Notizie per Categorie
Articoli Recenti
- Jasper Sleet: North Korean remote IT workers’ evolving tactics to infiltrate organizations 30 Giugno 2025
- [Launched] Generally Available: Encryption in Transit (EiT) for Azure Files NFS shares 30 Giugno 2025
- [Launched] Generally Available: Query editor in Azure Monitor Metrics 30 Giugno 2025
- [Launched] Generally Available: FQDN Filtering in DNAT rules in Azure Firewall 30 Giugno 2025
- [In preview] Generally Available: Two-Way Forest Trusts for Microsoft Entra Domain Services 30 Giugno 2025
- Unveiling RIFT: Enhancing Rust malware analysis through pattern matching 27 Giugno 2025
- [Launched] Generally Available: Azure FXv2-series Virtual Machines 26 Giugno 2025
- [In preview] Public Preview: Draft & Deploy on Azure Firewall 26 Giugno 2025
- [Launched] Generally Available: Azure Virtual Network Manager IP address management 26 Giugno 2025
- [Launched] Generally Available: Transition existing platform-managed keys (PMK) to customer-managed keys (CMK) for Azure NetApp Files volumes without data migration. 26 Giugno 2025
Microsoft Defender Experts for Hunting demonstrates industry-leading protection in the 2022 MITRE Engenuity ATT&CK® Evaluations for Managed Services
Microsoft Defender Experts for Hunting, our newest managed threat hunting service, delivered industry-leading results during the inaugural MITRE Engenuity ATT&CK® Evaluations for Managed Services.
We provided a seamless, comprehensive, and rapid response to the simulated attack using expert-led threat hunting and an industry-leading extended detection and response (XDR) platform—Microsoft 365 Defender. This evaluation showcased our service’s strength in the following areas:
- In-depth visibility and analytics across all stages of the attack chain.
- Comprehensive managed hunting.
- Seamless alert prioritization and consolidation into notifications for the security operations center (SOC).
- Tailored hunting guidance and advanced hunting queries (AHQ) to optimize investigations.
- Frequently updated and customized recommendations for rapid containment and remediation.
- Threat actor attribution with tactics, techniques, and procedures (TTP) context.
- Technology powered by a team of expert hunters and a customer-centric approach.
- Commitment to managed extended detection and response (MXDR) partners running on Microsoft 365 Defender.
In-depth visibility and analytics across all stages of the attack chain
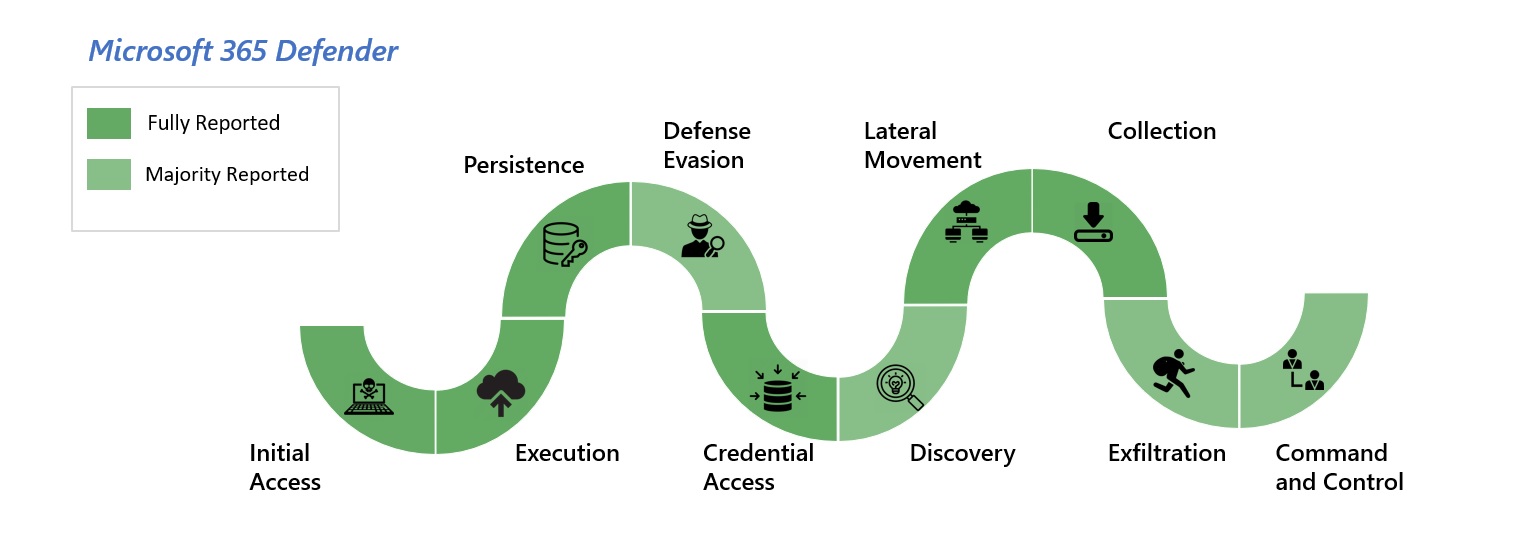
Figure 1. Microsoft Defender Experts for Hunting coverage. Fully reported—including initial access, execution, persistence, credential access, lateral movement, and collection—reflects 100 percent acceptance of evidence submission. Majority reported—including defense evasion, discovery, exfiltration, and command and control—reflects some gaps in evidence acceptance.
