Let’s start with the bad news. Cybersecurity breaches can be particularly devastating for supply chains, which involve multiple parties and sensitive information. As operational technology (OT) devices become increasingly connected, blurring the gap between IT and OT environments, the risk of hackers targeting sensitive supply chain data increases.[…]
Read More
In the digital world, when you meet professional contacts for the first time online, you need additional trust signals to increase your confidence that they are who they say they are. We’re thrilled to announce that millions of LinkedIn members will be able to verify their place of[…]
Read More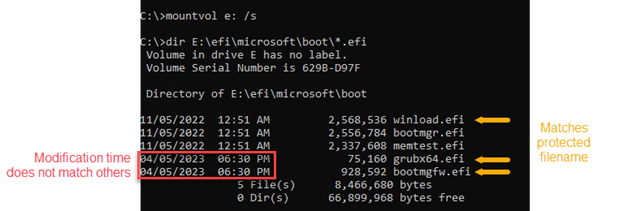
This guide provides steps that organizations can take to assess whether users have been targeted or compromised by threat actors exploiting CVE-2022-21894 via a Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus. UEFI bootkits are particularly dangerous as they run at computer startup, prior to the operating system[…]
Read MoreMicrosoft Threat Intelligence analysts assess with high confidence that a threat group tracked by Microsoft as DEV-0196 is linked to an Israel-based private sector offensive actor (PSOA) known as QuaDream. QuaDream reportedly sells a platform they call REIGN to governments for law enforcement purposes. REIGN is a suite[…]
Read More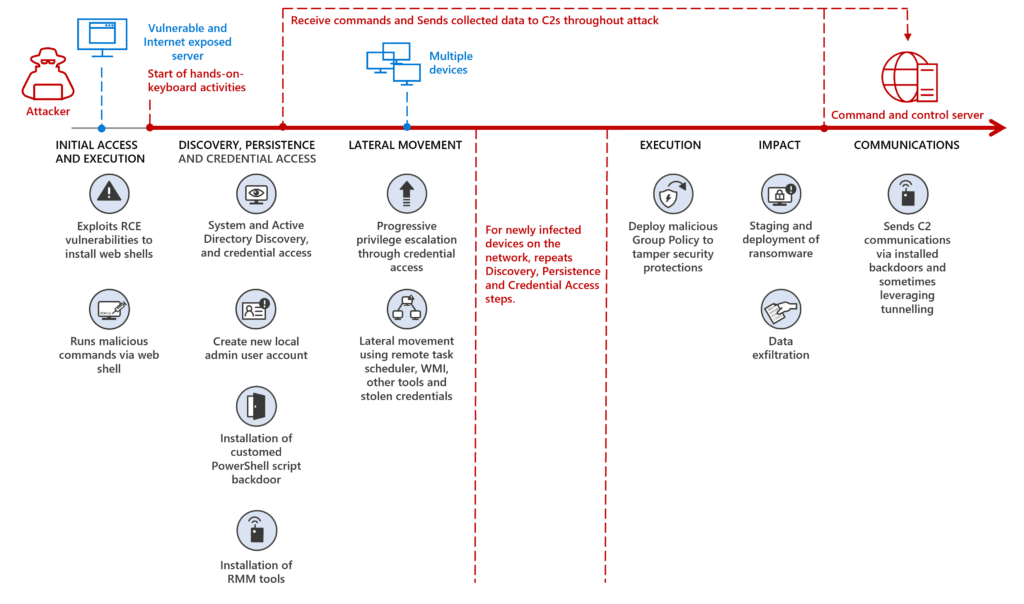
Microsoft Threat Intelligence has detected destructive operations enabled by MERCURY, a nation-state actor linked to the Iranian government, that attacked both on-premises and cloud environments. While the threat actors attempted to masquerade the activity as a standard ransomware campaign, the unrecoverable actions show destruction and disruption were the[…]
Read More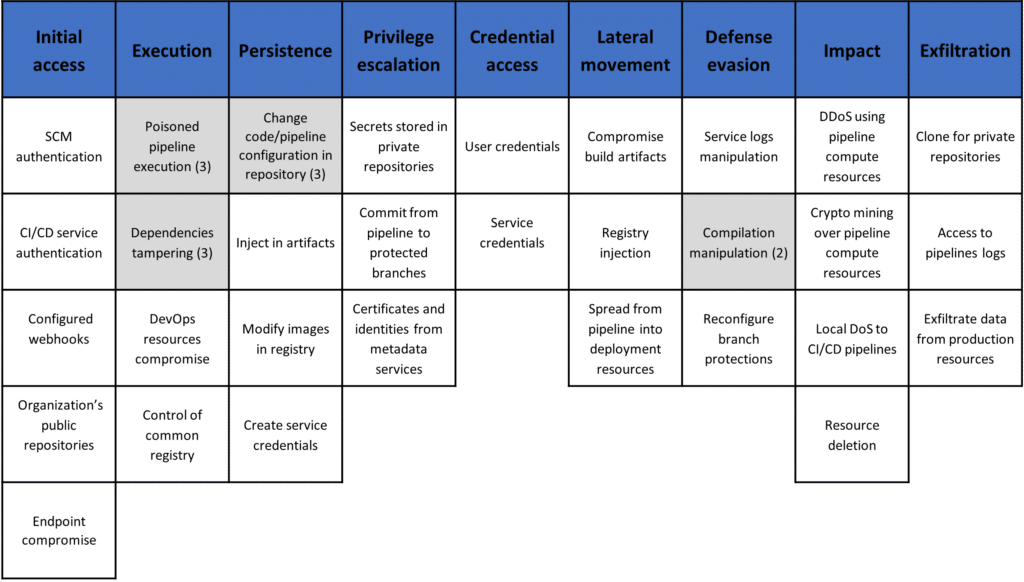
The use of DevOps practices, which enable organizations to deliver software more quickly and efficiently, has been on the rise. This agile approach minimizes the time-to-market of new features and bug fixes. More and more companies are implementing DevOps services, each with its own infrastructure and emphasis on[…]
Read More
Productivity and innovation have become critical goals in many hybrid and remote work environments. Ensuring preventative and strong security, in turn, must be at the heart of that. In this blog series, we’ll discuss two Zero Trust business scenarios: enabling a more productive hybrid or remote work environment[…]
Read MoreThe post Release wave 1 expands agility, automation, and innovation across Microsoft Dynamics 365 and Power Platform appeared first on Microsoft Power Platform Blog. Source: Microsoft Power Platform
Read More
We’re thrilled to participate and connect with you at RSA Conference 2023 from April 23 to 27, 2023, in San Francisco. Join your security peers as we welcome you to the new era of security—shaped by the power of OpenAI’s GPT-4 generative AI—and introduce to you the recently[…]
Read MoreIf you read behind the attention-grabbing headlines, most novel techniques rely on compromised identities.1 In fact, of all the ways an attacker can get into your digital estate, identity compromise is still the most common.2 This makes identity your first line of defense. In many organizations, however, too[…]
Read More