Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025

Cloud security is at a tipping point. While moving to the cloud powers both growth and speed for organizations, it can also bring new risks. According to IDC’s latest research, organizations experienced an average of nine cloud security incidents in 2024, with 89% reporting a year-over-year increase. That’s[…]
Read More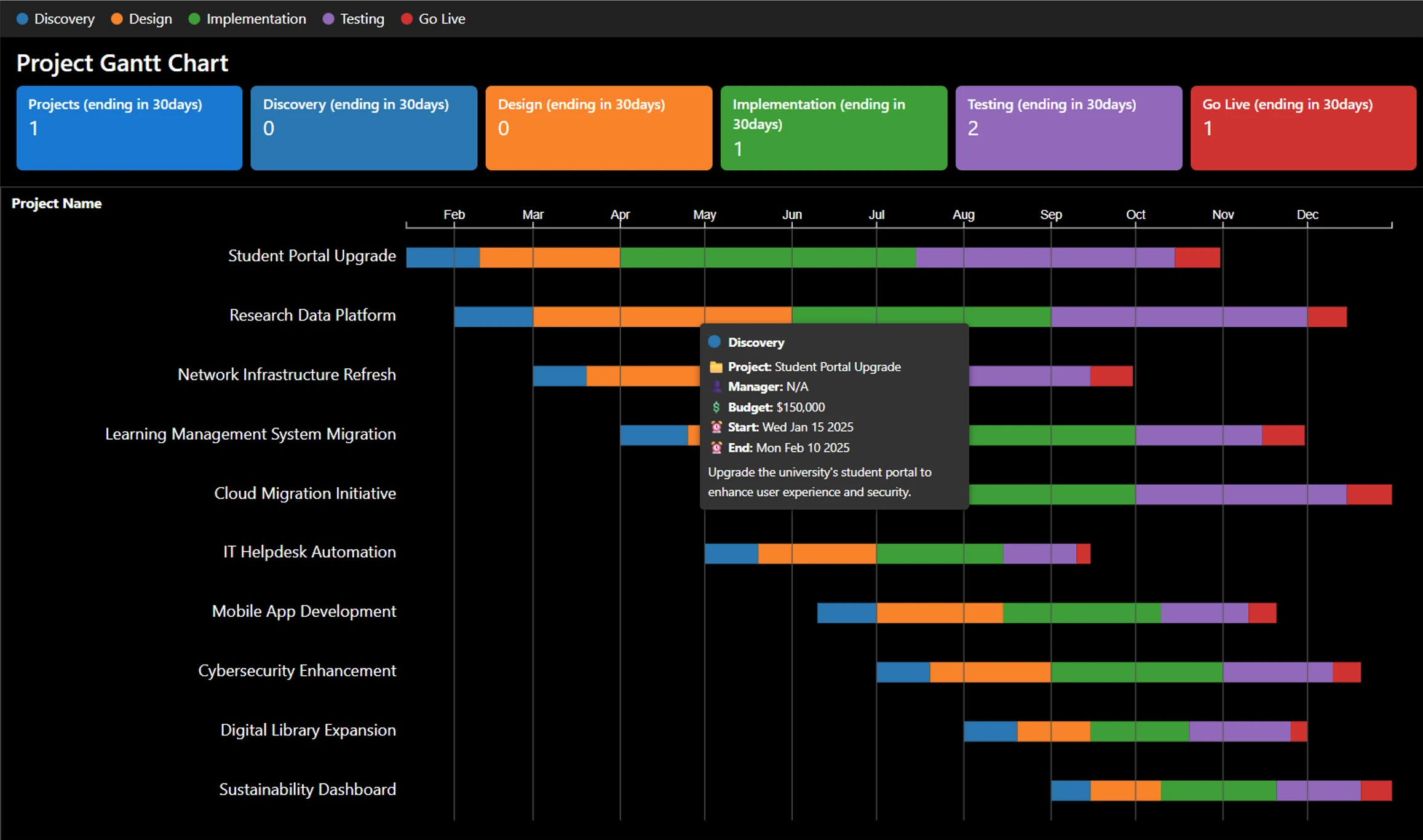
We’re excited to announce that generative pages in Power Apps is now generally available in the U.S. This milestone brings AI-powered page creation in model-driven apps into hands of more makers, enabling them to build rich, responsive experiences for new and existing apps fast. Designed specifically for model-driven[…]
Read More
The Deputy CISO blog series is where Microsoft Deputy Chief Information Security Officers (CISOs) share their thoughts on what is most important in their respective domains. In this series, you will get practical advice, tactics to start (and stop) deploying, forward-looking commentary on where the industry is going, and more. In[…]
Read More
The busier security teams get, the harder it can be to understand the full impact of false positives, queue clutter, tool fragmentation, and more. But what is clear—it all adds up to increased fatigue and an increased potential to miss the cyberthreats that matter most. To help security[…]
Read More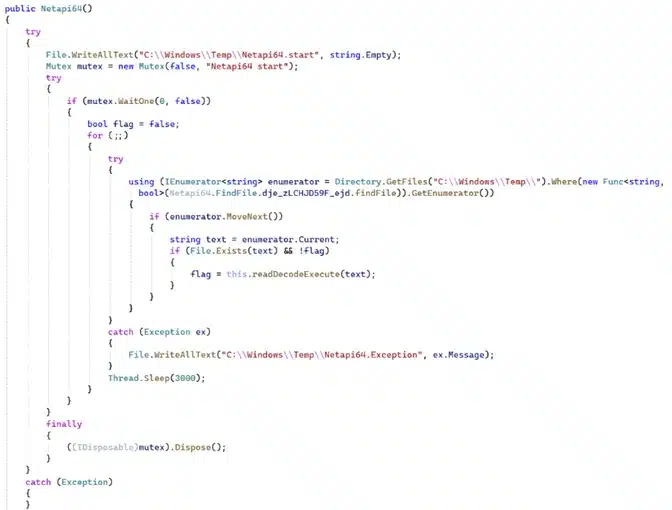
Microsoft Incident Response – Detection and Response Team (DART) researchers uncovered a new backdoor that is notable for its novel use of the OpenAI Assistants Application Programming Interface (API) as a mechanism for command-and-control (C2) communications. Instead of relying on more traditional methods, the threat actor behind this[…]
Read More
