At Microsoft Security, we understand how challenging it is to protect your most important asset, your data, in today’s threat landscape. You’re faced with evolving challenges—from empowering employees for greater productivity to eliminating gaps in your infrastructure—all while trying to protect your data across a hybrid work environment.[…]
Read More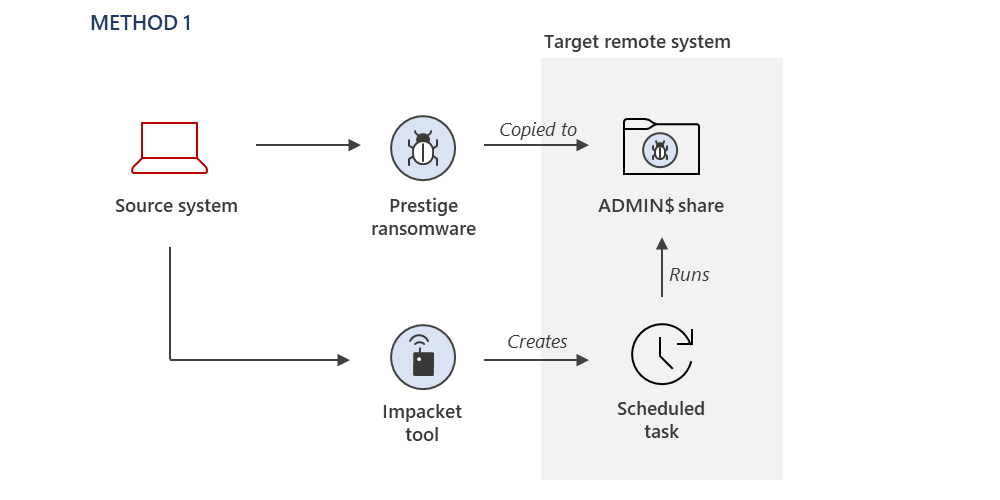
The Microsoft Threat Intelligence Center (MSTIC) has identified evidence of a novel ransomware campaign targeting organizations in the transportation and related logistics industries in Ukraine and Poland utilizing a previously unidentified ransomware payload. We observed this new ransomware, which labels itself in its ransom note as “Prestige ranusomeware”,[…]
Read More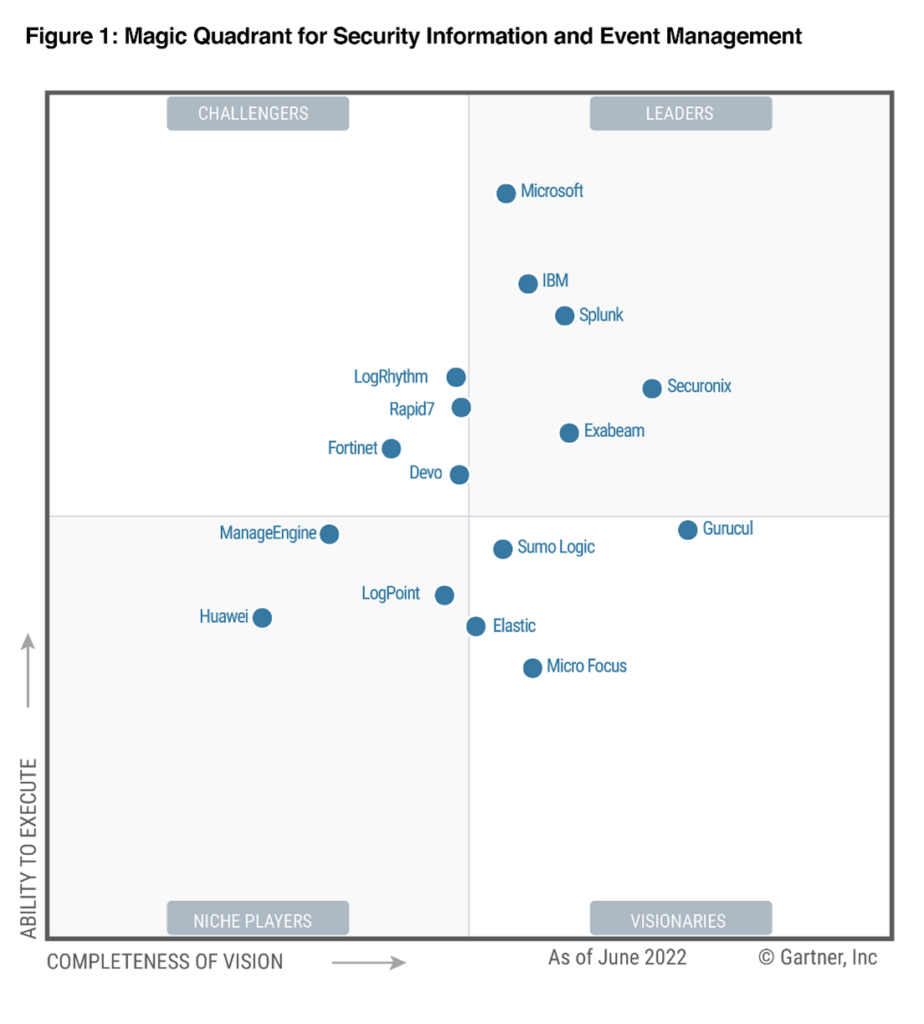
