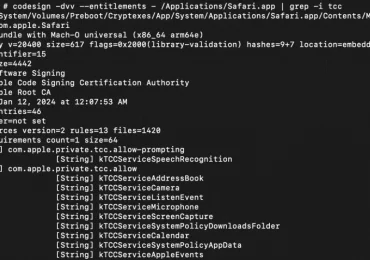
Microsoft Threat Intelligence uncovered a macOS vulnerability that could potentially allow an attacker to bypass the operating system’s Transparency, Consent,[…]
Leggi di più
Microsoft customers face more than 600 million cybercriminal and nation-state attacks every day, ranging from ransomware to phishing to identity[…]
Leggi di piùAs cyberthreats continue to evolve, it’s essential for security professionals to stay informed about the latest attack vectors and defense[…]
Leggi di piùAs cyberthreats continue to evolve, it’s essential for security professionals to stay informed about the latest attack vectors and defense[…]
Leggi di più
Introduction | Security snapshot | Threat briefingDefending against attacks | Expert profile Education is essentially an “industry of industries,” with[…]
Leggi di più
Introduction | Security snapshot | Threat briefingDefending against attacks | Expert profile Education is essentially an “industry of industries,” with[…]
Leggi di più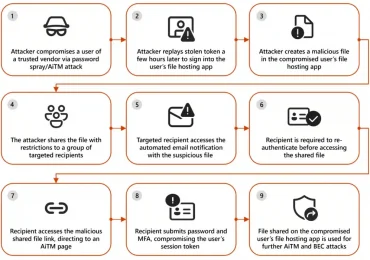
Microsoft has observed campaigns misusing legitimate file hosting services increasingly use defense evasion tactics involving files with restricted access and[…]
Leggi di più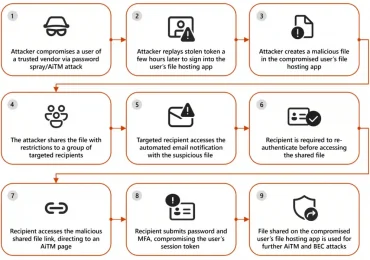
Microsoft has observed campaigns misusing legitimate file hosting services increasingly use defense evasion tactics involving files with restricted access and[…]
Leggi di più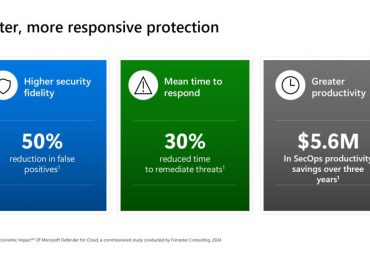
The broad adoption of multicloud and hybrid infrastructures has introduced new complexity to the cloud estates of many businesses. With[…]
Leggi di più
As Cybersecurity Awareness Month marks its 21st year, it’s clear that this year stands out. Phishing emails have become more[…]
Leggi di più
Microsoft has observed the threat actor tracked as Storm-0501 launching a multi-staged attack where they compromised hybrid cloud environments and[…]
Leggi di più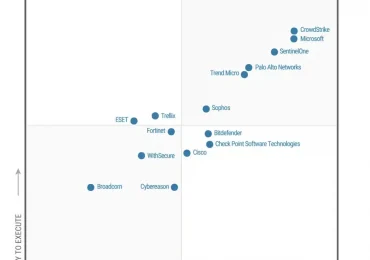
Since 2023, Microsoft has seen a 2.75 times increase in the number of organizations encountering ransomware campaigns.1 And up to[…]
Leggi di più