Comprehensive managed hunting
Microsoft Defender Experts for Hunting team identified all threats and provided a cohesive attack timeline with remediation guidance.
From the early stages of the intrusion, our hunters alerted the customer that a malicious archive masquerading as marketing materials was potentially part of a targeted attack. After a user opened the archive, a threat actor, which we attributed with high confidence as EUROPIUM, gained access to the environment.
Over the next few days, the threat actor used this foothold to steal credentials, move laterally in the network, deploy a web shell on an Exchange Server, and escalate privileges in the domain. The threat actor ultimately used their access to target sensitive data on an SQL server. Based on available telemetry, we reported that the threat actor staged sensitive data and may have successfully exfiltrated the data through email using a malicious RDAT utility.
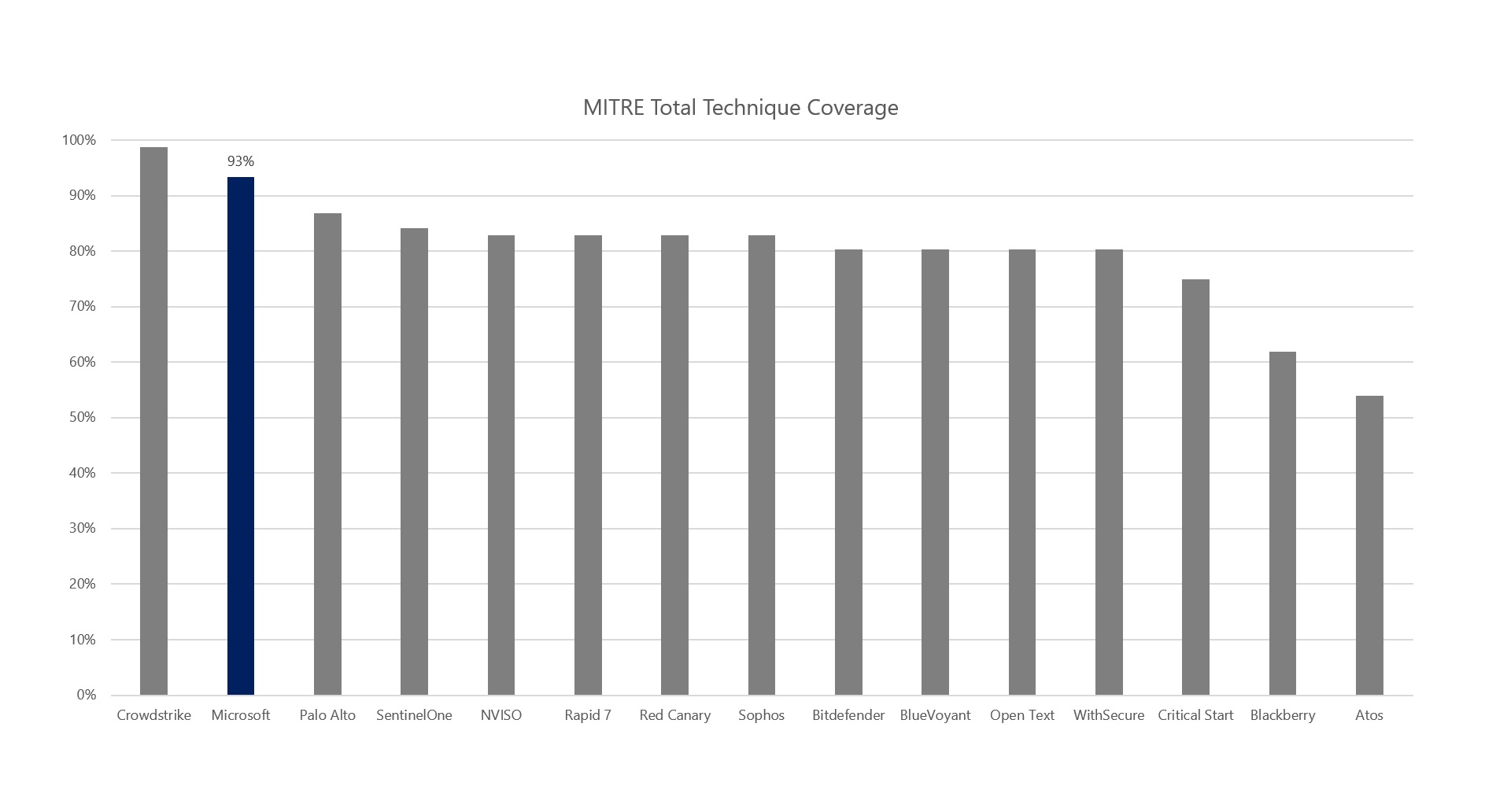
Figure 2. Microsoft results compared to all other vendors out of 76 total techniques.
Microsoft threat hunters discovered and investigated all of the essential and impactful TTPs used in this evaluation.
