Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: Customer controlled maintenance for Azure Firewall 9 Luglio 2025
- Microsoft expands Zero Trust workshop to cover network, SecOps, and more 9 Luglio 2025
- Enhancing Microsoft 365 security by eliminating high-privilege access 8 Luglio 2025
- What’s new in Power Apps: June 2025 Feature Update 8 Luglio 2025
- [In preview] Public Preview: Azure Storage Mover adds free, direct AWS S3-to-Azure Blob migration 7 Luglio 2025
- Learn how to build an AI-powered, unified SOC in new Microsoft e-book 7 Luglio 2025
- Dataverse MCP Server: A Game Changer for AI-Driven Workflows 7 Luglio 2025
- Build Modern Single-Page Applications in Power Pages (Preview) 3 Luglio 2025
- [Launched] Generally Available: Latest PostgreSQL minor versions supported by Azure Database for PostgreSQL flexible server 2 Luglio 2025
- [Launched] Generally Available: Azure DNS security policy 2 Luglio 2025
Leverage cloud-powered security with Microsoft Defender for IoT
Traditionally, operational technology (OT) and IT have occupied separate sides of enterprise security. But with digital transformation and the advent of Industry 4.0, the old, siloed approach is showing its age.1 The rise of manufacturing execution systems has enabled more “smart factories” to deliver improved manageability and data collection. While increased OT connectivity in energy production, utilities, transportation, and other critical industries help drive greater efficiency, it also creates new vulnerabilities. Roughly 41.6 billion devices are projected to be internet-facing by 2025, creating an enormous attack surface.2 And unlike IT environments, a breach in OT can have potentially life-threatening consequences, as evidenced by the 2021 cyberattack against a Florida city’s water supply.3
It is with great pleasure that we announce the general availability (GA) of the Microsoft Defender for IoT cloud-managed platform, which lets businesses interconnect their OT environment without compromising security. Powered by Microsoft’s scalable, cost-effective cloud technology, Defender for IoT helps you manage assets, track emerging threats, and control risks across enterprise and mission-critical networks—both in connected and air-gapped environments. In this blog, we’ll look at today’s connected OT environment, including the advantages of cloud-managed security and how a converged security operations center (SOC) can offer advantages over the traditional siloed approach.
Why choose a cloud-powered solution for IoT and OT security?
The proliferation of connected devices—everything from manufacturing systems, heating, ventilation, and air conditioning (HVAC), and building management systems (BMS) to heavy machinery for mining, drilling, and transportation—means that OT security solutions require speed, accuracy, and context on a massive scale. In the December 2022 issue of our Cyber Signals threat brief, Microsoft identified unpatched, high-severity vulnerabilities in 75 percent of the most common industrial controllers used in our customers’ OT networks. Even using ordinary Internet of Things (IoT) devices like printers and routers, attackers can breach and move laterally through an IT system, installing malware and stealing sensitive intellectual property. Cloud-powered IoT and OT security solutions offer several advantages over traditional solutions:
- Discovery of assets end-to-end: Asset profiling involves analyzing network signals to discover and categorize network assets, the information collected about those assets, and the types of assets they represent. Profiling in the cloud is driven by an extensive collection of classifiers, allowing for high-fidelity categorization into categories such as servers, workstations, mobile devices, and IoT devices. Monitoring and analyzing potential security risks can be done once the assets have been classified properly. This is critical for protecting an organization’s networks, as vulnerabilities or misconfigurations in any asset can create a potential entry point for attackers. By identifying and mitigating these risks, organizations can ensure that their infrastructure is secure and protects sensitive information.
- Detect and respond to threats as they occur in real-time: Reduce response times from days to minutes by detecting and responding to threats as they occur. Through collaboration between defenders from different industries, we can share best practices and information to better protect against emerging threats. By leveraging collective knowledge, defenders can stay ahead of malicious actors and respond to incidents as they occur. As a result, a cloud-powered OT solution can help prevent breaches and minimize their effects. For instance, by detecting malicious activity on a network or a suspicious login attempt, security analysts can respond immediately to prevent a breach or limit its extent.