Security operations teams are overwhelmed trying to protect their organizations against an onslaught of cyberattacks, including a 92 percent rise in ransomware attacks.1 Too often, existing security tools are siloed or not designed to meet the needs of today’s hybrid cloud environment. The result is overworked security analysts,[…]
Read More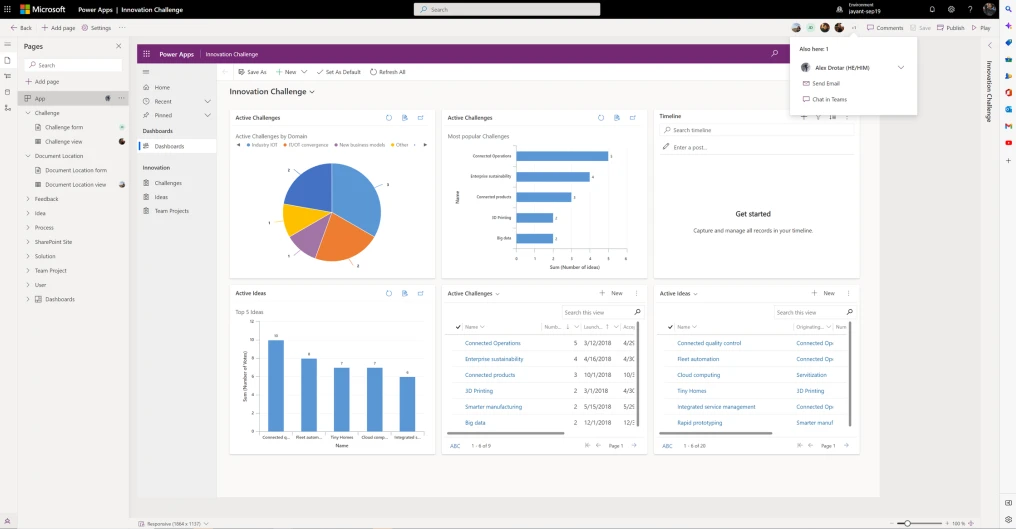
Welcome to Microsoft Ignite 2022! Microsoft Power Platform is empowering you to do more with less by making it easier than ever to securely scale low-code adoption, increase organizational collaboration, and infuse AI and automation into all of your business processes. The scope of chief information officers (CIOs), IT[…]
Read More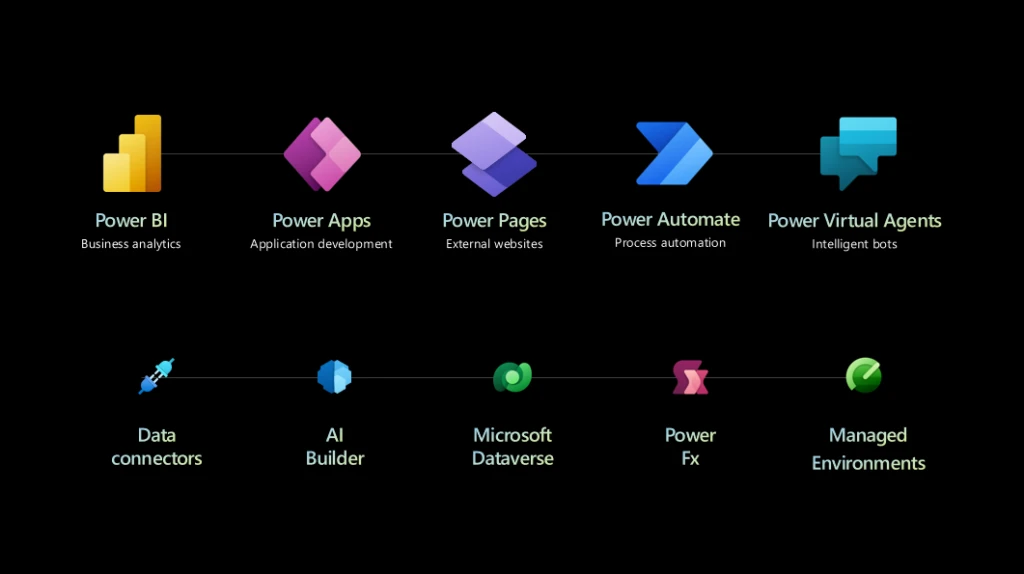
We are thrilled to announce the general availability of Managed Environments for Microsoft Power Platform, the progressive rollout of the enhancements started today and will continue over the coming weeks to all regions. In July of 2022, we announced the preview of Managed Environments and since then hundreds[…]
