Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: Latest PostgreSQL minor versions supported by Azure Database for PostgreSQL flexible server 2 Luglio 2025
- [Launched] Generally Available: Azure DNS security policy 2 Luglio 2025
- [In preview] Public Preview: Azure SQL updates for early-July 2025 2 Luglio 2025
- [Launched] Generally Available: Azure SQL updates for early-July 2025 2 Luglio 2025
- Retirement: VM Insights Map and Dependency Agent are being on June 30, 2028 2 Luglio 2025
- Planning your move to Microsoft Defender portal for all Microsoft Sentinel customers 1 Luglio 2025
- [Launched] Generally Available: Azure App Service on Azure Stack Hub 25R1 1 Luglio 2025
- Jasper Sleet: North Korean remote IT workers’ evolving tactics to infiltrate organizations 30 Giugno 2025
- [Launched] Generally Available: Encryption in Transit (EiT) for Azure Files NFS shares 30 Giugno 2025
- [Launched] Generally Available: Query editor in Azure Monitor Metrics 30 Giugno 2025
Microsoft shifts to a new threat actor naming taxonomy
Today, Microsoft is excited to announce that we are shifting to a new threat actor naming taxonomy aligned to the theme of weather. The complexity, scale, and volume of threats is increasing, driving the need to reimagine not only how Microsoft talks about threats but also how we enable customers to understand those threats quickly and with clarity. With the new taxonomy, we intend to bring better context to customers and security researchers that are already confronted with an overwhelming amount of threat intelligence data. It will offer a more organized, memorable, and easy way to reference adversary groups so that organizations can better prioritize threats and protect themselves. Simply put, security professionals will instantly have an idea of the type of threat actor they are up against, just by reading the name.
The Microsoft Threat Intelligence community has spent over a decade discovering, tracking, and identifying targeted malicious activity and sharing that critical intelligence with customers. Our threat research has grown to track more than 300 unique threat actors, including 160 nation-state actors, 50 ransomware groups, and hundreds of others. A global multi-disciplinary assembly of threat intelligence analysts, pen testers, and data scientists work together alongside experts in geopolitics and disinformation to take a whole-of-adversary approach. This helps Microsoft Threat Intelligence teams fully understand the what of an attack, make assessments on the why, then forecast and implement protections for where an attacker might go next. Our vision is that this new naming model helps our customers and the industry move to a more proactive approach to defense.
We realize that other vendors in the industry also have unique naming taxonomies representing their distinct view of threats based on their intelligence. However, there are often overlaps or close alignments with tracked actors, and keeping track of these names can be challenging for defenders. Microsoft Threat Intelligence is committed to helping customers understand threats, no matter which naming taxonomy they are familiar with. Therefore, we will strive to also include other threat actor names within our security products to reflect these analytic overlaps and help customers make well-informed decisions.
The Microsoft threat actor taxonomy explained
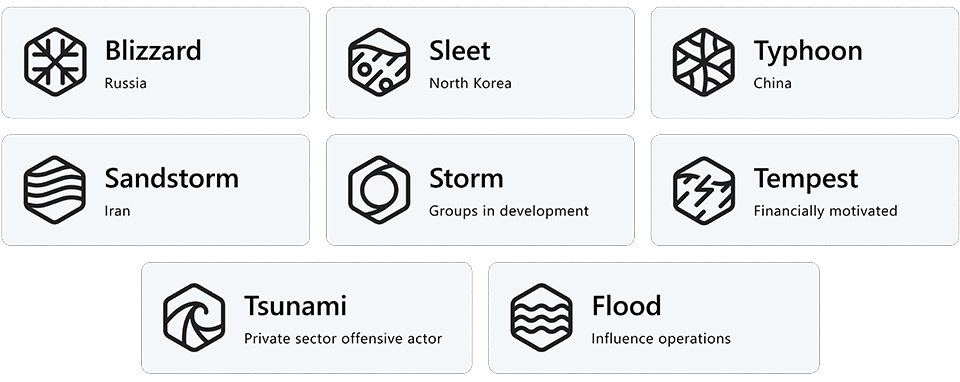
In our new taxonomy, threat actor groups will be named after weather events. A weather event or “family name” represents either a nation-state actor attribution (e.g., Typhoon indicates origin or attribution to China) or a motivation (e.g., Tempest indicates financially motivated actors). The table below shows the threat actor groups Microsoft tracks and their assigned weather events in the new naming convention.