- Defend against known and unknown threats: Microsoft AI and machine learning alerts provide real-time detection of threats, as well as automated responses to known or unknown attacks. These alerts are designed to help security teams quickly identify and investigate suspicious activity, then take the necessary steps to protect the organization. For instance, a security system that monitors network activity in real-time can detect suspicious activity within minutes of it occurring, alerting security administrators to take action before the attack has a chance to succeed.
- Compliance reports tailored to your requirements: Organizations can easily create and manage tailored compliance reports that are up-to-date, secure, and compliant with industry standards. With customizable reporting tools available in Microsoft Azure, users can obtain data from multiple sources and build robust, customized reports. Along with providing automated reporting and scheduling capabilities, Azure Workbooks provide a collaborative experience across silos.
- Workflows and integrations that leverage the cloud: Cloud-to-cloud integrations help organizations streamline workflows and easily access data from multiple sources. By connecting multiple cloud services, organizations can gain better visibility into their operations, automate processes, and reduce manual labor. Additionally, cloud-to-cloud integrations help organizations scale quickly and eliminate the need to purchase additional hardware and software. As a result, organizations can reduce costs and increase efficiency.
With any type of OT security, mean time to recovery (MTTR) provides a critical metric. A target MTTR for IT is typically between 30 minutes and two hours. However, because IoT and OT security often involves cyber physical systems used in utilities, healthcare, or energy production, every minute counts. Cloud-based OT security can make a difference by enabling real-time response rates across multiple locations. But what if you could take your security a step further by enabling a faster MTTR through a unified SOC for both IT and OT?
Unifying security efforts with a converged IT, IoT, and OT SOC
Empowering OT and IT security teams to work together helps create a unified front against evolving threats, maximizing your resources while gaining a comprehensive view of vulnerabilities. This way, a converged SOC taps into the strengths of both teams, creating a streamlined, cost-effective approach to enterprise security. By establishing common goals and key performance indicators, IT and OT security teams can work together on tabletop exercises to build cohesion. To learn more about how to empower OT and IT security teams to work together, watch our webinar, OT/IoT Enabled SOC with Microsoft Sentinel and Microsoft Defender for IoT.
