
As organizations dive deeper into their sustainability data journey, they need ever-sharper tools and resources to address complexity. We’re excited[…]
Read MoreThe finance department is the heart of the organization, juggling a myriad of critical, yet complex tasks—from quote-to-cash processes like[…]
Read More
A new breed of industry-leading company is taking shape — Frontier Firms. These organizations blend human ambition with AI-powered technology[…]
Read More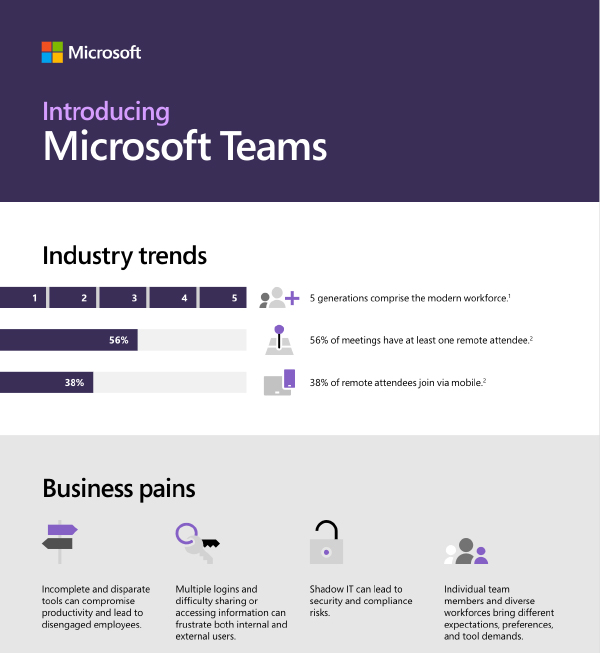
According to IWG, as many as 70% of employees work remotely at least one day each week. With a distributed workforce, individual team members and diverse employees bring different expectations, preferences, and tool demands. That’s why it’s important to have the right tools that everyone knows. Adopting a familiar modern workplace with solutions like Microsoft Teams can help bring your workforce together. At AGORA TECH srls, we have the expertise and experience to help you integrate the modern workplace you need to achieve more. Contact us today to learn more on how we can help.
Read More
With 5 generations collaborating in the workplace, how can you use a digital workspace to empower great ideas? Watch this video to learn how you can use #MicrosoftTeams to complement your #Office365 suite and enable efficient workplace collaboration, then contact AGORA TECH srls to get started.
Read More
Security operations teams can get overwhelmed. Protect yourself with Microsoft Threat Experts. You can search for threats, deliver data-driven insights and augment your existing resources. Together with Microsoft, AGORA TECH srls has your back.
Read MoreNotizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- 80% of Fortune 500 use active AI Agents: Observability, governance, and security shape the new frontier 10 Febbraio 2026
- Manipulating AI memory for profit: The rise of AI Recommendation Poisoning 10 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- A one-prompt attack that breaks LLM safety alignment 9 Febbraio 2026
- Analysis of active exploitation of SolarWinds Web Help Desk 7 Febbraio 2026
