Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
Security operations centers are under pressure from unprecedented scale and complexity. Speed, precision, and consistency matter more than ever, and AI is everywhere—but hype alone doesn’t solve the challenge. This blog shares our journey and insights from building autonomous AI agents for MDR operations and explores how the[…]
Read More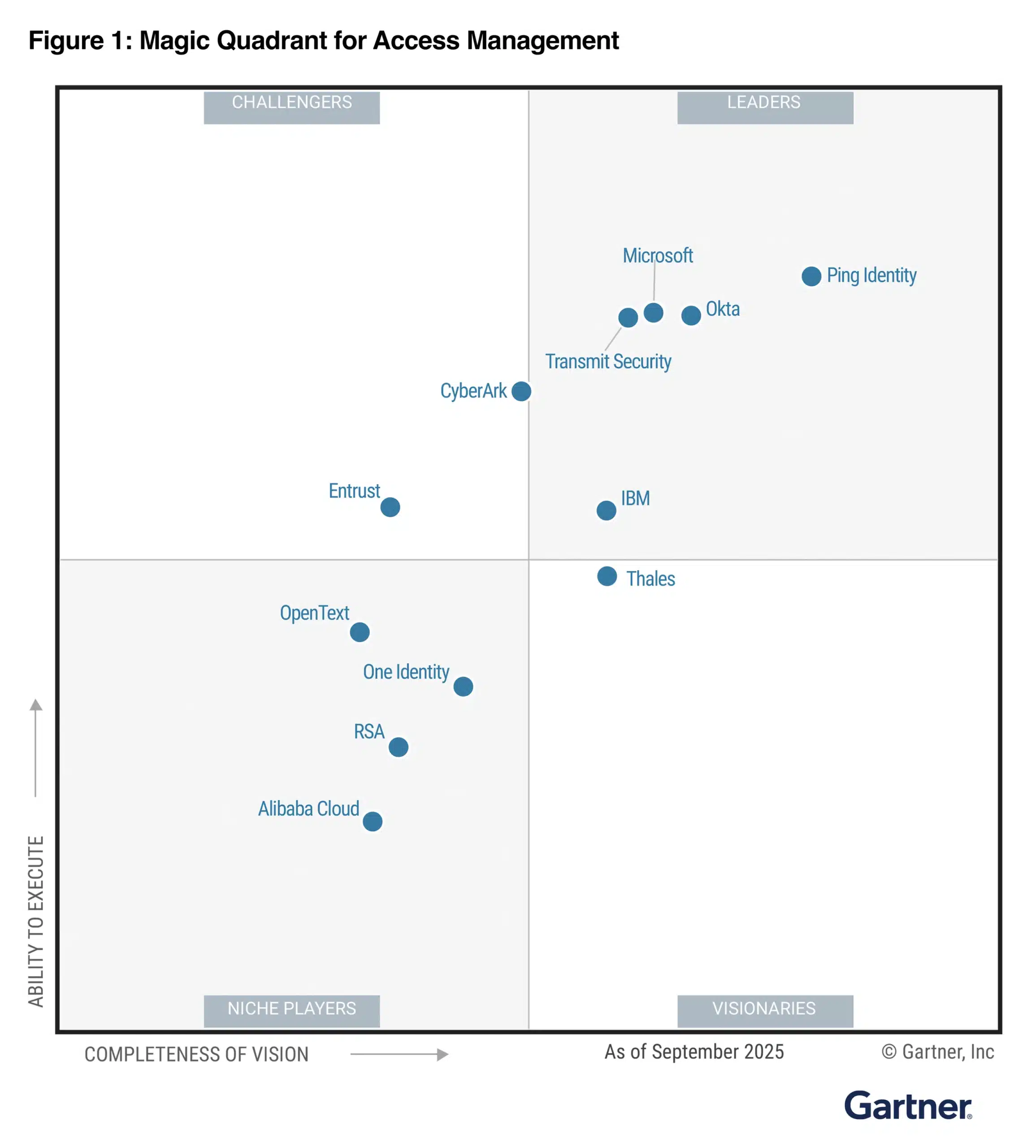
I’m deeply grateful to our customers and partners for their continued trust and collaboration. We’re happy to share that Microsoft has been recognized as a Leader in the 2025 Gartner® Magic Quadrant™ for Access Management for the ninth consecutive year. We feel this recognition underscores the impact and[…]
Read More
Over the past year, I’ve had countless conversations with customers who are striving to unlock human ambition with AI. They are on their journey to become Frontier Firms, where humans and agents push the boundaries of innovation and create new possibilities, empowering humans to become limitless. As agents[…]
Read More
The cybersecurity landscape is at a historic inflection point. As cyberattackers wield AI to automate cyberattacks at extraordinary speed and scale, the challenge before us is not just to keep pace—but to leap ahead. There are over four million unfilled cybersecurity jobs, so depending solely on human resources[…]
Read MoreThis week at Microsoft Ignite 2025, we’re unveiling a new era for Microsoft Power Apps. We are redefining what it means to build with AI with a reimagined experience that makes building apps as intuitive as describing your idea, seamless integration between apps and agents, and the ability[…]
Read More
Today’s leading organizations are going through an agentic business transformation. This change takes AI from concept to measurable impact, by automating existing workflows and using agents to enhance productivity and reinvent entire functions. Copilot Studio, Copilot’s agent platform, provides a fully managed solution for accomplishing this. Using Copilot Studio,[…]
Read MoreAI-Powered Threats Demand AI-Powered Defense While AI supports growth and innovation, it is also reshaping how organizations address faster, more adaptive security risks. AI-driven security threats, including “vibe-hacking”, are evolving faster than traditional defenses can adapt. Attackers can now combine reinforcement learning (RL) with LLM capabilities in code generation, tool use, and multi-step reasoning to create agents[…]
Read MoreWhen we launched the Secure Future Initiative (SFI), our mission was clear: accelerate innovation, strengthen resilience, and lead the industry toward a safer digital future. Today, we’re sharing our latest progress report that reflects steady progress in every area and engineering pillar, underscoring our commitment to security above[…]
Read MoreWhen we launched the Secure Future Initiative (SFI), our mission was clear: accelerate innovation, strengthen resilience, and lead the industry toward a safer digital future. Today, we’re sharing our latest progress report that reflects steady progress in every area and engineering pillar, underscoring our commitment to security above[…]
Read More
Microsoft has discovered a new type of side-channel attack on remote language models. This type of side-channel attack could allow a cyberattacker a position to observe your network traffic to conclude language model conversation topics, despite being end-to-end encrypted via Transport Layer Security (TLS). We have worked with multiple vendors to get the risk[…]
Read More