Seamless alert prioritization and consolidation into notifications for the SOC
From initial malware execution to data theft, Microsoft 365 Defender seamlessly detected and correlated alerts from all stages of the attack chain into two overarching incidents that provided end-to-end attack stories (see Figure 3). Microsoft 365 Defender’s incident correlation technology helps SOC analysts to counter alert fatigue, and our hunters then enrich these incidents by finding new attacks with the existing deep signals and custom alerting.
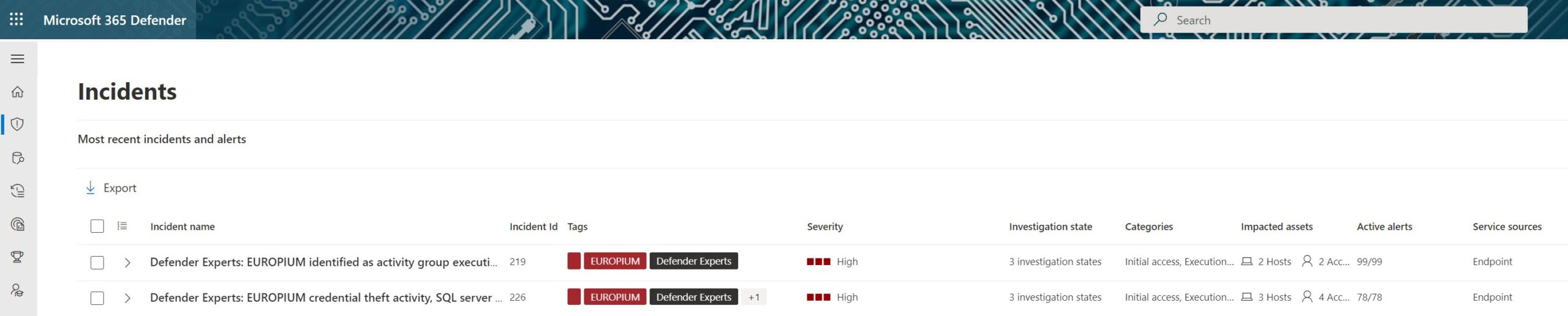
Figure 3. Consolidated incidents enriched by Defender Experts for Hunting as illustrated in the above tags.
Our hunters followed up on automated alerting with Defender Expert notifications (DENs) to provide additional context on the threat activity with an executive summary, threat actor attribution, detailed scope of impact, recommendations, and advanced hunting queries to self-serve investigations and response actions. This human enrichment helps the customer prioritize their time and focused actions in the SOC.