| Actor category | Type | Family Name |
| Nation state | China | Typhoon |
| Iran | Sandstorm | |
| Lebanon | Rain | |
| North Korea | Sleet | |
| Russia | Blizzard | |
| South Korea | Hail | |
| Turkey | Dust | |
| Vietnam | Cyclone | |
| Financially motivated | Financially motivated | Tempest |
| Private sector offensive actors | PSOAs | Tsunami |
| Influence operations | Influence operations | Flood |
| Groups in development | Groups in development | Storm |
Threat actors within the same weather family are given an adjective to distinguish actor groups that have distinct TTPs, infrastructure, objectives, or other identified patterns. The examples below show how the naming system works for Russia and Iran.
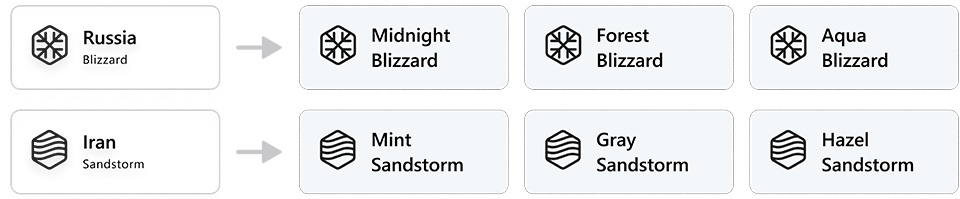
Note: Our latest blog about the Iranian threat actor Mint Sandstorm (previously PHOSPHORUS) reflects the new naming taxonomy: Nation-state threat actor Mint Sandstorm refines tradecraft to attack high-value targets.
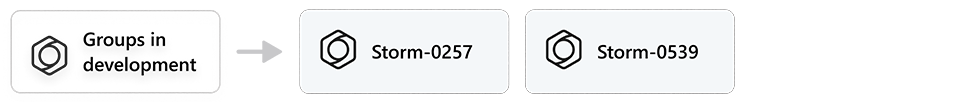
Where there is a newly discovered, unknown, or emerging cluster of threat activity, we use a temporary designation of Storm (previously DEV) and a four-digit number, allowing us to track it as a unique set of information until we can reach high confidence about the origin or identity of the actor behind the operation. Once our analysis has developed to meet high confidence criteria, a Storm is converted to a named actor.
We believe this new approach, along with the new icon system shown in some of the examples above, makes it even easier to identify and remember Microsoft’s threat actors. Each icon uniquely represents a family name, and where it makes sense will accompany the threat actor names as a visual aid. This new naming approach does not in any way change who the threat actors are that we are tracking, or our current analysis behind the names.
The naming approach we have used previously (Elements, Trees, Volcanoes, and DEVs) has been retired. We have reassigned all existing threat actors to the new taxonomy, and going forward will be using the new threat actor names. Over the next few weeks, you will start seeing changes across public facing content and in-product experiences. We estimate to complete prioritized in-product updates by September 2023. There will be some surfaces that will not be updated. To ease the transition from old names to new names, we developed a reference guide at https://aka.ms/threatactors. Make sure to bookmark it for future reference.
Microsoft’s approach to threat actor tracking
The way Microsoft Threat Intelligence approaches identifying and naming threat actors is outlined below in Figure 4. As is sometimes the case, when a new threat surfaces, we don’t know all the details. We might know about a subset of victims and the malware they were infected with, and/or the command-and-control infrastructure, but we sometimes don’t immediately know the full scope of the actor’s capability or victimology. Microsoft maintains an internal process for tracking these ‘in-development’ activity clusters (now Storm-###) for reference across our hunting teams. In-development names (e.g., Storm-0257) apply to all actor types (nation-state, financially motivated, PSOA, etc.).
