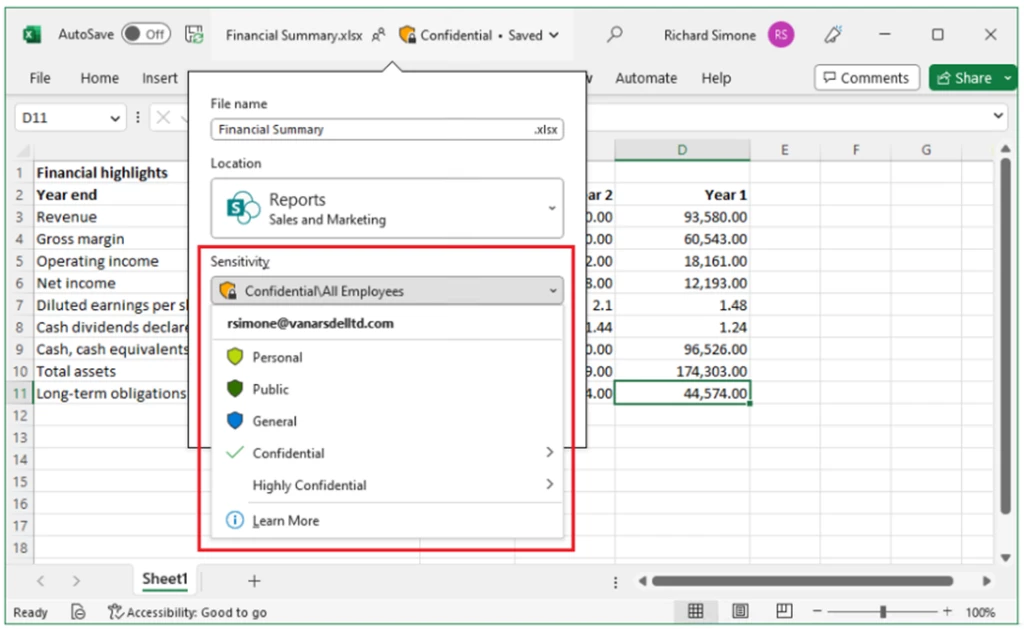
I recently worked with an enterprise customer who experienced a data exfiltration attack using the characteristics of the BazaCall campaign. BazaCall can be both a ransomware and data exfiltration attack that are used together to increase pressure on and damage to the victim. Microsoft Purview has data security[…]
Read More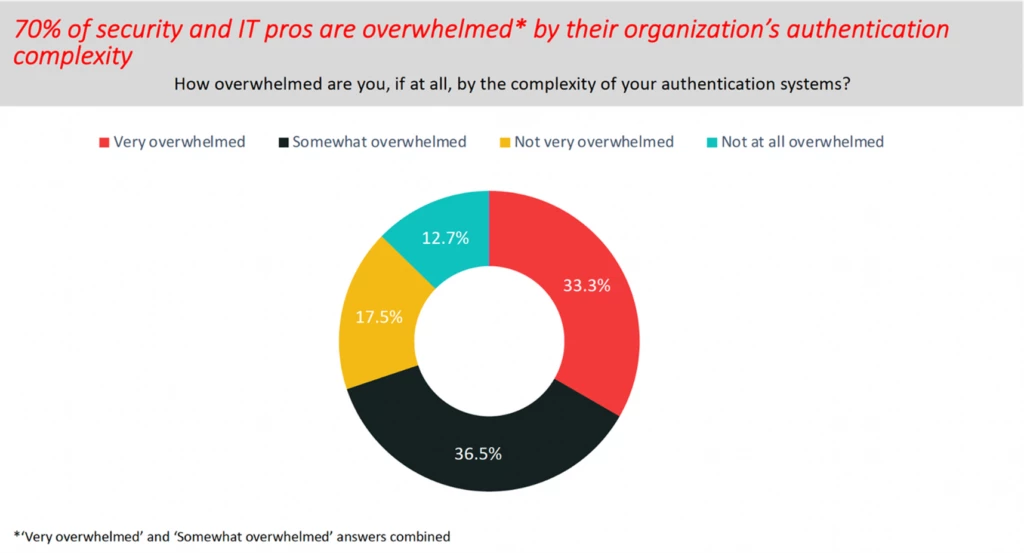
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Passwords are a security weakness and phishing attacks to exploit accounts protected by passwords are on the rise. The last 12 months have seen an average of more than 4,000 password attacks[…]
Read More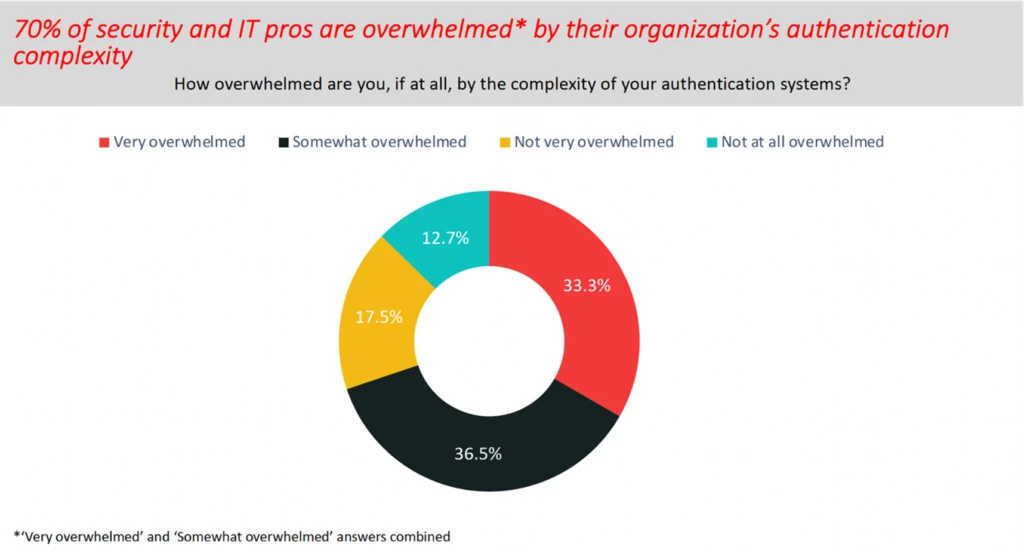
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Passwords are a security weakness and phishing attacks to exploit accounts protected by passwords are on the rise. The last 12 months have seen an average of more than 4,000 password attacks[…]
Read MoreThe recently published United States National Cybersecurity Strategy warns that many popular Internet of Things (IoT) devices are not sufficiently secure to protect against many of today’s common cybersecurity threats.1 The strategy also cautions that many of these IoT devices are difficult—or, in some cases, impossible—to patch or[…]