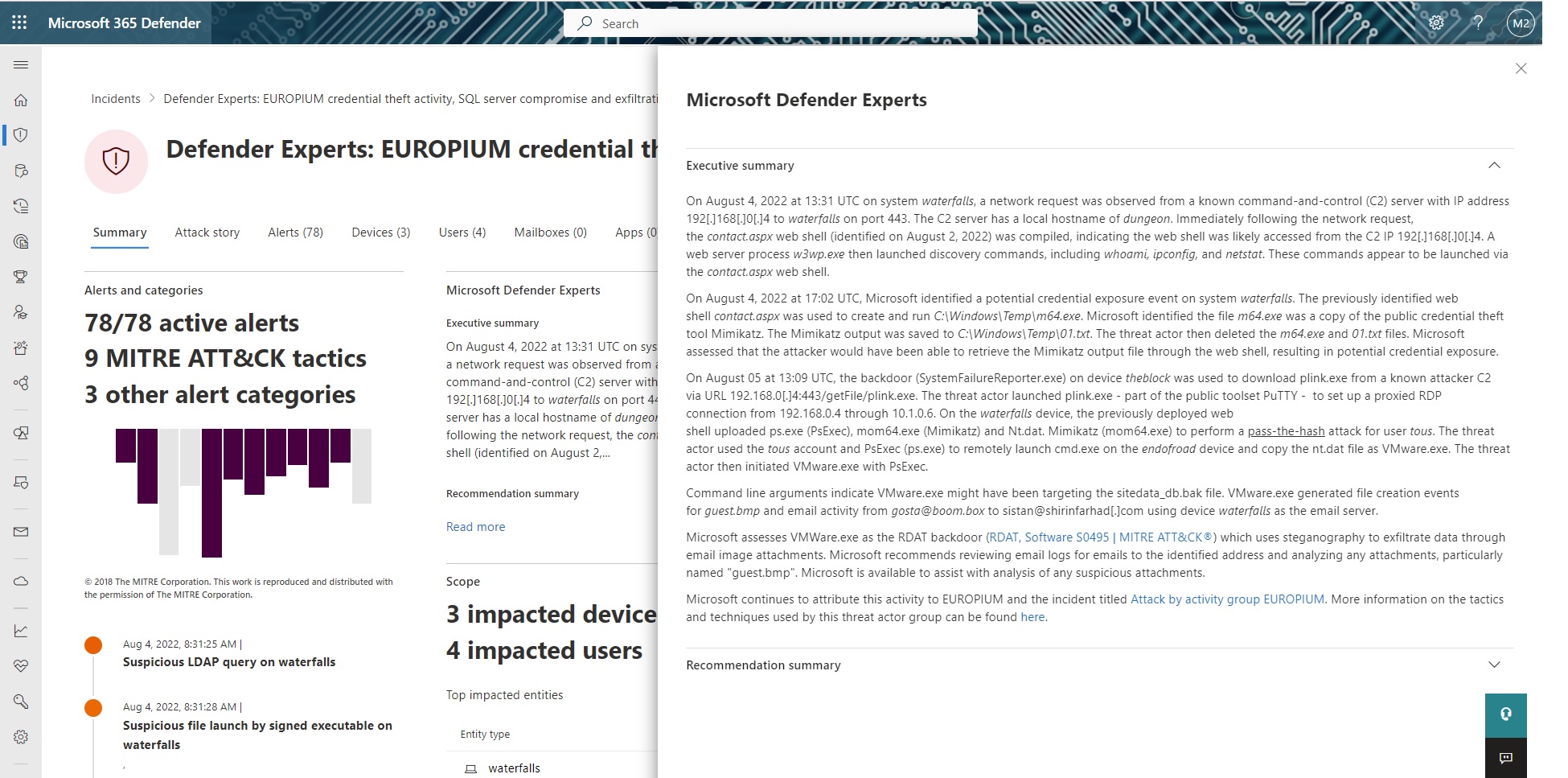
Figure 4. Beginning of incident executive summary provided by Defender Experts.
Tailored hunting guidance and AHQ to optimize investigations
Within the DENs, our hunters additionally provided tailored hunting guidance and AHQs to enable investigators to hunt for and identify relevant attack activity in each incident. Figure 5 shows one example where we directly flagged to the customer that a series of file modification events were consistent with data exfiltration attempts.
