Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- 80% of Fortune 500 use active AI Agents: Observability, governance, and security shape the new frontier 10 Febbraio 2026
- Manipulating AI memory for profit: The rise of AI Recommendation Poisoning 10 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- A one-prompt attack that breaks LLM safety alignment 9 Febbraio 2026
- Analysis of active exploitation of SolarWinds Web Help Desk 7 Febbraio 2026
Modernize your identity defense with Microsoft Identity Threat Detection and Response
In today’s fast-evolving landscape, where businesses balance on-premises systems and cloud resources, identity-based cyberthreats are growing more frequent and sophisticated. The question isn’t whether an identity attack will occur—but when. The numbers are staggering: In 2024 Microsoft saw an average of more than 7,000 password attacks happen per second and a 146% increase in adversary-in-the-middle (AiTM) phishing attacks alone.1
A unified approach to identity threat detection and response (ITDR) is no longer a luxury; it’s a necessity. Whether you are an identity admin or a security operations center (SOC) analyst, minimizing your risk starts with eliminating gaps in protection.
From chaos to control: Uniting identity and security solutions
As the corporate IT landscape has evolved organizations have been left managing complex webs of identities across multiple environments, tools, and vendors, giving cyber criminals many potential gaps to sneak through. The recent Secure Access Report illustrates the direct correlation between complex, multisolution identity vendors and the probability of a significant breach.
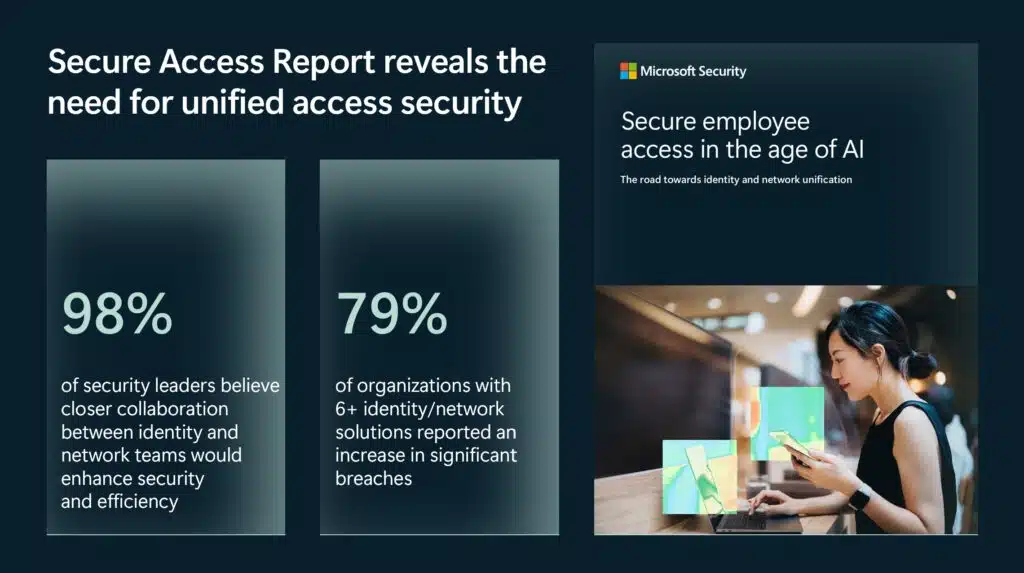
According to the report research, companies relying on a patchwork of six or more identity and network solutions not only face operational inefficiencies but also a 79% higher probability of a significant breach.2
At Microsoft, we understand that ITDR is an integrated partnership between identity and access management (IAM) and extended detection and response (XDR) and our vision has been to eliminate the organizational silos and unite these teams, their tools, and processes.
One of the key advantages of our integrated solution is its ability to provide end-to-end visibility and protection. Microsoft Entra natively feeds critical signals to Microsoft Defender and vice versa, enabling comprehensive identity protection across both on-premises, cloud environments, and third parties. Customers like ElringKlinger have recognized that fragmented, siloed security solutions were no longer sufficient to address the sophisticated nature of cyberthreats.
The combination of the individual Microsoft identity solutions is great. It helps us find issues that we might not uncover if we had siloed identity solutions and makes life easier for our team.
—Alexander Maute, Director of IT at ElringKlinger
Proactive protection: Hardening your Identity security posture
ITDR starts long before a cyberattack ever begins, specifically by minimizing your attack surface area. From an identity perspective this means eliminating the vulnerable configurations, stale accounts, and instances of over-privilege that cyberattackers often look to exploit. Microsoft’s approach to ITDR emphasizes this proactive stance: posture management isn’t just a best practice—it’s the foundation that makes real-time ITDR possible. We also understand that successful security practices require coordination across different teams and processes.
