
Microsoft Power Platform recently commissioned a Forrester Total Economic Impact study to help customers better understand the value of Microsoft Power Platform premium capabilities. This study expounds on how premium capabilities empower enterprises to unlock more business value using the platform.The study accomplishes this by highlighting three key[…]
Read More
The Department of Defense (DoD) released its formal Zero Trust strategy today, marking a major milestone in its goal of achieving enterprise-wide implementation by 2027. The strategy comes at a critical time as United States government networks continue to face nearly half the global nation-state attacks that occur,[…]
Read More
Notebooks are gaining popularity in InfoSec. Used interactively for investigations and hunting or as scheduled processing jobs, notebooks offer plenty of advantages over traditional security operations center (SOC) tools. Sitting somewhere between scripting/macros and a full-blown development environment, they offer easy entry to data analyses and visualizations that[…]
Read More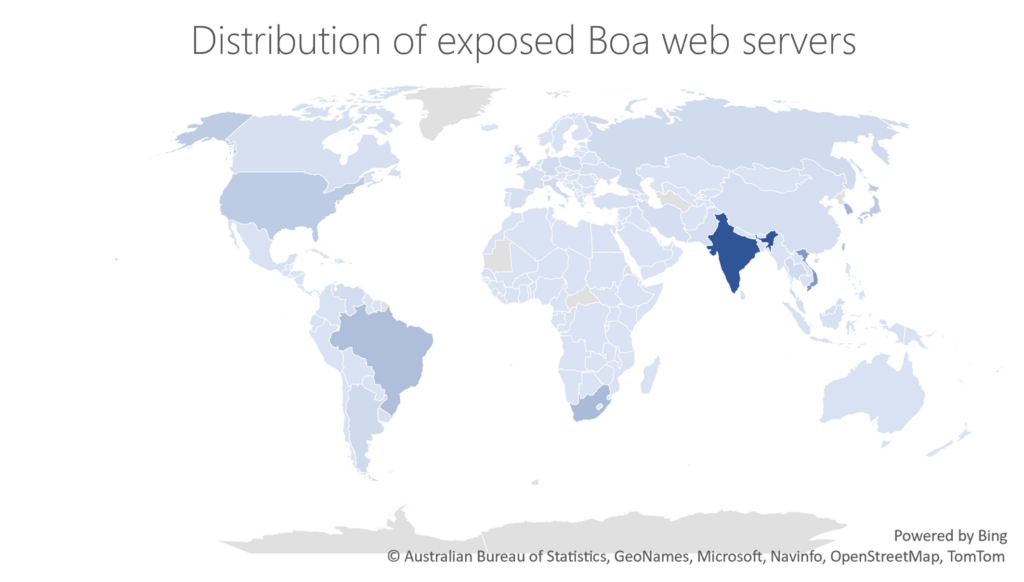
