Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- 80% of Fortune 500 use active AI Agents: Observability, governance, and security shape the new frontier 10 Febbraio 2026
- Manipulating AI memory for profit: The rise of AI Recommendation Poisoning 10 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- A one-prompt attack that breaks LLM safety alignment 9 Febbraio 2026
- Analysis of active exploitation of SolarWinds Web Help Desk 7 Febbraio 2026
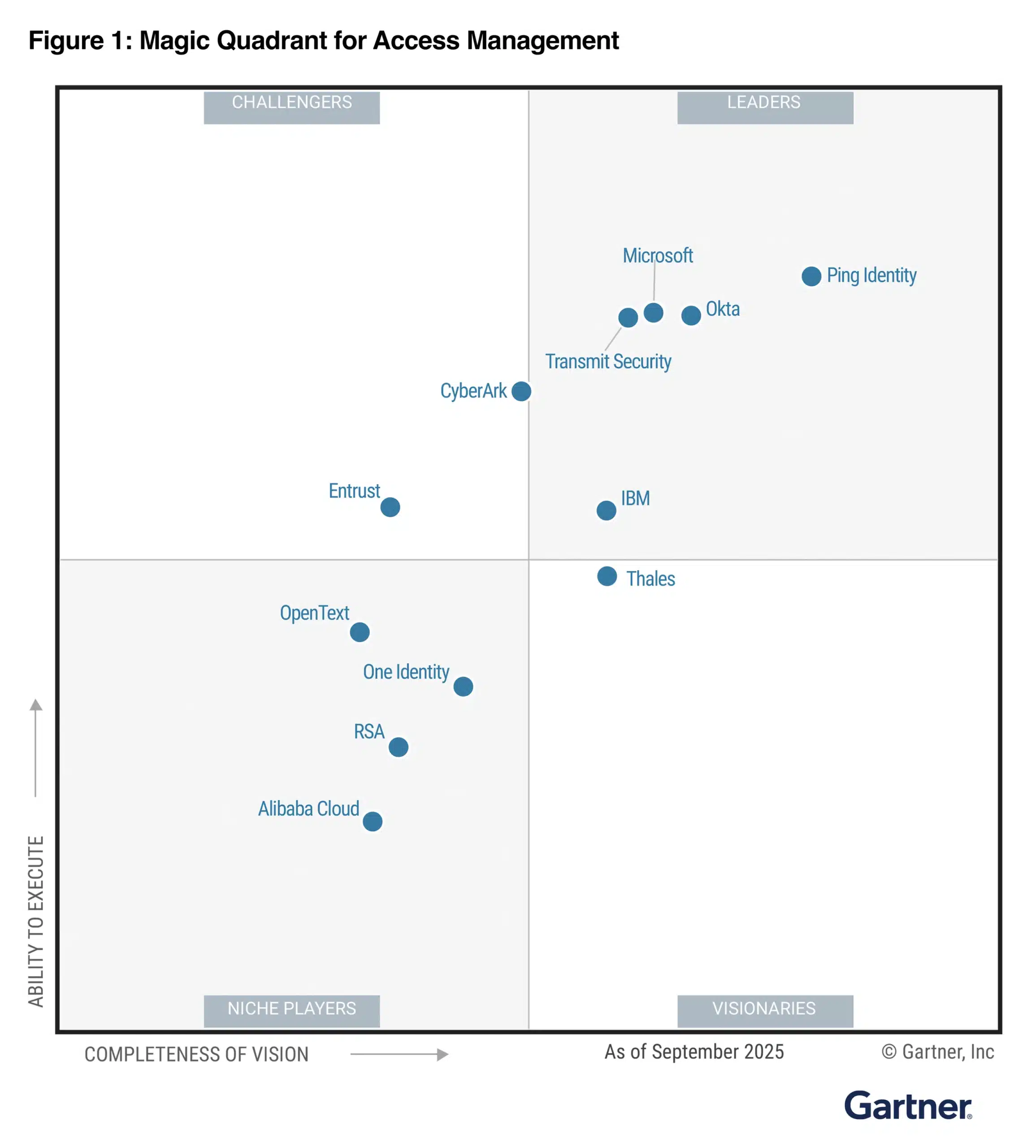
I’m deeply grateful to our customers and partners for their continued trust and collaboration. We’re happy to share that Microsoft has been recognized as a Leader in the 2025 Gartner® Magic Quadrant™ for Access Management for the ninth consecutive year. We feel this recognition underscores the impact and[…]
Read More
Over the past year, I’ve had countless conversations with customers who are striving to unlock human ambition with AI. They are on their journey to become Frontier Firms, where humans and agents push the boundaries of innovation and create new possibilities, empowering humans to become limitless. As agents[…]
Read More
The cybersecurity landscape is at a historic inflection point. As cyberattackers wield AI to automate cyberattacks at extraordinary speed and scale, the challenge before us is not just to keep pace—but to leap ahead. There are over four million unfilled cybersecurity jobs, so depending solely on human resources[…]
Read MoreThis week at Microsoft Ignite 2025, we’re unveiling a new era for Microsoft Power Apps. We are redefining what it means to build with AI with a reimagined experience that makes building apps as intuitive as describing your idea, seamless integration between apps and agents, and the ability[…]
Read More
Today’s leading organizations are going through an agentic business transformation. This change takes AI from concept to measurable impact, by automating existing workflows and using agents to enhance productivity and reinvent entire functions. Copilot Studio, Copilot’s agent platform, provides a fully managed solution for accomplishing this. Using Copilot Studio,[…]
Read MoreAI-Powered Threats Demand AI-Powered Defense While AI supports growth and innovation, it is also reshaping how organizations address faster, more adaptive security risks. AI-driven security threats, including “vibe-hacking”, are evolving faster than traditional defenses can adapt. Attackers can now combine reinforcement learning (RL) with LLM capabilities in code generation, tool use, and multi-step reasoning to create agents[…]
Read MoreWhen we launched the Secure Future Initiative (SFI), our mission was clear: accelerate innovation, strengthen resilience, and lead the industry toward a safer digital future. Today, we’re sharing our latest progress report that reflects steady progress in every area and engineering pillar, underscoring our commitment to security above[…]
Read MoreWhen we launched the Secure Future Initiative (SFI), our mission was clear: accelerate innovation, strengthen resilience, and lead the industry toward a safer digital future. Today, we’re sharing our latest progress report that reflects steady progress in every area and engineering pillar, underscoring our commitment to security above[…]
Read More
Microsoft has discovered a new type of side-channel attack on remote language models. This type of side-channel attack could allow a cyberattacker a position to observe your network traffic to conclude language model conversation topics, despite being end-to-end encrypted via Transport Layer Security (TLS). We have worked with multiple vendors to get the risk[…]
Read More
Cloud security is at a tipping point. While moving to the cloud powers both growth and speed for organizations, it can also bring new risks. According to IDC’s latest research, organizations experienced an average of nine cloud security incidents in 2024, with 89% reporting a year-over-year increase. That’s[…]
Read More