The key benefits of a converged SOC include:
- Improved collaboration: Increase your team’s effectiveness in identifying and responding to threats by utilizing both IT skills and OT knowledge, creating a better understanding of potential impacts on both IT and OT systems.
- Greater visibility: Gain a complete picture of vulnerabilities across both the business and industrial sides of your organization. Then take proactive measures to prevent a breach.
- Streamlined response: Eliminate the need to transfer incidents between IT and OT teams, reducing response times. Mitigate security incidents with swift, coordinated actions to reduce potential damage.
- Strengthened compliance: Share knowledge and expertise easily to ensure that all areas of the business comply with industry regulations and standards.
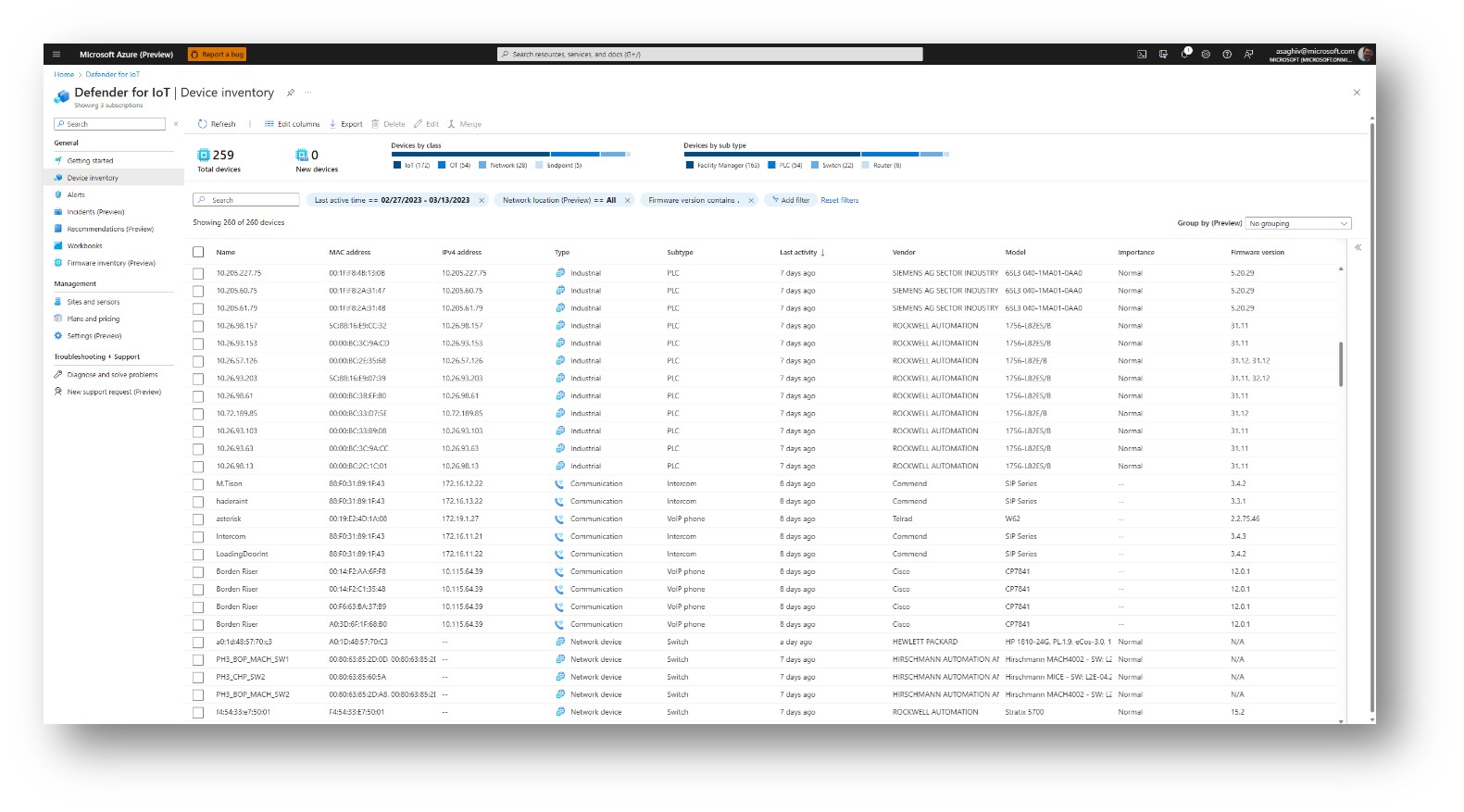
Figure 1. Defender for IoT—Device inventory view.
Microsoft Defender for IoT is a unified solution for today’s converged SOC
Given the 75 percent vulnerability rate in industrial controllers, nearly every organization using OT will need to reevaluate the security posture of both its legacy equipment (brownfield; lacking security) and its newer devices (greenfield; with some built-in security).2 Older network monitoring systems are not familiar with IoT and OT protocols, making them unreliable. A purpose-built solution is needed for today’s converged SOC.
With Microsoft Defender for IoT, you can achieve faster time-to-value, improve agility and scalability, increase visibility, and strengthen the resiliency of your network and infrastructure without making significant changes. The Defender for IoT cloud is designed to augment your on-premises processing power while providing a source of centralized management for global security teams—raising the bar for OT defense. Let’s walk through how a typical scenario might play out.
How Defender for IoT works—scenario:
- A new common vulnerability and exposure (CVE) is published with information that may affect your organization’s OT devices. Even more concerning, you discover that hackers have been sharing this vulnerability widely online.
- With Microsoft Threat Intelligence, the new CVE is ingested automatically and shared across our cloud-based security services, including Defender for IoT.
- Using the Microsoft Azure Portal, your SOC can begin monitoring for the new vulnerability across all devices and sites.
- Result: Securing your IoT and OT environment becomes faster and more comprehensive.
Additional scenarios where your SOC could see immediate benefit with Defender for IoT include:
- OT security and compliance audits.
- Attack surface reduction consulting.
- Tabletop exercises.