Read More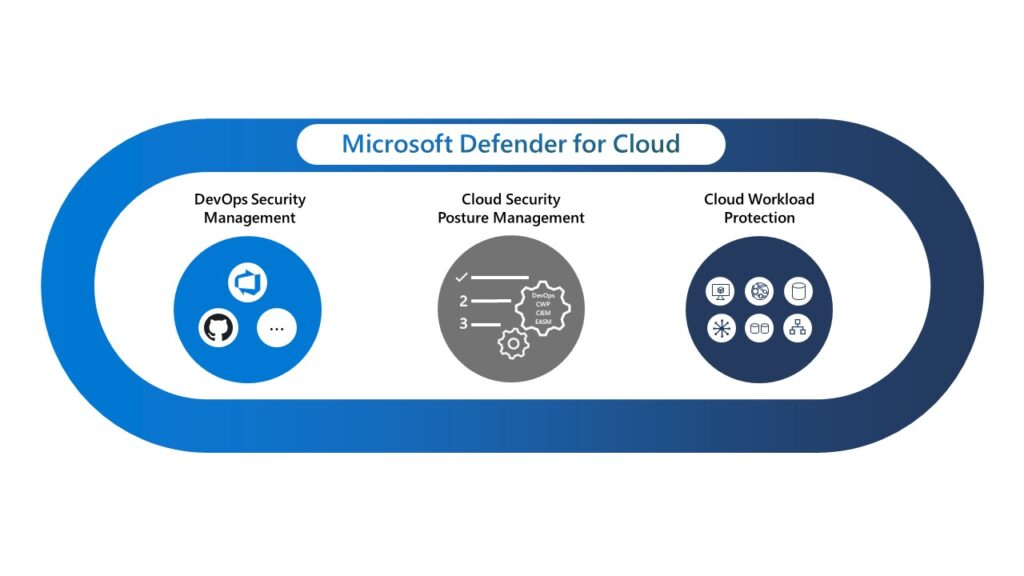
Security teams face an expanding attack surface as organizations increasingly use cloud-native services to develop, deploy, and manage applications across their multicloud and hybrid environments. Their challenge is compounded by incomplete visibility, siloed processes, and a lack of prioritized mitigations that put defenders into a position where they[…]
Read More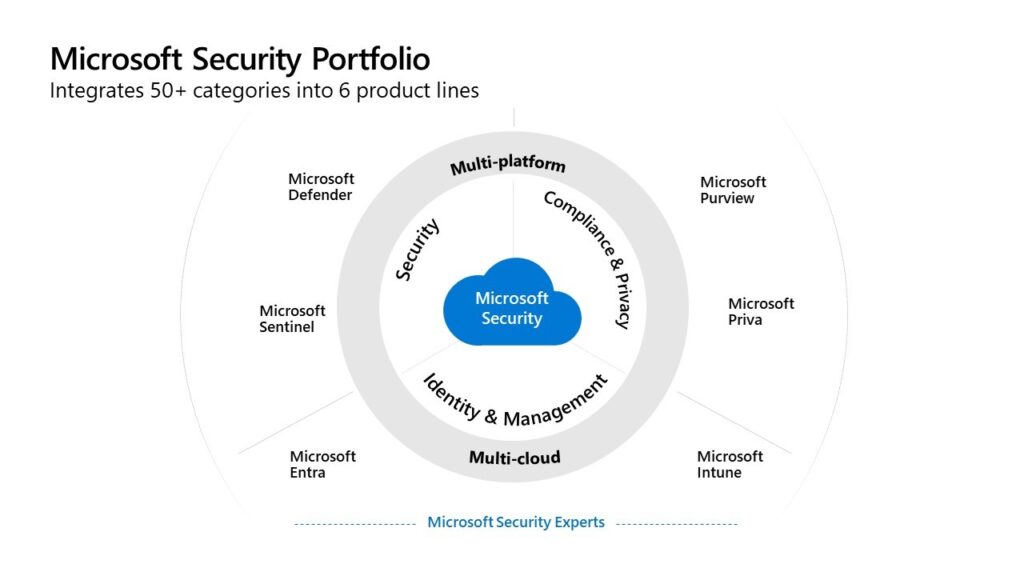
Protecting your business against growing security threats is a huge priority. Companies of all sizes have increased their spending on cybersecurity solutions to protect their operations over the last year. User spending for the information security and risk management market will grow to USD169.2 billion in 2022, with[…]