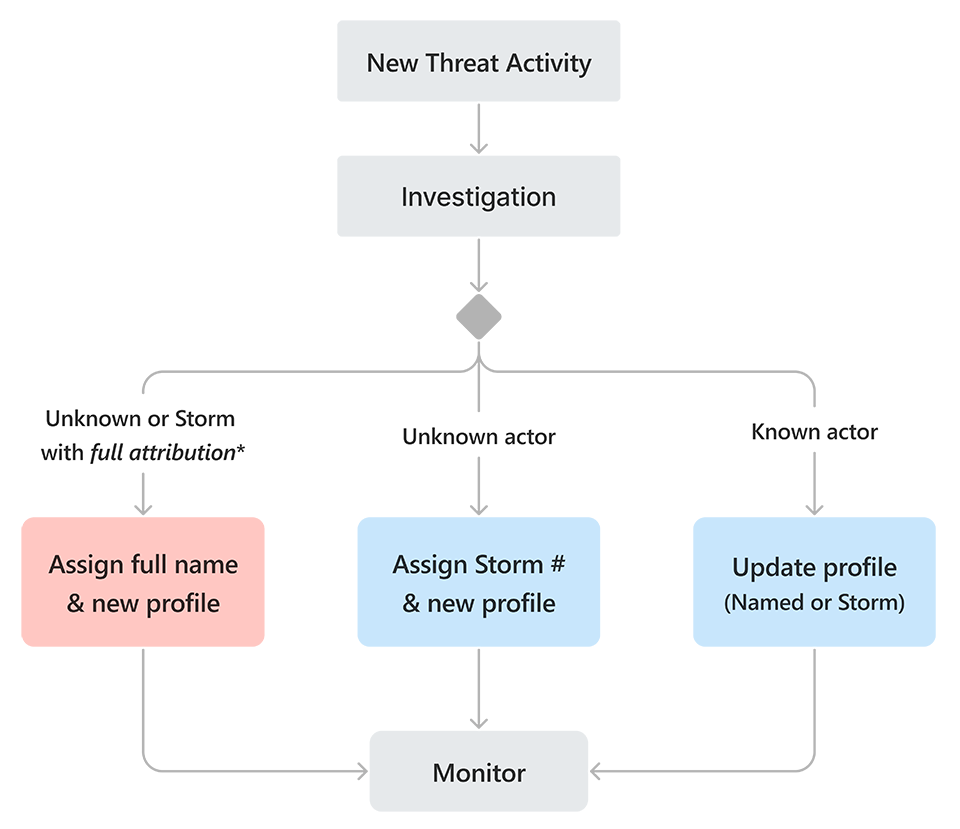
*Full attribution means known capabilities, techniques, infrastructure, scope, and intent of the activity
Storm names may persist indefinitely, but we strive to progress our understanding of all clusters of threat activity to either merge them with existing fully named actors (thereby expanding the definition), or merge multiple in-development clusters together to define a new fully named actor.
To meet the requirements of a full name, we aim to gain knowledge of the actor’s infrastructure, tooling, victimology, and motivation. We expand and update the definitions supporting our actor names based on our own telemetry, industry reporting, and a combination thereof.
The new centralized home of Microsoft threat actor intelligence
As a security industry leader, Microsoft has unique capabilities to track threats and the expectation to provide timely, consistent analysis will only increase. In a growing industry of complexity, confusion, and an overwhelming amount of data, we see an opportunity to provide customers with hyper relevant threat intelligence enabling them to implement even more proactive defenses.
We know defenders benefit from context and actionable insight– they need to understand what threat actor is behind an attack and how they can take steps to mitigate the issue. This is where Intel Profiles in Microsoft Defender Threat Intelligence can bring crucial information and context about threats. Integrated into Microsoft 365 Defender, Intel Profiles are updated daily and put the wealth of information tracked by the Microsoft Threat Intelligence community about threat actors and their tools and techniques directly into the hands of security operations professionals so that they can investigate, analyze, and hunt for threats.
We’re excited to share this new threat actor update with you, our defenders, and help bring clarity and relevance to the threat intelligence you are getting from Microsoft.
Resources
To ease the transition to the new naming taxonomy, use this reference guide to look up the old and new names of Microsoft threat actors: https://aka.ms/threatactors.
For the latest security research from the Microsoft Threat Intelligence community, check out the Microsoft Threat Intelligence Blog: https://aka.ms/threatintelblog.
For additional insights into the threat landscape, visit the Microsoft Security Insider.
The post Microsoft shifts to a new threat actor naming taxonomy appeared first on Microsoft Security Blog.
Source: Microsoft Security
