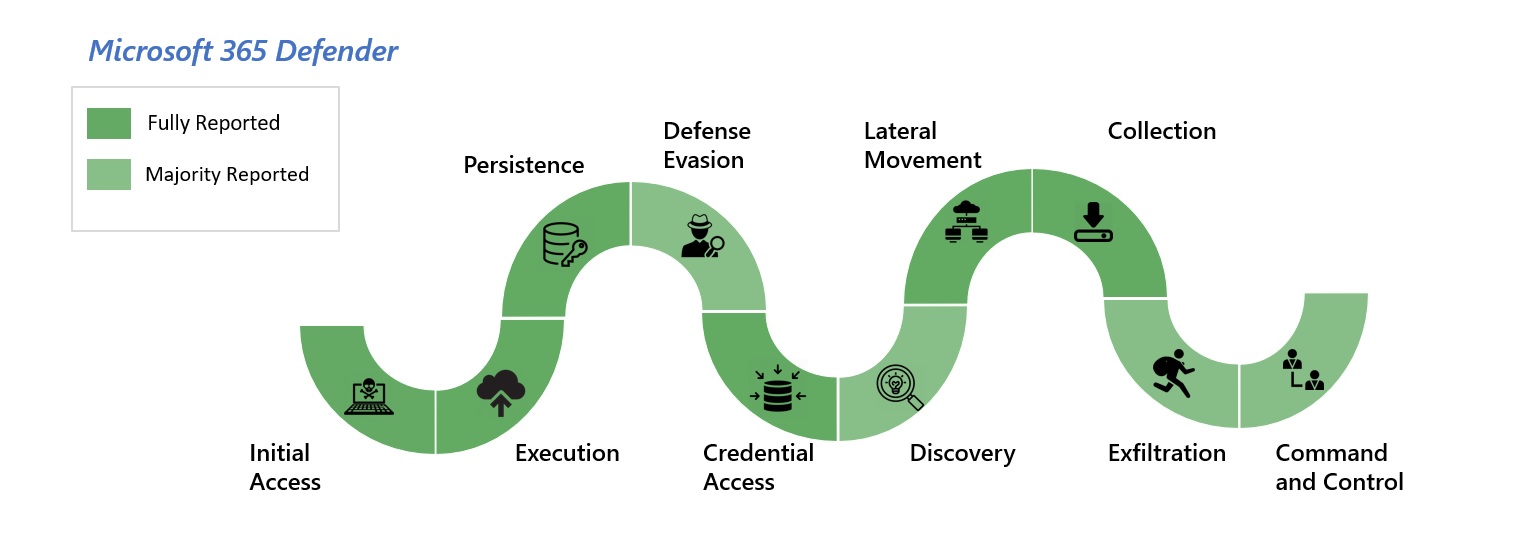
Microsoft Defender Experts for Hunting, our newest managed threat hunting service, delivered industry-leading results during the inaugural MITRE Engenuity ATT&CK® Evaluations for Managed Services. We provided a seamless, comprehensive, and rapid response to the simulated attack using expert-led threat hunting and an industry-leading extended detection and response (XDR)[…]
Read More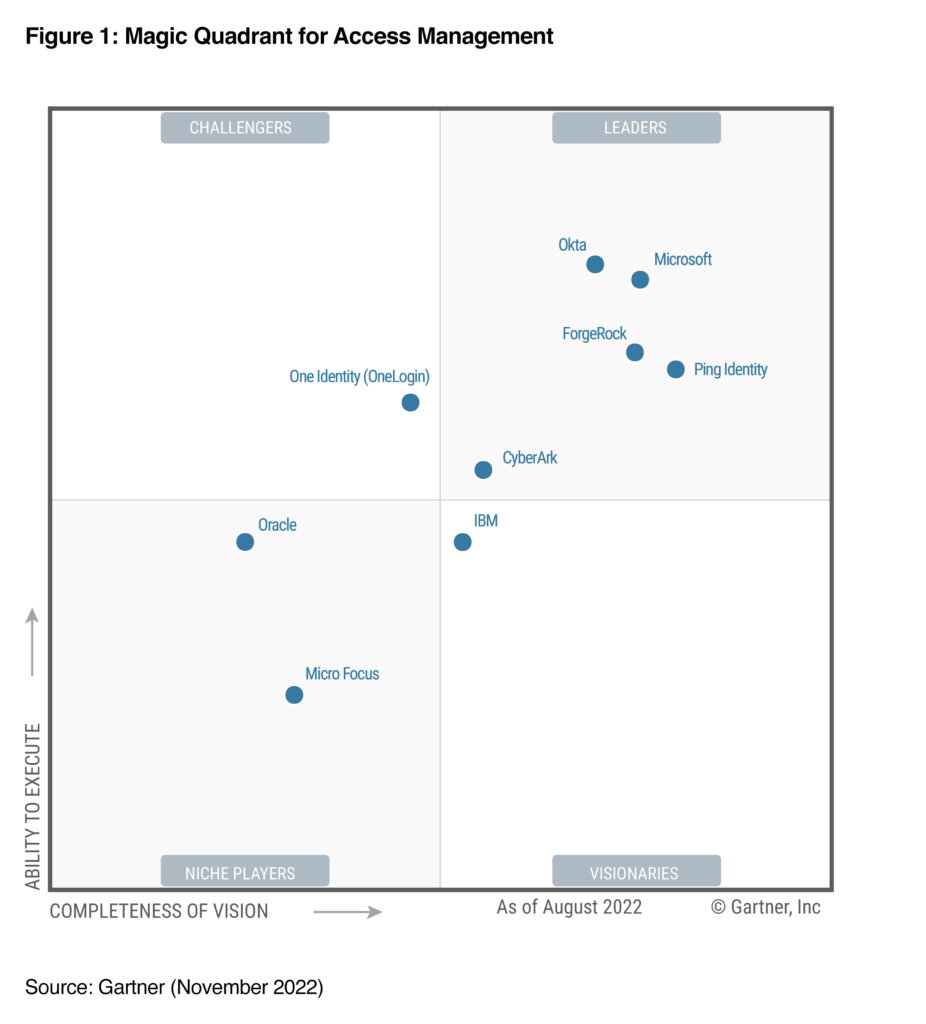
We are honored to announce that Microsoft has been named a Leader in the 2022 Gartner® Magic QuadrantTM for Access Management for Microsoft Azure Active Directory (Azure AD), part of Microsoft Entra. We thank our customers who guide our strategy and product innovation, engage with us deeply in[…]
Read More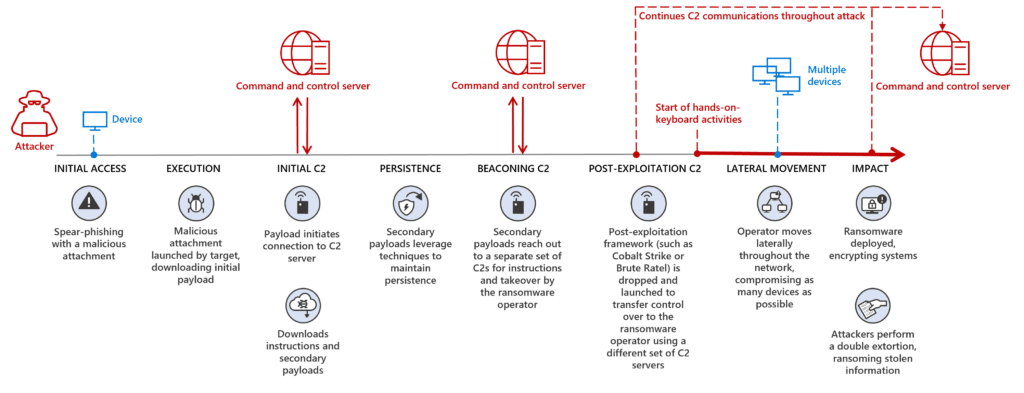
