Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: GRS and CRR support for Azure VMs using Premium SSD v2 in Azure Backup availability in Norway and Japan 17 Luglio 2025
- [Launched] Generally Available: Geo-Replication for Azure Event Hubs Premium and Dedicated 17 Luglio 2025
- [In preview] Public Preview: CLI command for migration from Availability Sets and Basic load balancer on AKS 17 Luglio 2025
- [Launched] Generally Available: Virtual Machines node pools support in AKS 17 Luglio 2025
- [In preview] Public Preview: Max blocked nodes allowed support in AKS 17 Luglio 2025
- [Launched] Generally Available: Cluster Extension Manager move to AKS control plane 17 Luglio 2025
- [Launched] Generally Available: Node auto-provisioning support in AKS 17 Luglio 2025
- Transparency on Microsoft Defender for Office 365 email security effectiveness 17 Luglio 2025
- [In preview] Public Preview: AZNFS (3.0) for BlobNFS with FUSE for superior performance 17 Luglio 2025
- [Launched] Generally Available: Durable Functions PowerShell SDK as a standalone module 17 Luglio 2025
We’re excited and honored to be positioned in the Leaders Category in the IDC MarketScape: Worldwide SIEM (security information and event management) for Enterprise 2024 Vendor Assessment (doc #US51541324, September 2024)—our third major analyst report in SIEM to name Microsoft as a Leader. We were recognized in the[…]
Read More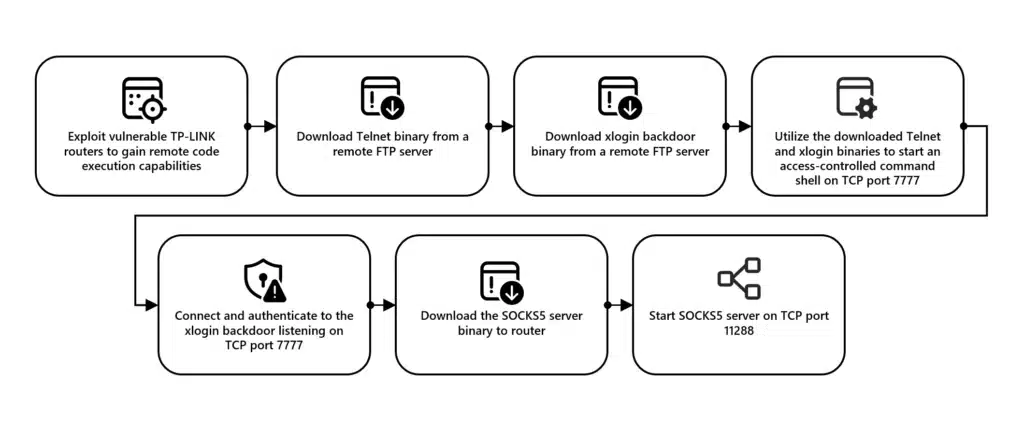
Since August 2023, Microsoft has observed intrusion activity targeting and successfully stealing credentials from multiple Microsoft customers that is enabled by highly evasive password spray attacks. Microsoft has linked the source of these password spray attacks to a network of compromised devices we track as CovertNetwork-1658, also known[…]
Read More
As October draws to a close, marking 21 years of Cybersecurity Awareness Month, cyberattacks continue to be a challenge for businesses of all sizes, however, small and medium businesses (SMBs) face distinct challenges when it comes to cybersecurity. Although SMBs face heightened cybersecurity threats, unlike large enterprises, they[…]
Read More
Now more than ever is the time for every organization to prioritize security. The use of AI by cyberattackers gives them an asymmetric advantage over defenders, as cyberattackers only have to be right once, while defenders have to be right 100% of the time. The way to win[…]
