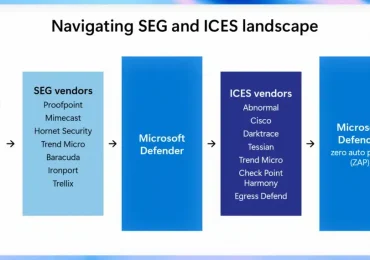
As email threats grow more sophisticated and layered security architectures become more common, organizations need clear, data-driven insights to evaluate[…]
Read More
The Shai‑Hulud 2.0 supply chain attack represents one of the most significant cloud-native ecosystem compromises observed recently. Attackers maliciously modified hundreds[…]
Read More
The Shai‑Hulud 2.0 supply chain attack represents one of the most significant cloud-native ecosystem compromises observed recently. Attackers maliciously modified hundreds[…]
Read More
The Deputy CISO blog series is where Microsoft Deputy Chief Information Security Officers (CISOs) share their thoughts on what is most important in[…]
Read More
The Deputy CISO blog series is where Microsoft Deputy Chief Information Security Officers (CISOs) share their thoughts on what is most important in[…]
Read More
In this article Reenergizing change management with AI Powering AI change management end-to-end Transforming change management at Coca-Cola Beverages Africa[…]
Read More