Command-and-control (C2) servers are an essential part of ransomware, commodity, and nation-state attacks. They are used to control infected devices and perform malicious activities like downloading and launching payloads, controlling botnets, or commanding post-exploitation penetration frameworks to breach an organization as part of a ransomware attack. Blocking these[…]
Read MoreThe security community is continuously changing, growing, and learning from each other to better position the world against cyberthreats. In the latest post of our Community Voices blog series, Microsoft Security Senior Product Marketing Manager Brooke Lynn Weenig talks with Matthew Hickey, Co-founder, Chief Executive Officer (CEO), and hacker of Hacker House. The thoughts below[…]
Read More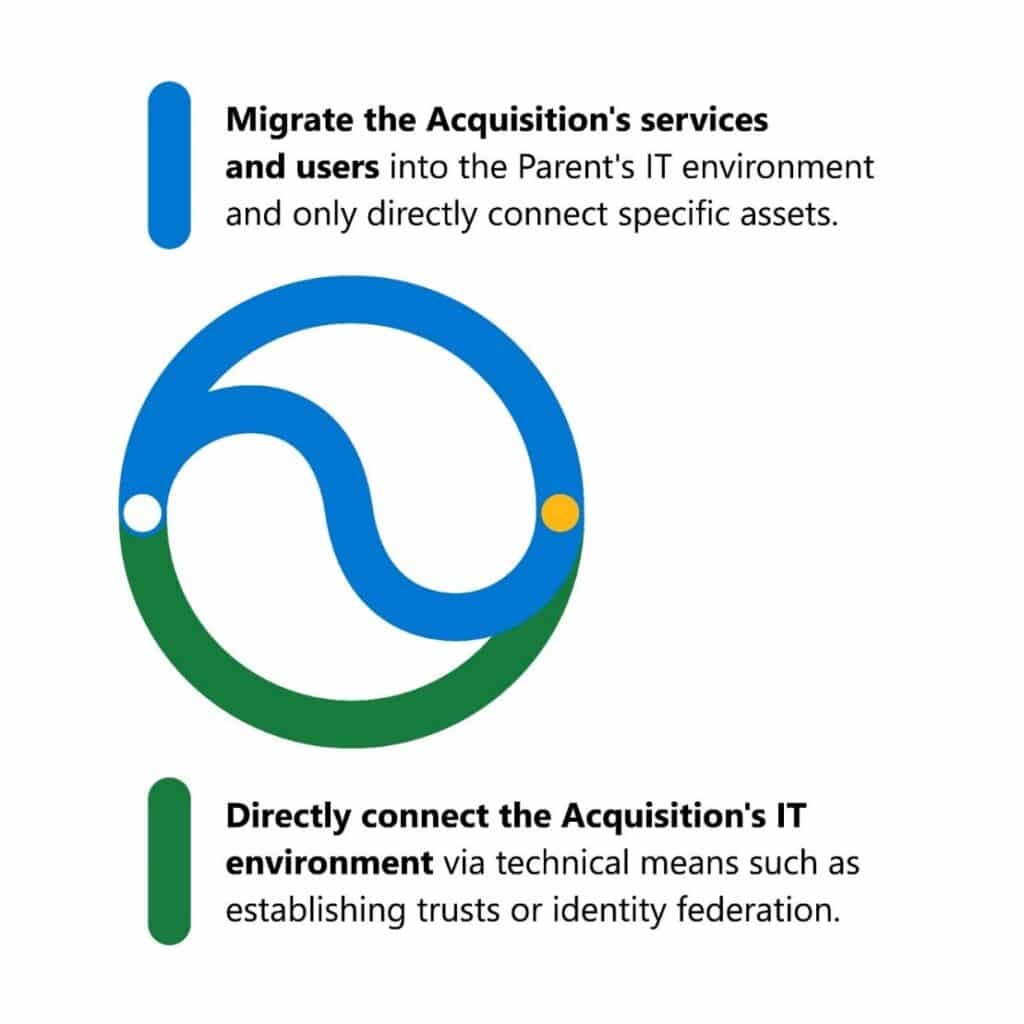
Sixty-two percent of organizations that undertake mergers and acquisitions face significant cybersecurity risks or consider cyber risks their biggest concern post-acquisition.1 Threat actors that focus on corporate espionage often target the acquiring company, which we will refer to as the Parent, early in the bidding process to gain[…]