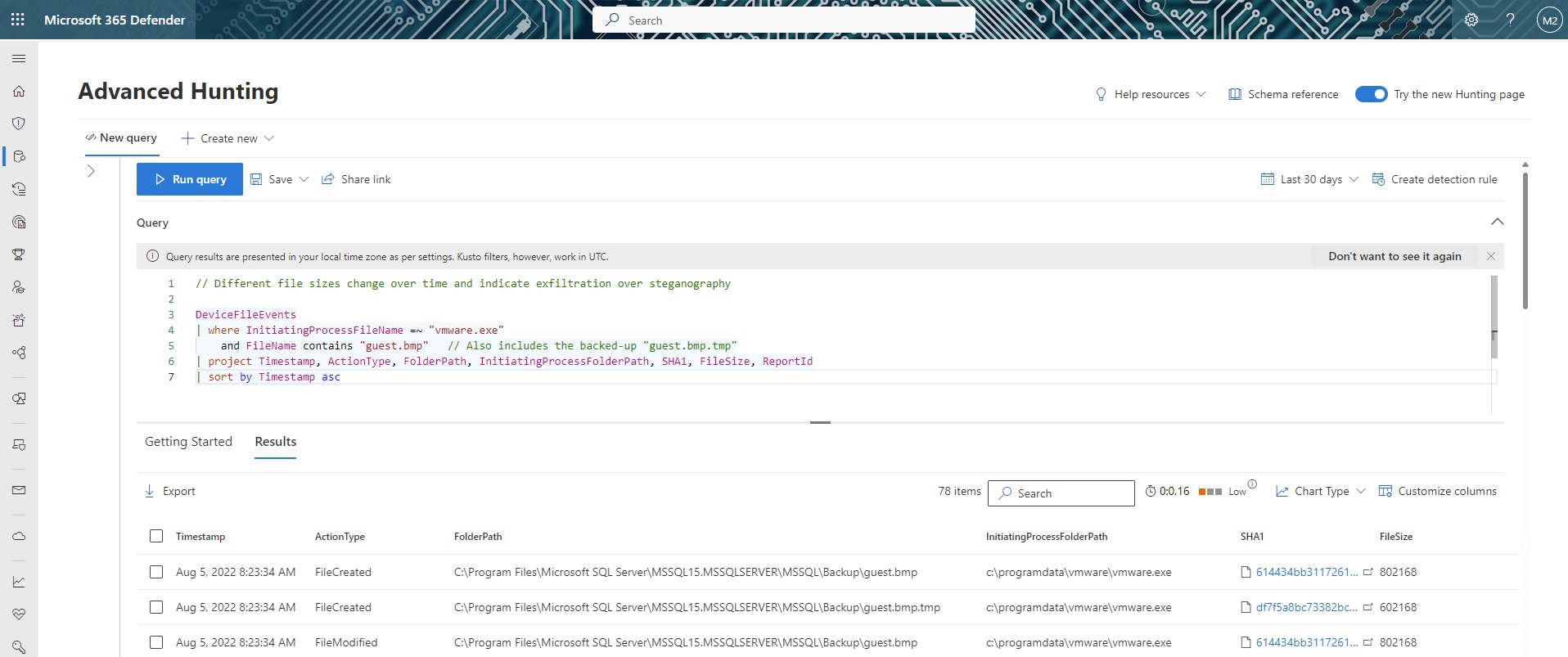
Figure 5. Example of running provided AHQs to surface activity of interest.
Frequently updated and customized recommendations for containment and remediation
Throughout the attack, our hunters regularly shared remediation guidance to aid the customer in a rapid response (Figure 6). As the incident developed, using the Recommendation Summary, we kept the customer apprised of the scope of the attack and the efforts needed to contain it.
