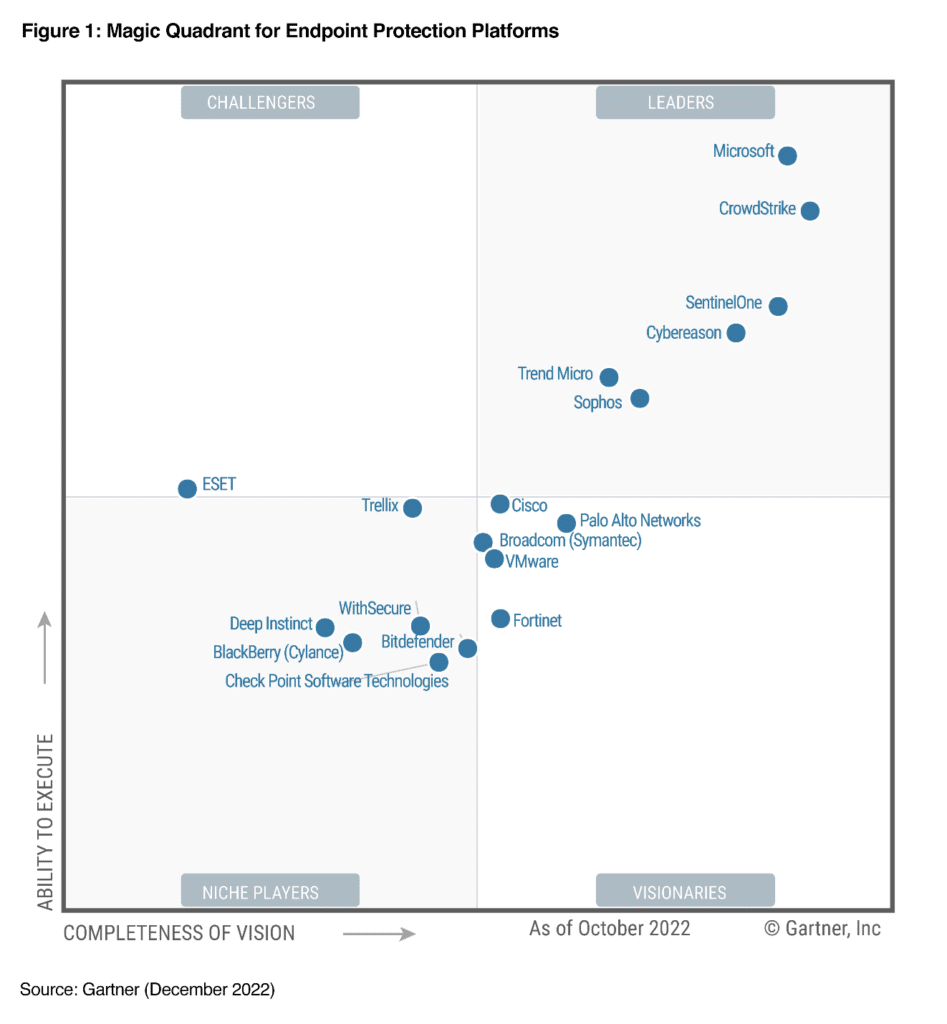
The state of cybersecurity continues to challenge defenders around the world. With hybrid work here to stay and emerging trends like Ransomware as a Service, organizations need a partner that empowers them with not only modern endpoint security but an integrated solution that helps security operations teams defend[…]
Read More