
2023 has been quite a rollercoaster year for us in the retail industry. We’ve faced our share of challenges, from dealing with economic uncertainties to meeting the ever-changing demands of our customers. But the industry has shown incredible resilience and resourcefulness in the face of it all. Just[…]
Read More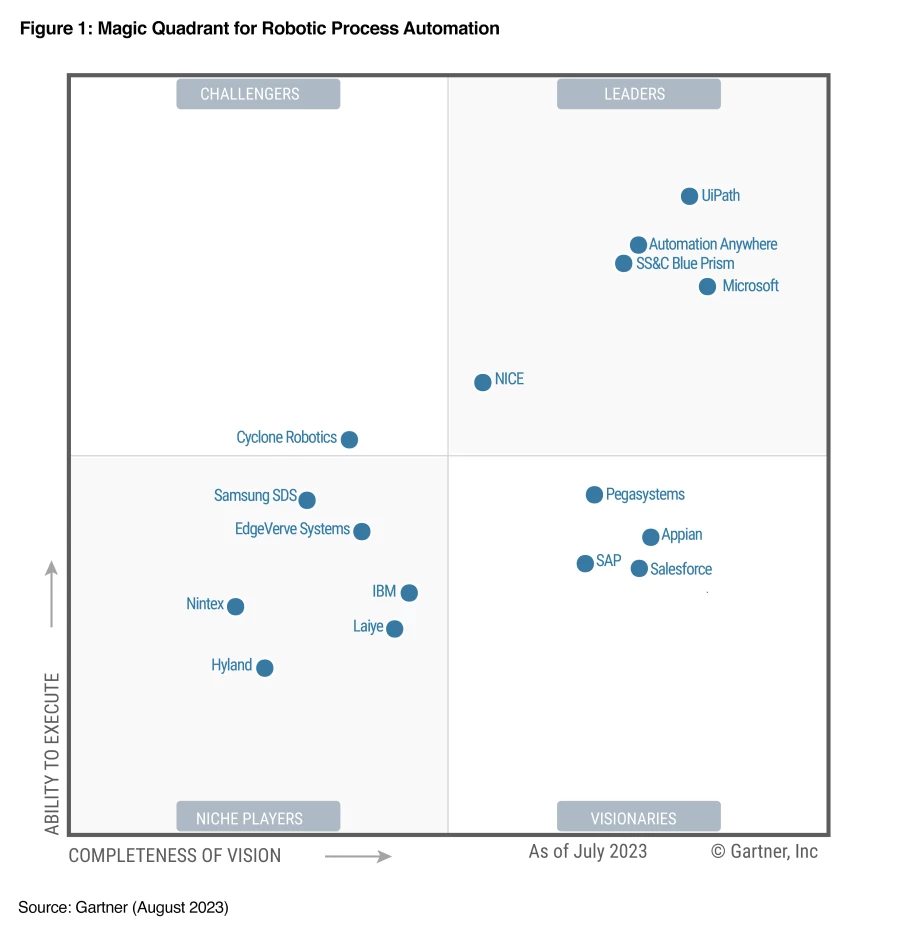
For the third consecutive year, Microsoft has been named a Leader in the Gartner® Magic Quadrant™ for Robotic Process Automation. This year Microsoft is positioned furthest in Completeness of Vision. We would like to thank our millions of active users and community members using Power Automate who helped[…]
Read More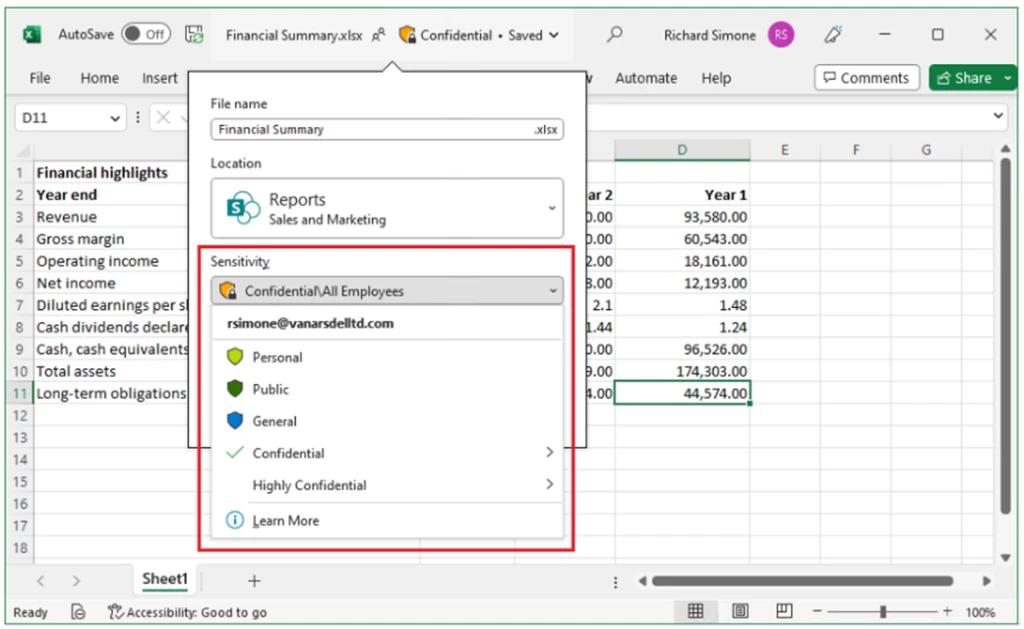
I recently worked with an enterprise customer who experienced a data exfiltration attack using the characteristics of the BazaCall campaign. BazaCall can be both a