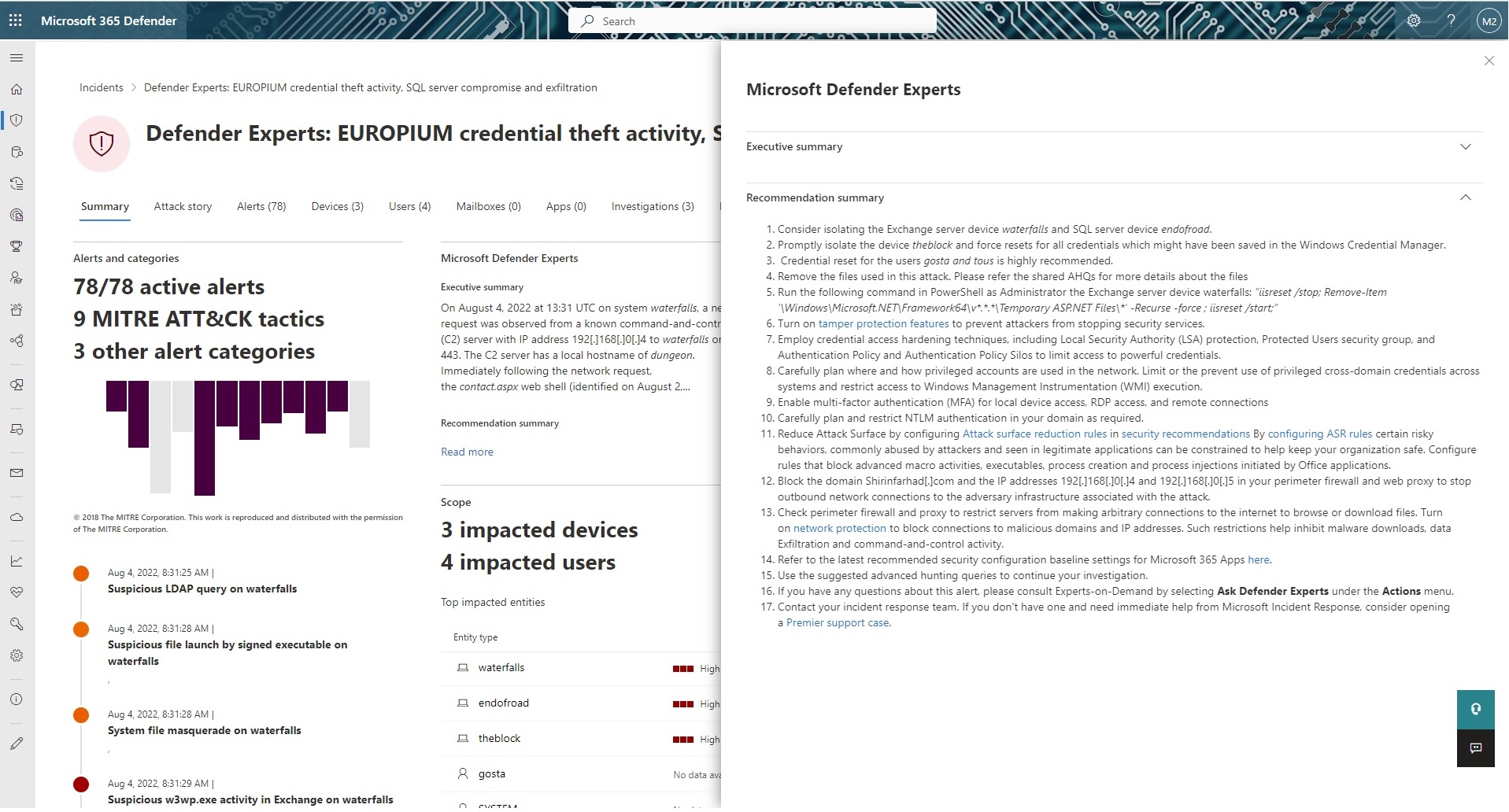
Figure 6. Excerpt of custom recommendations in the Microsoft 365 Defender portal.
Threat actor attribution with TTP context
Microsoft Defender Experts for Hunting provided the customer with nation-state attribution based on observed TTPs and behaviors. We identified the activity was consistent with the threat actor EUROPIUM, also known as APT34 and OilRig, which Microsoft has observed as far back as 2015. EUROPIUM is a well-resourced actor capable of multiple types of attacks—from spear phishing and social engineering to remote exploitation of internet-facing devices.
We leveraged this attribution to provide valuable incident context, such as potential intrusion goals and relevant TTP, to the customer.
