Leading Through the Worst Day Incident response is never orderly. Threat actors don’t wait. Environments are compromised. Data is missing.[…]
Leggi di piùOn September 18, 2025, Fortra published a security advisory regarding a critical deserialization vulnerability in GoAnywhere MFT’s License Servlet, which[…]
Leggi di più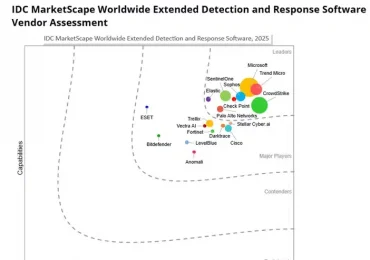
When cybersecurity stakes are high and complexity is the norm, Microsoft doesn’t just participate, it excels with Microsoft Defender XDR—built[…]
Leggi di più
At Microsoft, security is our number one priority, and we believe that cybersecurity is as much about people as it[…]
Leggi di più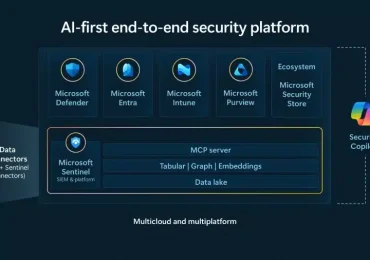
Microsoft unveils a new wave of security innovation—delivering an agentic platform to protect organizations at scale We are living through[…]
Leggi di piùWe’re excited to announce the general availability of Microsoft Power Pages in the regions of Singapore Local and South Africa. Whether you’re[…]
Leggi di più
A new breed of industry-leading company is taking shape — Frontier Firms. These organizations blend human ambition with AI-powered technology[…]
Leggi di più
Microsoft Threat Intelligence has identified yet another XCSSET variant in the wild that introduces further updates and new modules beyond[…]
Leggi di più
In the latest edition of our Cyberattack Series, we dive into real-world cases targeting retail organizations. With 60% of retail[…]
Leggi di piùMicrosoft Threat Intelligence recently detected and blocked a credential phishing campaign that likely used AI-generated code to obfuscate its payload[…]
Leggi di più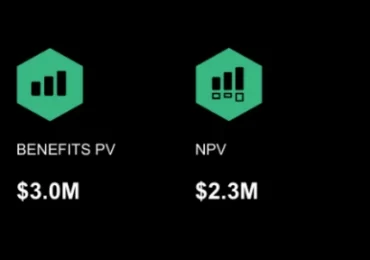
In today’s digital-first world, data is both an asset and a liability. As organizations scale their use of cloud platforms,[…]
Leggi di più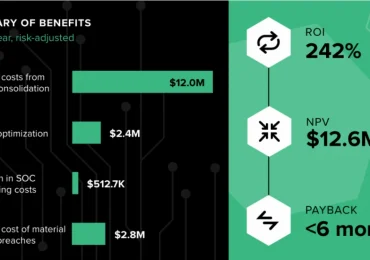
The latest Forrester Total Economic Impact™ (TEI) study reveals a 242% return on investment (ROI) over three years for organizations that chose Microsoft Defender.[…]
Leggi di più