Read More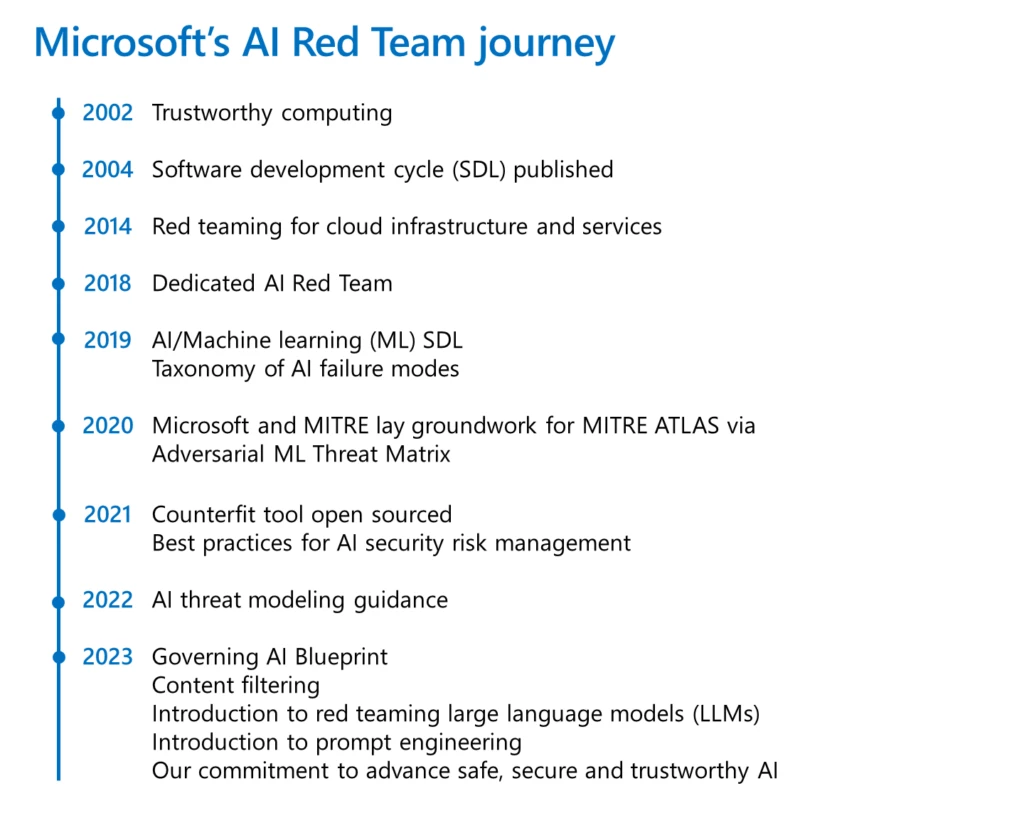
An essential part of shipping software securely is red teaming. It broadly refers to the practice of emulating real-world adversaries and their tools, tactics, and procedures to identify risks, uncover blind spots, validate assumptions, and improve the overall security posture of systems. Microsoft has a rich history of[…]
Read More
Today we released the fifth edition of Cyber Signals, spotlighting threats to large venues, and sporting and entertainment events, based on our learnings and telemetry from delivering cybersecurity support to critical infrastructure facilities during the State of Qatar’s hosting of the FIFA World Cup 2022™. Cybersecurity threats to[…]
Read More
Microsoft Threat Intelligence has identified highly targeted social engineering attacks using credential theft phishing lures sent as Microsoft Teams chats by the threat actor that Microsoft tracks as Midnight Blizzard (previously tracked as NOBELIUM). This latest attack, combined with past activity, further demonstrates Midnight Blizzard’s ongoing execution of[…]