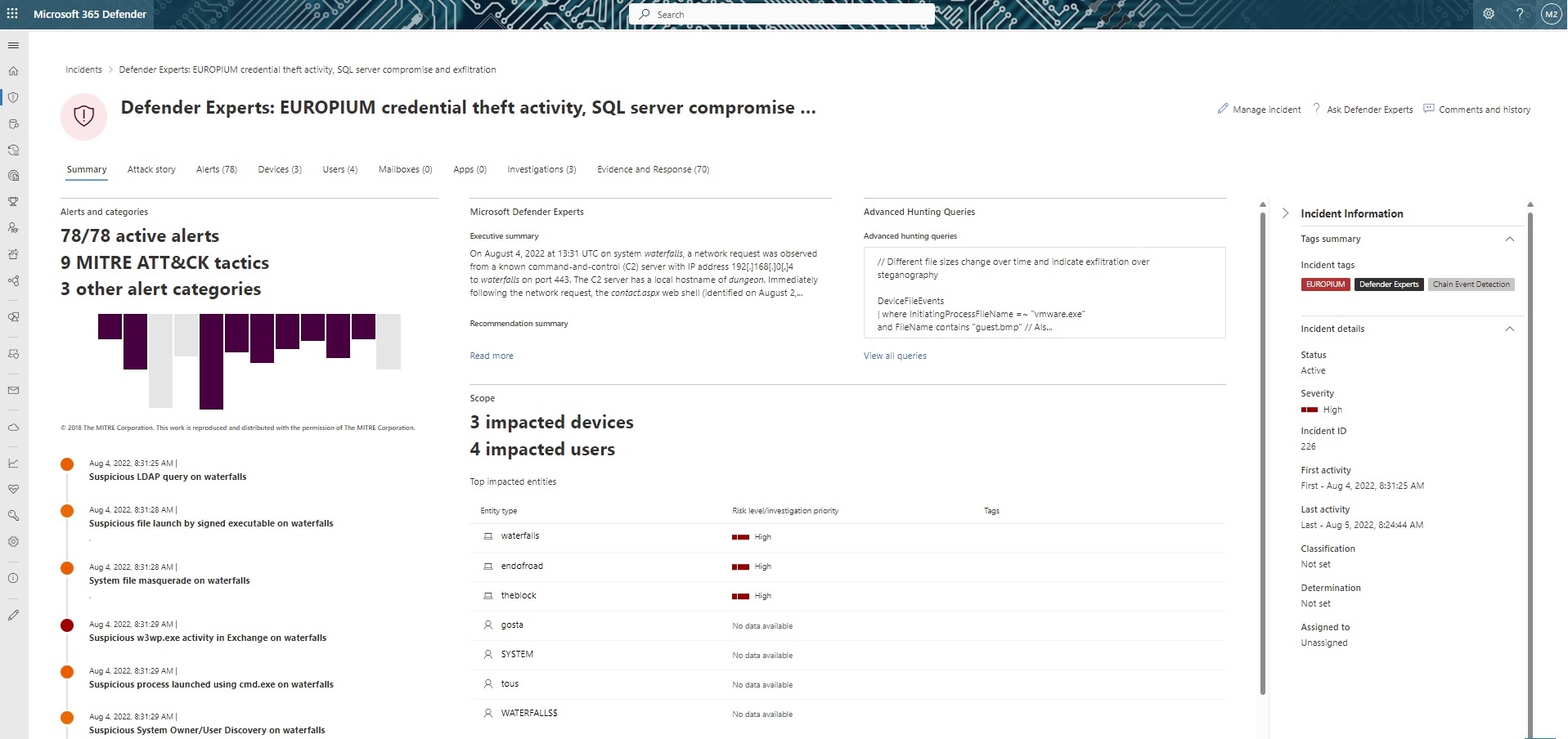
Figure 7. Incident attribution in Microsoft 365 Defender portal.
Technology powered by a team of expert hunters
The Microsoft philosophy in this evaluation was to represent product truth and real-world service delivery for our customers. We participated in the evaluation using our Defender Experts for Hunting team and product capabilities and configurations that we expect customers to use. As you review evaluation results, you should consider additional aspects including depth and durability of protection, completeness of signals, actionable insights, and the quality of what our hunters provided to enrich both the incidents and component alerts. All of these factors are critical in delivering a world-class hunting service to protect real customer production environments.
Commitment to MXDR partners running on Microsoft 365 Defender
Microsoft supported several of our verified MXDR partners in this evaluation. Our collaborative efforts reinforce our commitment to our partners’ success in building managed services to meet growing demand and support our joint customers.
We thank MITRE Engenuity for the opportunity to contribute to and participate in this year’s evaluation.

Read more about the MITRE Managed Services Evaluations.
Learn more
Learn more about Microsoft Defender Experts for Hunting.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
© November 2022 The MITRE Corporation. This work is reproduced and distributed with the permission of The MITRE Corporation.
The post Microsoft Defender Experts for Hunting demonstrates industry-leading protection in the 2022 MITRE Engenuity ATT&CK® Evaluations for Managed Services appeared first on Microsoft Security Blog.
Source: Microsoft Security
