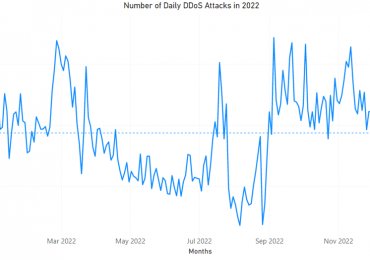
As organizations strengthen their defenses and take a more proactive approach to protection, attackers are adapting their techniques and increasing[…]
Leggi di più
In today’s world where hybrid and remote work are on the rise, and companies rely on email now more than[…]
Leggi di più
The security community is continuously changing, growing, and learning from each other to better position the world against cyberthreats. In the latest post of our Community[…]
Leggi di più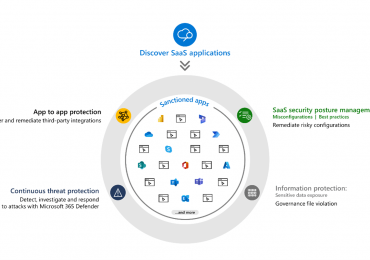
Software as a service (SaaS) apps are ubiquitous, hybrid work is the new normal, and protecting them and the important[…]
Leggi di più
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Cybersecurity is no longer[…]
Leggi di più
Maintaining security across today’s vast digital ecosystem is a team effort. AI and machine learning have helped to detect threats[…]
Leggi di piùOur story begins with eight Microsoft Detection and Response Team (DART) analysts gathered around a customer’s conference room to solve[…]
Leggi di più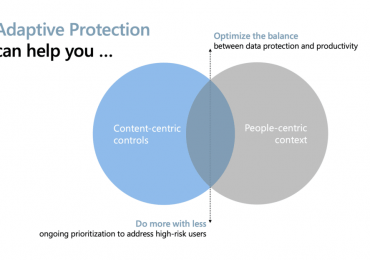
At Microsoft, we never stop working to protect you and your data. If the evolving cyberattacks over the past three[…]
Leggi di piùAgile and DevOps are without any doubt two of the biggest security trends of recent years. The rapid rise of[…]
Leggi di più
Welcome to 2023! I wanted to kick this year off by having a quick look at the trends in identity[…]
Leggi di più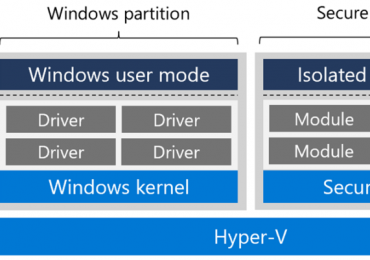
As part of Microsoft’s commitment to continuously raise security baselines, we have been introducing innovations to the foundation of the[…]
Leggi di più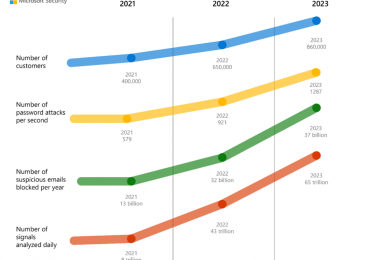
Yesterday, we shared some exciting news about the momentum we’re seeing in the security industry. Microsoft Chief Executive Officer Satya[…]
Leggi di più