
In today’s AI-powered world, security professionals are facing unprecedented challenges—and opportunities. As generative AI reshapes the digital landscape, the need[…]
Leggi di più
Founded more than 125 years ago, Dow has demonstrated a commitment to leveraging science to make the world a better[…]
Leggi di più
We are excited to share the latest developments in Customer Managed Key (CMK) management for Power Platform Environments. As data[…]
Leggi di piùEver had a critical app crash at the worst possible moment, or a vital flow suddenly stop sending emails? With Monitor,[…]
Leggi di piùDataverse Knowledge takes center stage in Microsoft Copilot Studio’s latest update—with support for multi-line text and file columns, plus improved[…]
Leggi di più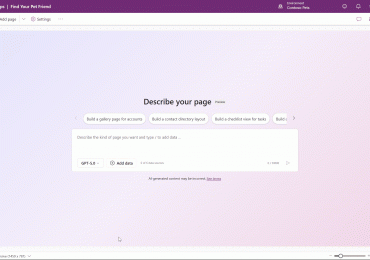
Generative pages aims to redefine how makers build with Microsoft Power Apps—bringing the power of vibe coding to enterprise development[…]
Leggi di più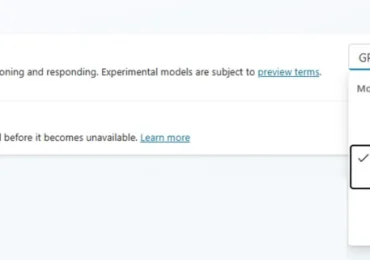
Starting today, Microsoft Copilot Studio users will have access to GPT-5, OpenAI’s best generative AI system that was introduced this[…]
Leggi di piùIntelligent triage for a more agile, autonomous SOCAt Microsoft Secure 2025, we introduced a new wave of innovations across Microsoft[…]
Leggi di più
We’re proud to share that Microsoft has again been named a Leader in the 2025 Gartner® Magic Quadrant™ for Enterprise[…]
Leggi di più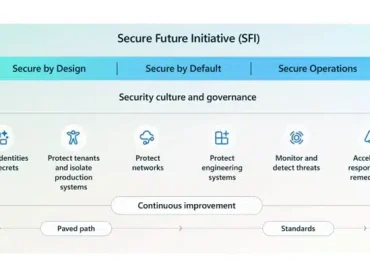
We’re excited to launch Microsoft Secure Future Initiative (SFI) patterns and practices: a new library of actionable guidance designed to[…]
Leggi di piùDefender Experts now offers 24/7, expert-driven protection for cloud workloads, beginning with hybrid and multicloud servers in Microsoft Defender for[…]
Leggi di più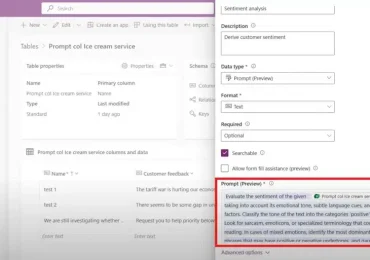
Microsoft Dataverse continues to evolve as a foundational platform for building intelligent, secure, and scalable business solutions. We are excited[…]
Leggi di più