Generative AI is reshaping the way security teams operate—accelerating threat detection, automating workflows, and enabling scale. But as defenders embrace AI to strengthen their posture, cyberattackers are doing the same to evolve faster than traditional defenses can adapt. Microsoft’s 2025 Digital Threats Report revealed that cyberattackers like Russia,[…]
Read More
Generative AI is reshaping the way security teams operate—accelerating threat detection, automating workflows, and enabling scale. But as defenders embrace AI to strengthen their posture, cyberattackers are doing the same to evolve faster than traditional defenses can adapt. Microsoft’s 2025 Digital Threats Report revealed that cyberattackers like Russia,[…]
Read More
This year’s Power Platform Community Conference (PPCC 2025) was nothing short of extraordinary. Over 7,000 makers, developers, and partners came together to explore the future of innovation, share inspiring stories, and strengthen the bonds that make this community so special. Behind every innovation is a maker, someone who[…]
Read More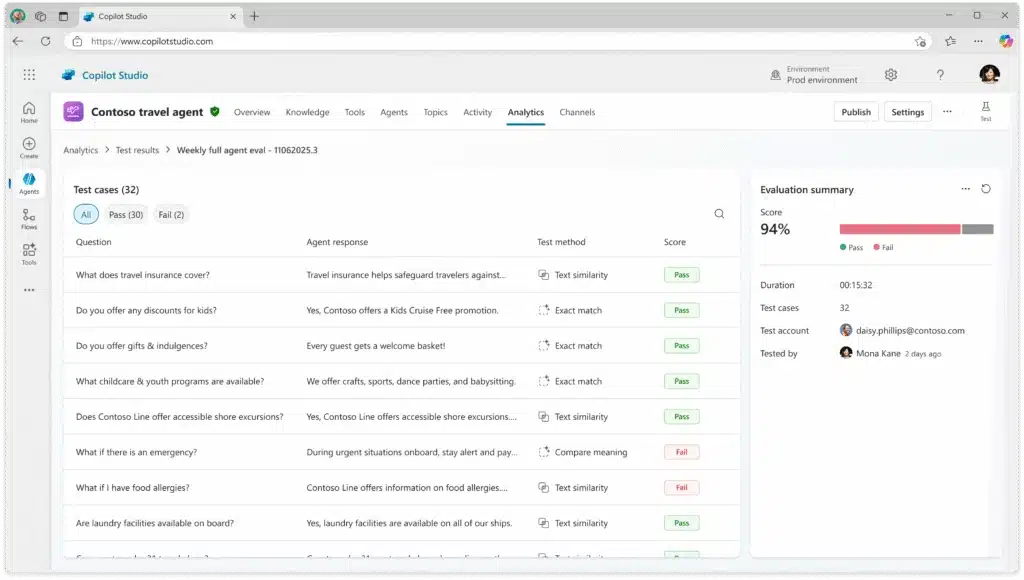
As AI agents take on critical roles in business processes, the need for reliable, repeatable testing becomes essential. In the past, agents have been manually tested—typing in questions, hoping for the right answers, and troubleshooting inconsistencies case by case. That time consuming, unscalable, and inconsistent approach that relies[…]
Read More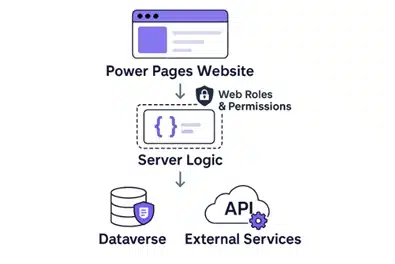
We are happy to announce the new server logic feature in Power Pages to execute business logic securely on the server to build connected, compliant, and intelligent web experiences. Forget the days of jumping through hoops to call external APIs, orchestrate complex actions or securely handle sensitive tasks.[…]
Read More