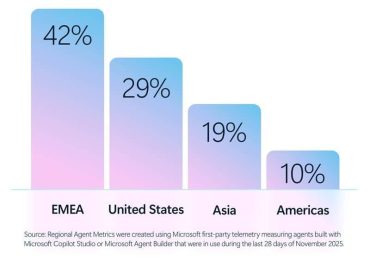
Today, Microsoft is releasing the new Cyber Pulse report to provide leaders with straightforward, practical insights and guidance on new[…]
Leggi di più
That helpful “Summarize with AI” button? It might be secretly manipulating what your AI recommends. Microsoft security researchers have discovered a[…]
Leggi di più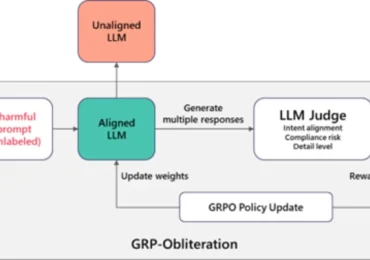
Large language models (LLMs) and diffusion models now power a wide range of applications, from document assistance to text-to-image generation, and users[…]
Leggi di più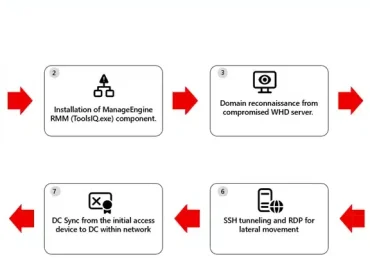
The Microsoft Defender Research Team observed a multi‑stage intrusion where threat actors exploited internet‑exposed SolarWinds Web Help Desk (WHD) instances to[…]
Leggi di più
In January 2026, Microsoft Defender Experts identified a new evolution in the ongoing ClickFix campaign. This updated tactic deliberately crashes[…]
Leggi di più
Today, we’re excited to announce that the new usage page in the Power Platform admin center (PPAC) is available in[…]
Leggi di più
What if your AI agents truly understood your business—your data, your workflows, your goals—and IT could still govern them at[…]
Leggi di piùToday, organizations are being measured by how quickly they can innovate. Whether it’s launching new digital experiences, streamlining operations, or[…]
Leggi di piùWhen building advanced, data‑driven sites on Power Pages, developers often encounter limitations and fragility in standard DOM manipulation. Relying on[…]
Leggi di più
While patchwork tools slow defenders down and impact visibility into potential cyberthreats, they’re an unfortunate reality for many organizations. As[…]
Leggi di piùToday, most organizations use multiple identity systems and multiple network access solutions from multiple vendors. This happens, either intentionally or[…]
Leggi di più
CVE-2025-55182 (also referred to as React2Shell and includes CVE-2025-66478, which was merged into it) is a critical pre-authentication remote code[…]
Leggi di più