ransomware and data exfiltration attack that are used together to increase pressure on and damage to the victim. Microsoft Purview has data security[…]
Read More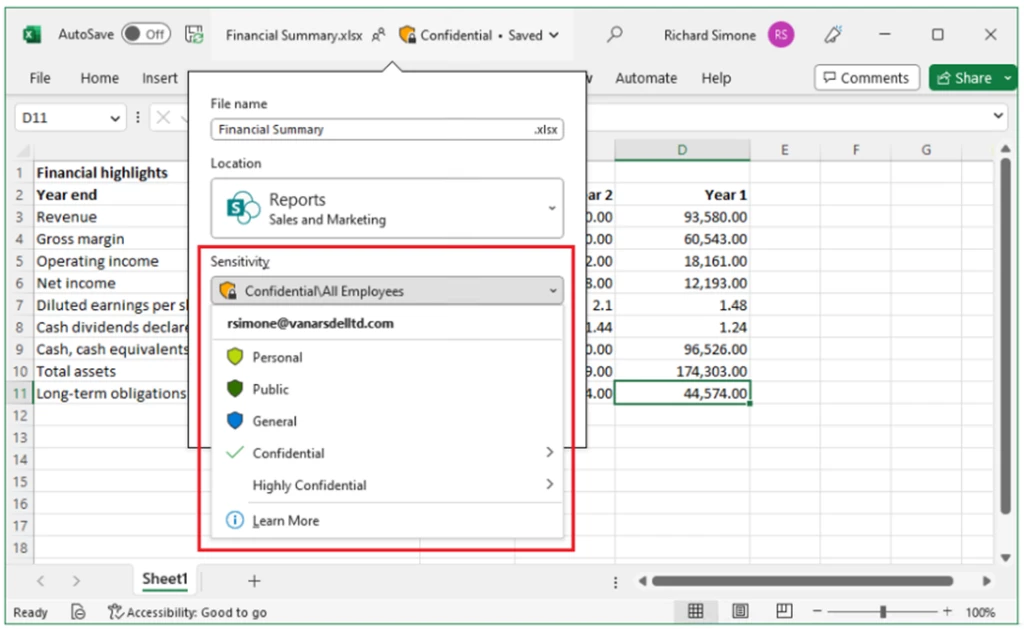
I recently worked with an enterprise customer who experienced a data exfiltration attack using the characteristics of the BazaCall campaign. BazaCall can be both a ransomware and data exfiltration attack that are used together to increase pressure on and damage to the victim. Microsoft Purview has data security[…]
Read More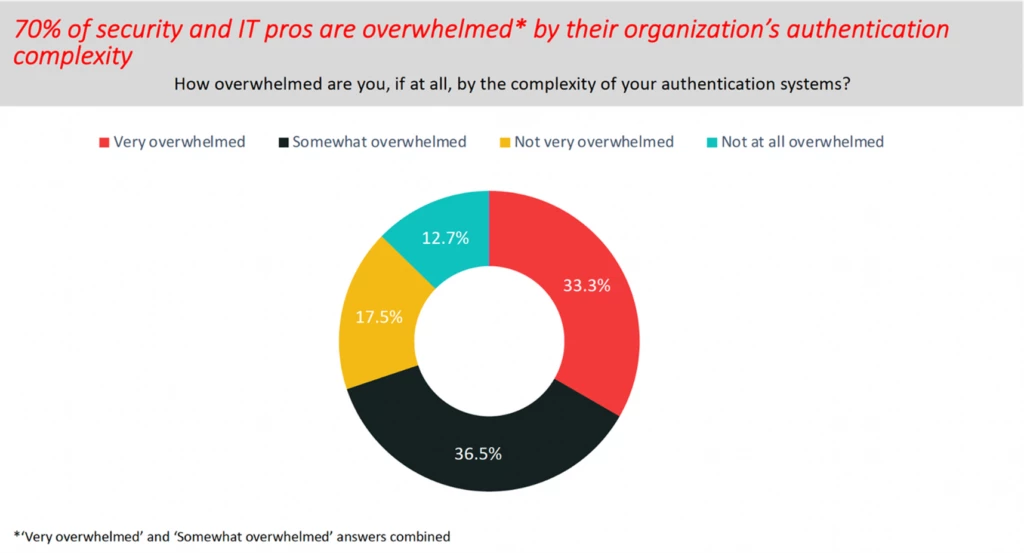
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Passwords are a security weakness and phishing attacks to exploit accounts protected by passwords are on the rise. The last 12 months have seen an average of more than 4,000 password attacks[…]
Read MoreNotizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