Vulnerabilities in network components, architecture files, and developer tools have become increasingly popular attack vectors to gain access into secure networks and devices. External tools and products that are managed by vendors and developers can pose a security risk, especially to targets in sensitive industries. Attacks on software[…]
Read More
Recent activity from the threat actor that Microsoft tracks as DEV-0569, known to distribute various payloads, has led to the deployment of the Royal ransomware, which first emerged in September 2022 and is being distributed by multiple threat actors. Observed DEV-0569 attacks show a pattern of continuous innovation,[…]
Read More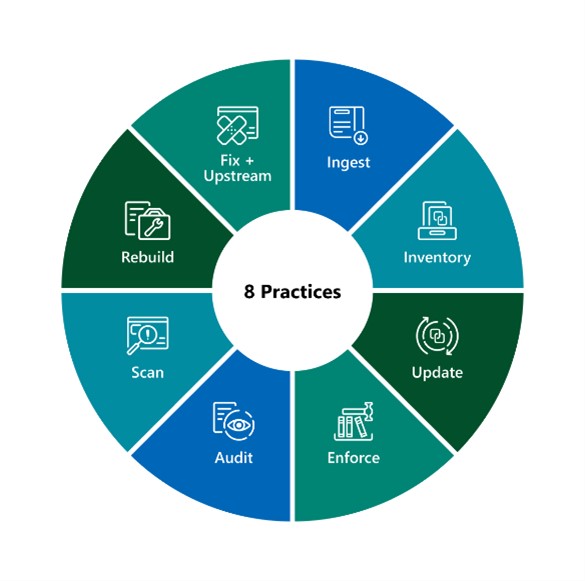
On August 4, 2022, Microsoft publicly shared a framework that it has been using to secure its own development practices since 2019, the Secure Supply Chain Consumption Framework (S2C2F), previously the Open Source Software-Supply Chain Security (OSS-SSC) Framework. As a massive consumer of and contributor to open source,[…]
Read More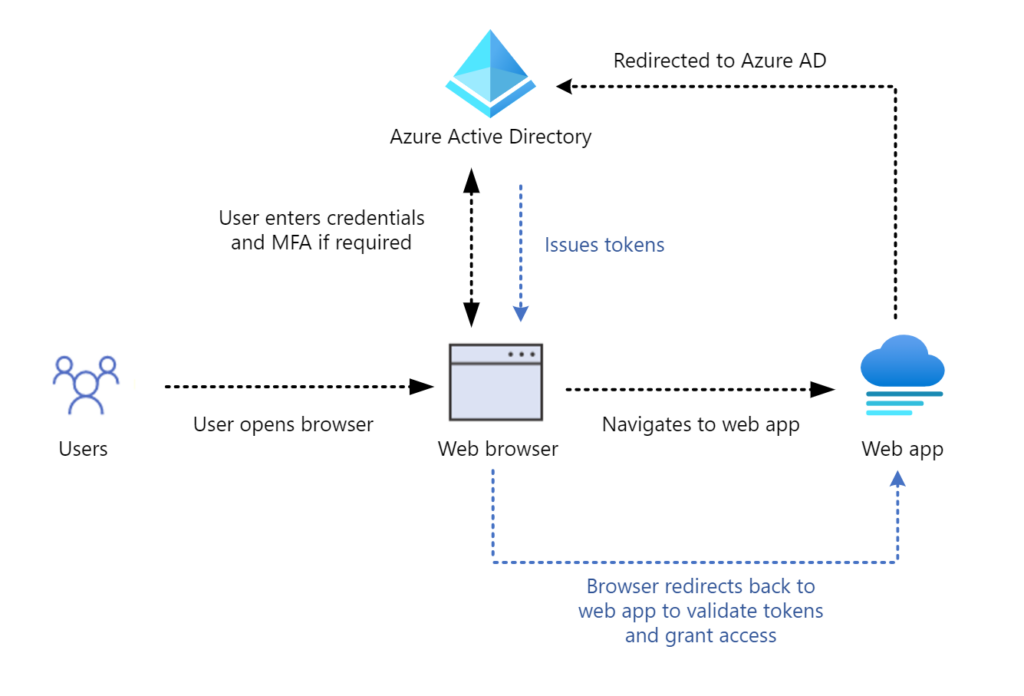
As organizations increase their coverage of multifactor authentication (MFA), threat actors have begun to move to more sophisticated techniques to allow them to compromise corporate resources without needing to satisfy MFA. Recently, the Microsoft Detection and Response Team (DART) has seen an increase in attackers utilizing token theft[…]