Read More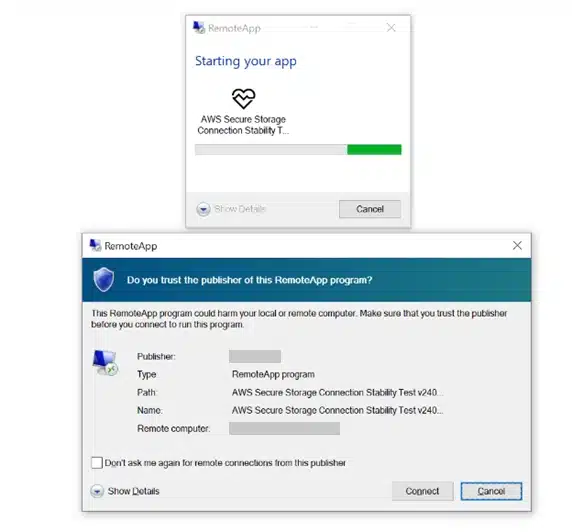
Since October 22, 2024, Microsoft Threat Intelligence has observed Russian threat actor Midnight Blizzard sending a series of highly targeted spear-phishing emails to individuals in government, academia, defense, non-governmental organizations, and other sectors. This activity is ongoing, and Microsoft will continue to investigate and provide updates as available.[…]
Read More
We’ve launched 2024 release wave 2 for Microsoft Dynamics 365, Microsoft Power Platform, and role-based Microsoft Copilot offerings—introducing a rollout of new features and enhanced capabilities releasing between October 2024 and March 2025. These updates include advanced Copilot capabilities for Microsoft 365 Copilot for Sales, Copilot for Service,[…]
Read MoreHealthcare organizations are an increasingly attractive target for threat actors. In a new Microsoft Threat Intelligence report, US healthcare at risk: strengthening resiliency against ransomware attacks, our researchers identified that ransomware continues to be among the most common and impactful cyberthreats targeting organizations. The report offers a holistic[…]
Read MoreHealthcare organizations are an increasingly attractive target for threat actors. In a new Microsoft Threat Intelligence report, US healthcare at risk: strengthening resiliency against ransomware attacks, our researchers identified that ransomware continues to be among the most common and impactful cyberthreats targeting organizations. The report offers a holistic[…]
Read More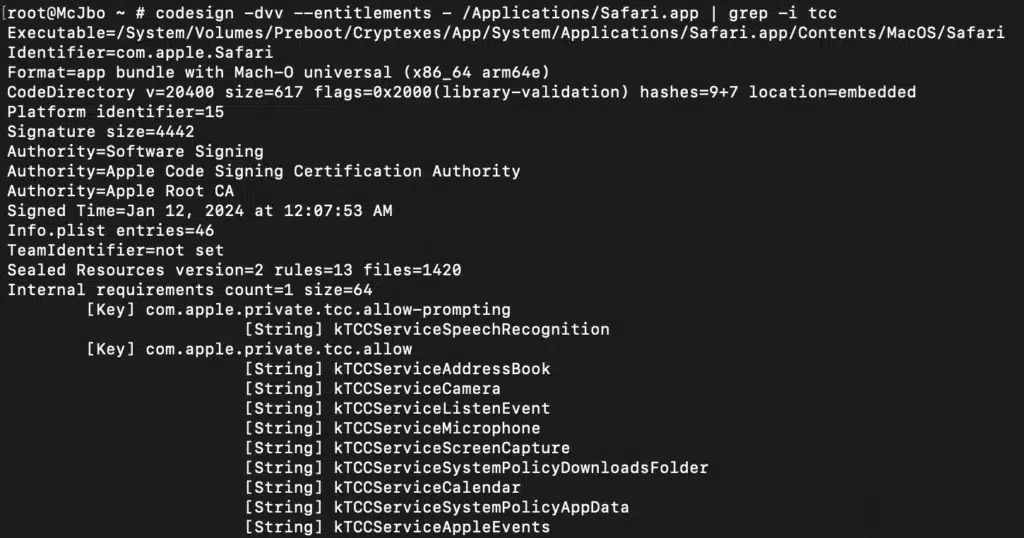
Microsoft Threat Intelligence uncovered a macOS vulnerability that could potentially allow an attacker to bypass the operating system’s Transparency, Consent, and Control (TCC) technology and gain unauthorized access to a user’s protected data. The vulnerability, which we refer to as “HM Surf”, involves removing the TCC protection for[…]
Read More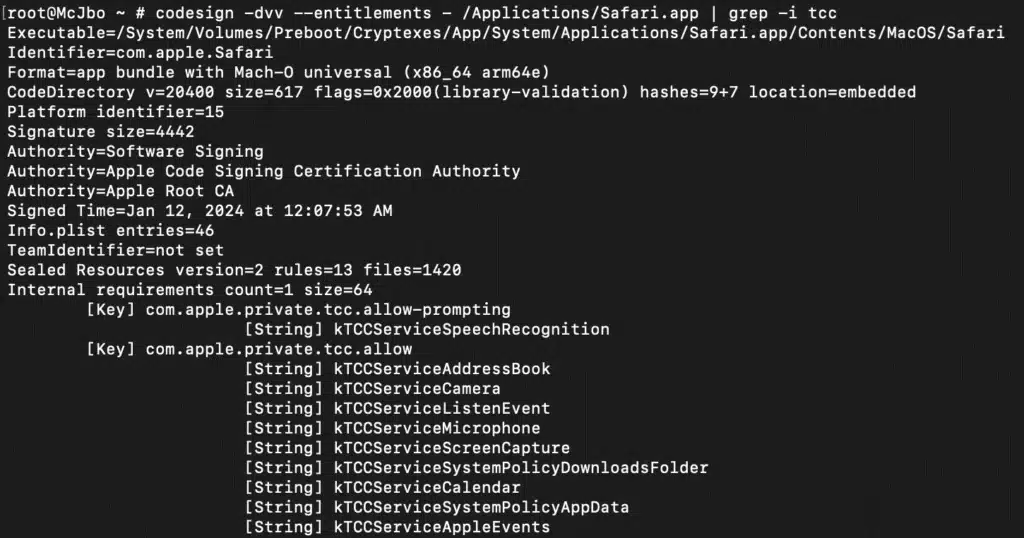
Microsoft Threat Intelligence uncovered a macOS vulnerability that could potentially allow an attacker to bypass the operating system’s Transparency, Consent, and Control (TCC) technology and gain unauthorized access to a user’s protected data. The vulnerability, which we refer to as “HM Surf”, involves removing the TCC protection for[…]
Read More