Microsoft Entra and Microsoft Defender surface actionable recommendations directly into Microsoft Secure Score and Extended Security Exposure Management (XSPM), enabling security teams to visualize attack paths, prioritize remediation, and proactively harden their defenses before threats materialize. The Identity Security initiative offers an identity-specific view of recommended actions from across on-premises and cloud identities, identity infrastructure, and third-party identity providers. These and other recommendations across endpoints, applications, data, networks, and identities help provide security leaders with unmatched visibility into potential attack paths and vulnerabilities, allowing them to identify and mitigate risks before they escalate.
Milliseconds matter: The power of real-time detection and response
Prevention alone is no longer sufficient in today’s evolving threat landscape—true cyber resilience relies on the ability to detect and respond at speed. In an environment where every second counts, Microsoft’s ITDR approach stands apart by delivering strategically layered defenses that help actively disrupt cyberthreats in real time by unifying the data, tools, and workflows across IAM and SOC teams.
The first layer comes in the form of dynamic, risk-based access controls leveraging the unparalleled insights from the identity landscape. As the identity provider, Microsoft Entra directly manages cloud authentication and enforces protection in real time at the point of authentication. This allows us to dynamically enforce access controls and step-up authentication faster and more consistently than anyone else. This is made possible through the native bi-directional integration between Entra and Defender, which enables continuous, real-time sharing of identity signals across identity and security operations.
What differentiates this approach is the built-in feedback loop: identity signals inform security detections instantly, and threat intelligence from Defender directly influences access decisions in Entra—without manual handoffs, or latency. In addition to adding more potential points of failure, multivendor solutions typically rely on older logs from prior log-on attempts and may not have the full context or see the changes that have happened since then.
Where the integration truly shines, however, is our identity threat response capabilities. During an active cyberattack, speed of response is critical. That’s why Microsoft has automatic attack disruption, a built-in self-defense capability that uses the correlated native signal in XDR, AI, and latest threat intelligence to identify and contain in-progress attacks like AiTM, ransomware, and more to prevent further lateral movement. Attack disruption maps out the attack path using insights from the unified platform to accurately predict where the attacker will go next. Once a threat is confirmed, Defender initiates automatic containment—isolating compromised assets or shutting down user sessions to prevent further spread.
This near real-time response not only stops the attack but also minimizes its impact, giving security teams critical time to investigate and remediate without disruption to the broader environment. This closed-loop integration strengthens risk engines over time, and responses become smarter and faster, saving time and balancing productivity and security for your identity and SOC teams.
Extending Zero Trust beyond ITDR
ITDR is a critical component of a modern cybersecurity strategy, but it’s only one part of a larger, evolving vision. At Microsoft, Zero Trust is not a checkpoint—it’s a guiding security philosophy that continues to scale and adapt with the evolving threat landscape. Securing the modern organization means adopting a Zero Trust strategy that protects users, data, applications, and infrastructure—regardless of where they reside. This includes enforcing least privileged access, verifying explicitly, and assuming breach as a constant. These principles must extend across the digital estate, not just within identity, but across endpoints, applications, and networks.
Microsoft delivers on this vision through an end-to-end portfolio that supports the full spectrum of Zero Trust capabilities. Microsoft Entra provides robust identity and access management. Microsoft Intune ensures device compliance and health. Microsoft Purview enforces data security and governance. Microsoft Defender offers threat protection across endpoints, identities, software as a service apps, email and collaboration tools, multicloud workloads, and data security insights. And Microsoft’s network access capabilities—delivered through the Entra Suite—secure connections and reduce lateral movement risks. And when you use them together, you can secure any identities, any apps, anywhere.
As organizations navigate increasingly complex environments—from hybrid work to multicloud infrastructures—Microsoft is committed to being a trusted partner on the Zero Trust journey. With Microsoft, organizations are not only prepared for today’s identity threats—they’re equipped for the future of secure digital transformation.
Microsoft Identity Threat Detection and Response
Get comprehensive protection for all of your identities and identity infrastructure. Learn more and explore products.

The future of ITDR
As threat actors grow more sophisticated, security strategies must evolve beyond fragmented tools and isolated signals. Looking ahead, ITDR will continue to serve as a cornerstone of Zero Trust—one that is natively integrated across identity, apps, endpoints, cloud, network, and beyond. With Microsoft as a trusted partner, business leaders are equipped to go beyond ITDR and protect your identities, secure your operations, and build resilience for the future.
Watch our video to learn more.
Learn more about Microsoft Identity Threat Detection and Response.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and X (@MSFTSecurity) for the latest news and updates on cybersecurity.
1Microsoft Digital Defense Report 2024
2Secure employee access in the age of AI
The post Modernize your identity defense with Microsoft Identity Threat Detection and Response appeared first on Microsoft Security Blog.
Source: Microsoft Security