Read More
In the ever-evolving world of cybersecurity, email remains a primary attack vector for cybercriminals, making effective email protection a foundational piece of any organization’s security strategy. In Q1 2023, Microsoft was once again part of an evaluation of email security platforms conducted by SE Labs. SE Labs has[…]
Read More
Now in its twenty-sixth year, Black Hat USA takes place August 5 to 10, 2023, at Mandalay Bay in Las Vegas, Nevada, bringing together security professionals for the latest in information security research, development, and trends. Microsoft Security is pleased to have a presence at Black Hat, with[…]
Read More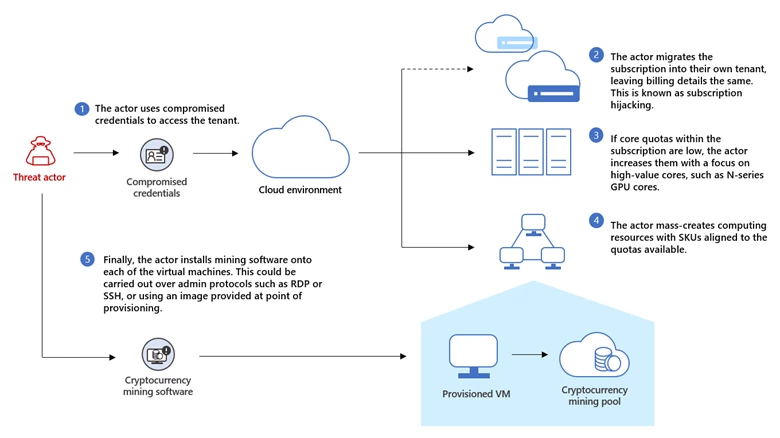
In cloud environments, cryptojacking – a type of cyberattack that uses computing power to mine cryptocurrency – takes the form of cloud compute resource abuse, which involves a threat actor compromising legitimate tenants. Cloud compute resource abuse could result in financial loss to targeted organizations due to the[…]
Read More