Read More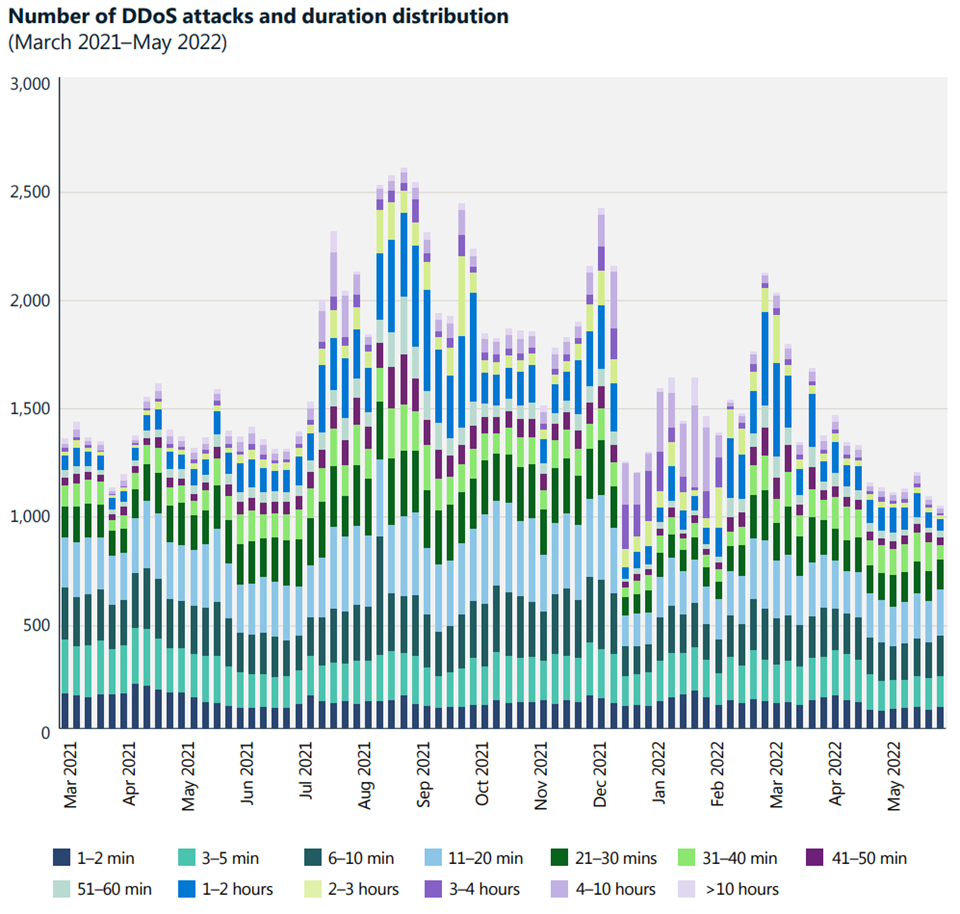
The holiday season is an exciting time for many people as they get to relax, connect with friends and family, and celebrate traditions. Organizations also have much to rejoice about during the holidays (for example, more sales for retailers and more players for gaming companies). Unfortunately, cyber attackers[…]
Read More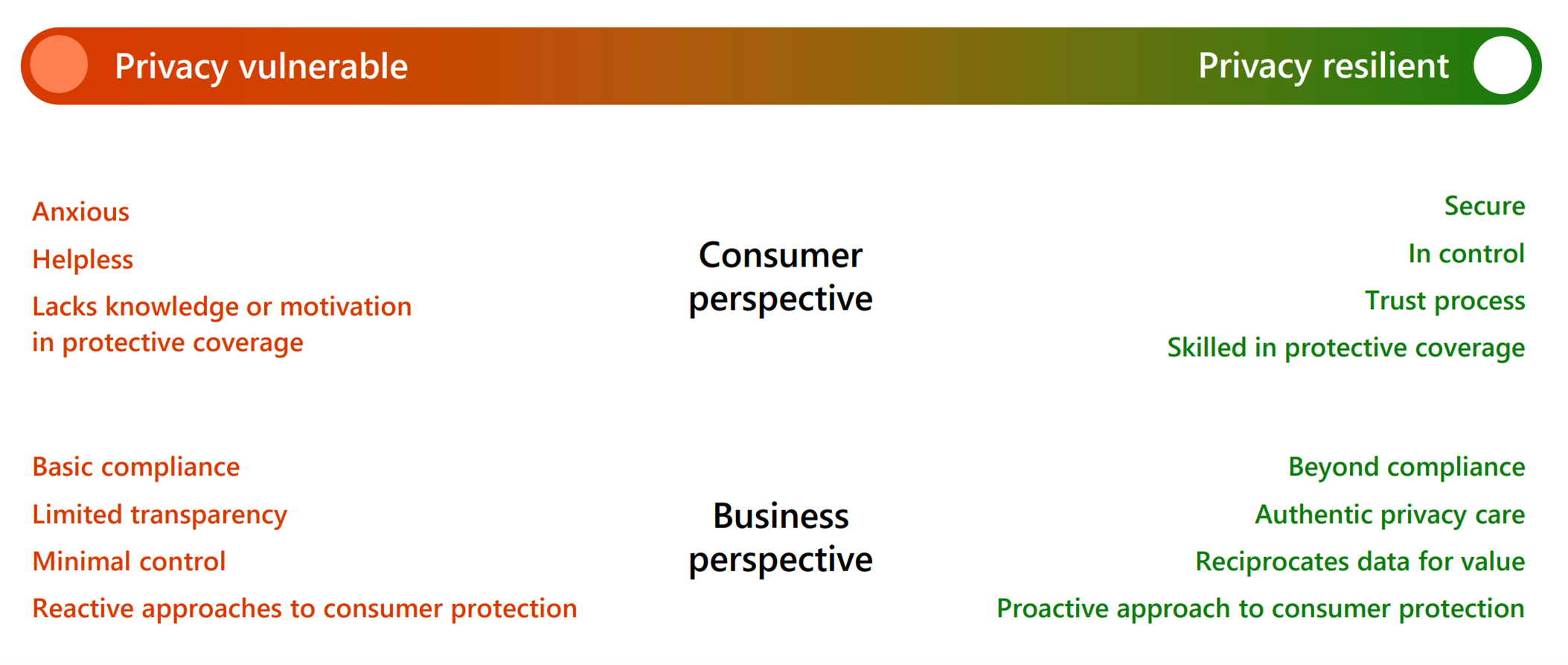
The General Data Protection Regulation (GDPR) came into effect in 2018 and set a new standard for the level of control individuals in the European Union had on the personal data they shared online. Since then, the number of privacy regulations around the world has flourished and impacted[…]
Read More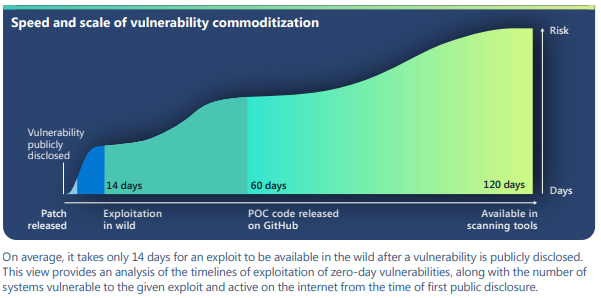
At CyberWarCon 2022, Microsoft and LinkedIn analysts presented several sessions detailing analysis across multiple sets of actors and related activity. This blog is intended to summarize the content of the research covered in these presentations and demonstrates Microsoft Threat Intelligence Center’s (MSTIC) ongoing efforts to track threat actors,[…]
Read More