See and protect everything with Device inventory
With the GA of Defender for IoT, Device inventory now allows your SOC to confidently manage OT devices from a single pane of glass through the Microsoft Azure Portal. By supporting unlimited data sources (such as manufacturer, type, serial number, firmware, and more), Device inventory helps your security team gain a complete picture of your IoT and OT assets and proactively addresses any vulnerabilities using Microsoft’s scalable, cloud-managed platform.
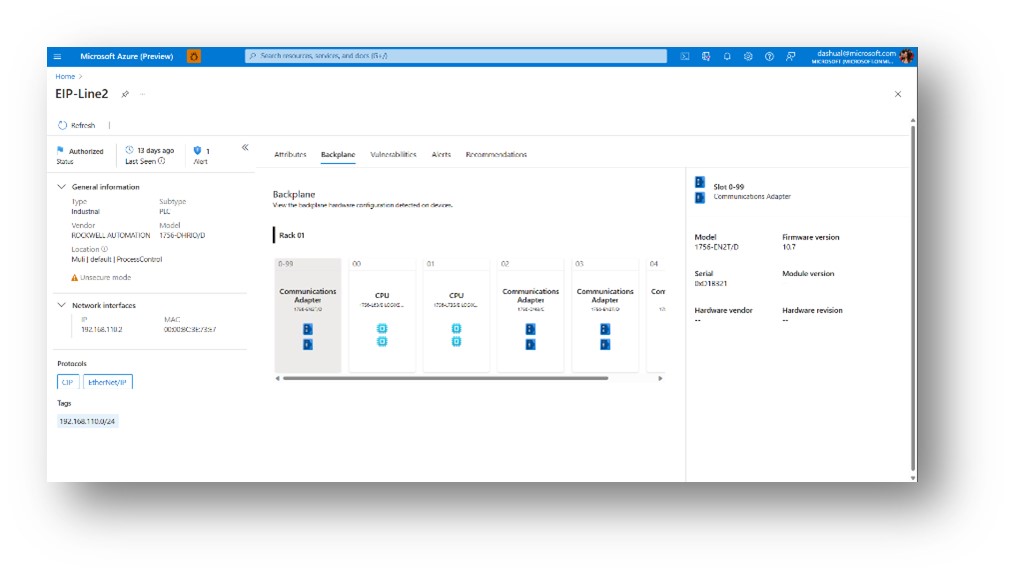
Figure 2. Defender for IoT—Comprehensive view of an asset with backplane modules.
Simplified integration for end-to-end protection
To enable comprehensive protection across your enterprise, Defender for IoT easily integrates with Microsoft Sentinel. Together, Defender for IoT and Microsoft Sentinel provide security information and event management (SIEM) for both OT and IT environments. Defender for IoT also shares threat data with Microsoft 365 Defender, Microsoft Defender for Cloud, and non-Microsoft products like Splunk, IBM QRadar, and ServiceNow. This extensive and integrated ecosystem allows your converged SOC to tune alerts automatically across IoT and IT, creating baselines and custom alerts that help reduce alert fatigue.
Creating security for all—you’re invited
To learn more about how Microsoft Defender for IoT can help create a unified security solution for your converged SOC, remember to mark your calendars for the RSA Conference, April 24 to 27, 2023, and visit us at Microsoft booth 604. Register now for the special RSA Microsoft pre-day event.
Want to be among the first to see the AI-powered future of cybersecurity and the latest advances in cloud defense? Join us at Microsoft’s new digital security-only event, Microsoft Secure, on March 28, 2023.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and Twitter (@MSFTSecurity) for the latest news and updates on cybersecurity.
1Industry 4.0 technologies assessment: A sustainability perspective, Chunguang Bai, Patrick Dallasega, Guido Orzes, and Joseph Sarkis. November 2020.
2The convergence of IT and OT: Cyber risks to critical infrastructure on the rise, Microsoft. December 2022.
3Someone tried to poison a Florida city by hacking into the water treatment system, sheriff says, Amir Vera, Jamiel Lynch, and Christina Carrega. February 8, 2021.
The post Leverage cloud-powered security with Microsoft Defender for IoT appeared first on Microsoft Security Blog.
Source: Microsoft Security