Read MoreThe risk landscape for organizations has changed significantly in the past few years. The amount of data captured, copied, and consumed is expected to grow to more than 180 zettabytes through 2025.1 Traditional ways of identifying and mitigating risks don’t always work. Historically, organizations have focused on external[…]
Read MoreMake the most of Microsoft Ignite! To help you do so for this three-day hybrid event, we have rounded up the must-see sessions and speakers for all things Microsoft Power Platform. There is a plethora of sessions designed to help IT professionals and makers across roles and skill[…]
Read More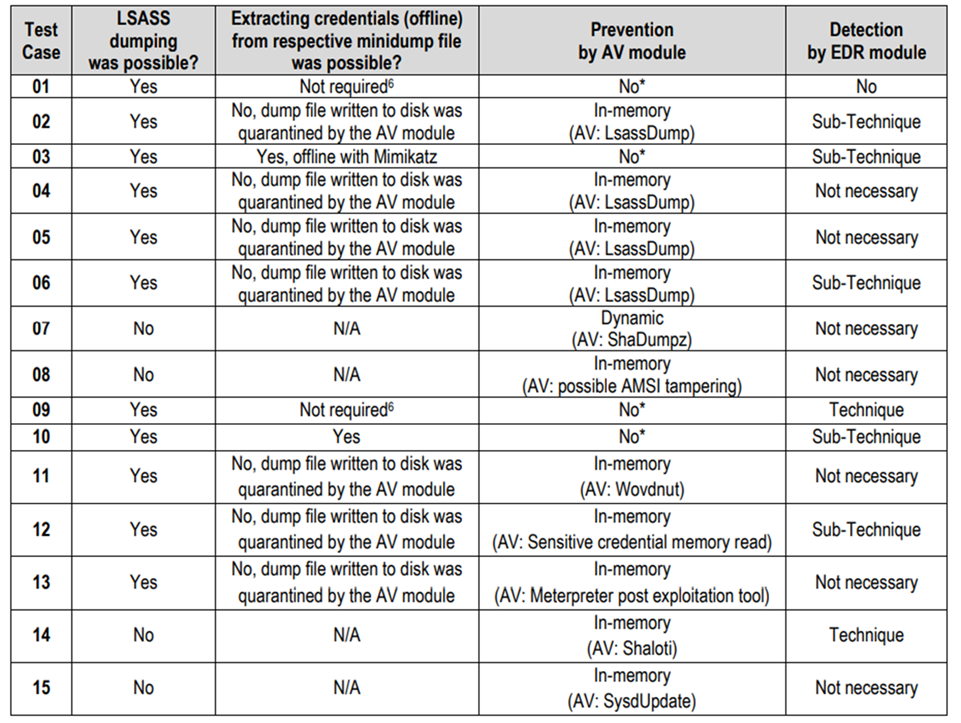
Obtaining user operating system (OS) credentials from a targeted device is among threat actors’ primary goals when launching attacks because these credentials serve as a gateway to various objectives they can achieve in their target organization’s environment, such as lateral movement. One technique attackers use is targeting credentials[…]
Read More