Read MoreThroughout Cybersecurity Awareness Month, Microsoft has highlighted the importance of cybersecurity and provided resources to help people and organizations stay safe. It’s great to have this month as a reminder, and even better if that awareness becomes a year-round endeavor. Education is really the key. With the increase[…]
Read More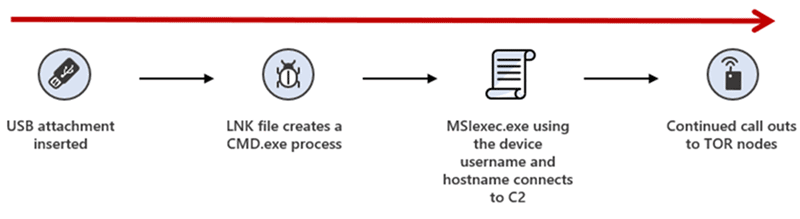
Microsoft has discovered recent activity indicating that the Raspberry Robin worm is part of a complex and interconnected malware ecosystem, with links to other malware families and alternate infection methods beyond its original USB drive spread. These infections lead to follow-on hands-on-keyboard attacks and human-operated ransomware activity. Our[…]
Read MoreAs part of the Bipartisan Infrastructure Law, also known as the Infrastructure Investment and Jobs Act of 2021, the United States federal government announced a cybersecurity grant program for state, local, territorial, and tribal (SLTT) governments to fund allocation of USD1 billion over the next four years for[…]
Read MoreToday, many companies face global supply chain challenges. From unexpected demand to ever-increasing fulfillment expectations, the stakes have never been higher. In response, some are looking for new strategies and solutions to help them quickly predict and overcome disruptionsto keep goods moving and their businesses profitable.The post Bring[…]
Read More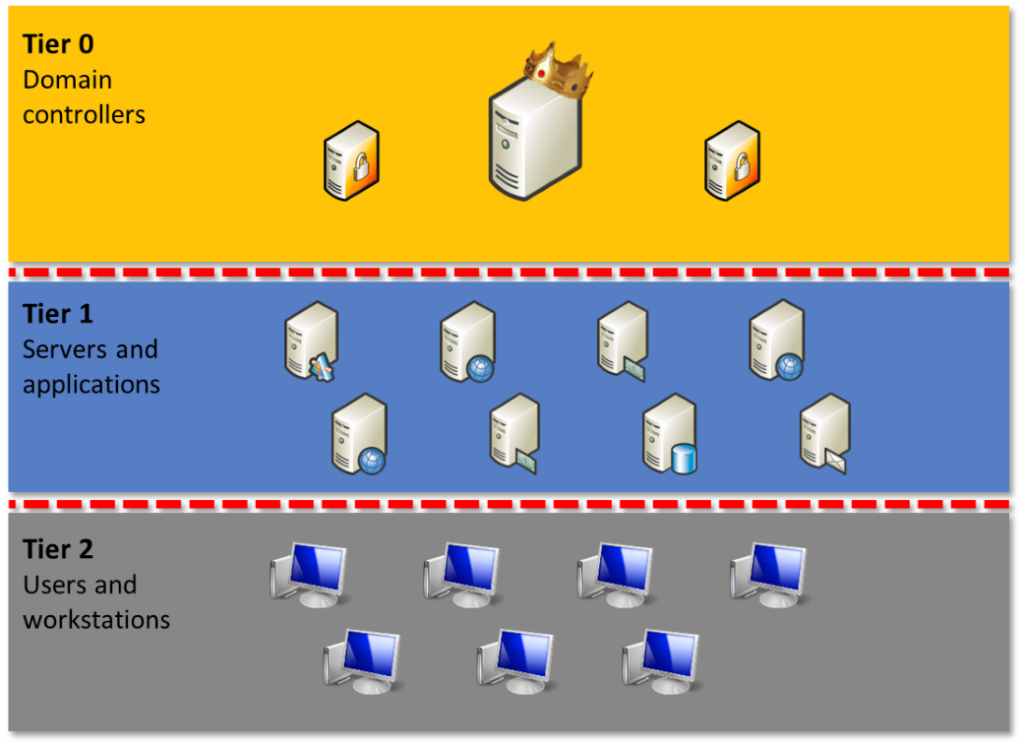
It’s been 10 years since the first version of the Mitigating Pass-the-Hash Attacks and Other Credential Theft whitepaper was made available, but the techniques are still relevant today, because they help prevent attackers from gaining a network foothold and using credential-dumping tools to extract password hashes, user credentials, or Kerberos[…]
Read More