Notizie per Categorie
Articoli Recenti
- Unveiling RIFT: Enhancing Rust malware analysis through pattern matching 27 Giugno 2025
- [Launched] Generally Available: Azure FXv2-series Virtual Machines 26 Giugno 2025
- [In preview] Public Preview: Draft & Deploy on Azure Firewall 26 Giugno 2025
- [Launched] Generally Available: Azure Virtual Network Manager IP address management 26 Giugno 2025
- [Launched] Generally Available: Transition existing platform-managed keys (PMK) to customer-managed keys (CMK) for Azure NetApp Files volumes without data migration. 26 Giugno 2025
- Building security that lasts: Microsoft’s journey towards durability at scale 26 Giugno 2025
- [In preview] Public Preview: Monitor ingestion issues with Azure Monitor Workspace 26 Giugno 2025
- Power Pages Home Action Center Is Generally Available – Stay Informed, Stay in Control 26 Giugno 2025
- Microsoft Named a Leader in the 2025 IDC CNAPP MarketScape: Key Takeaways for Security Buyers 25 Giugno 2025
- From potholes to personalization: What Abu Dhabi is teaching us about AI-powered smart cities 25 Giugno 2025
Microsoft’s 2025 Work Trend Index Read more ↗ Agentic AI transformation is giving rise to the Frontier Firm—a new type of organization characterized by on-demand intelligence and a workforce where humans and agents work in tandem. According to Microsoft’s 2025 Work Trend Index, we expect every organization will[…]
Read More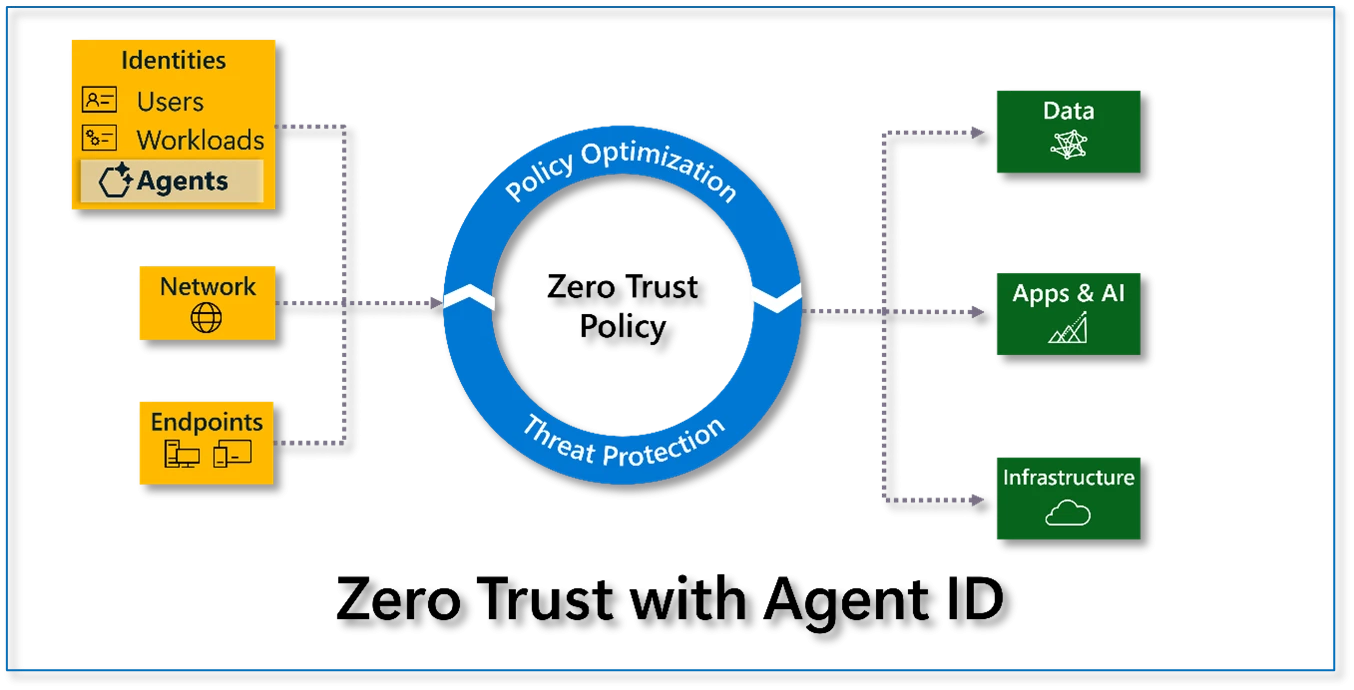
Microsoft’s 2025 Work Trend Index Read more ↗ Agentic AI transformation is giving rise to the Frontier Firm—a new type of organization characterized by on-demand intelligence and a workforce where humans and agents work in tandem. According to Microsoft’s 2025 Work Trend Index, we expect every organization will[…]
Read MoreAs we transition to a world where work is increasingly done through human collaboration with agents, the way we think about applications is changing dramatically. Microsoft Power Apps is at the center of evolving how we build agent-centric apps, what it means to use them, and how we[…]
Read More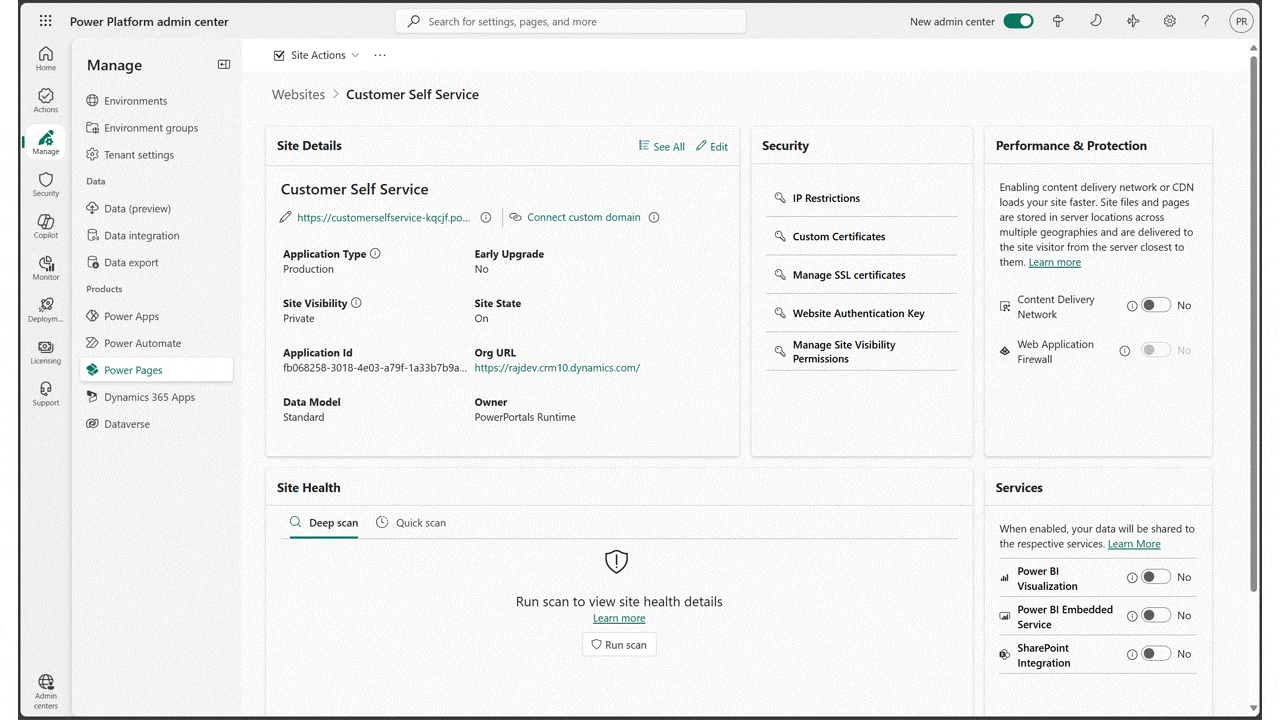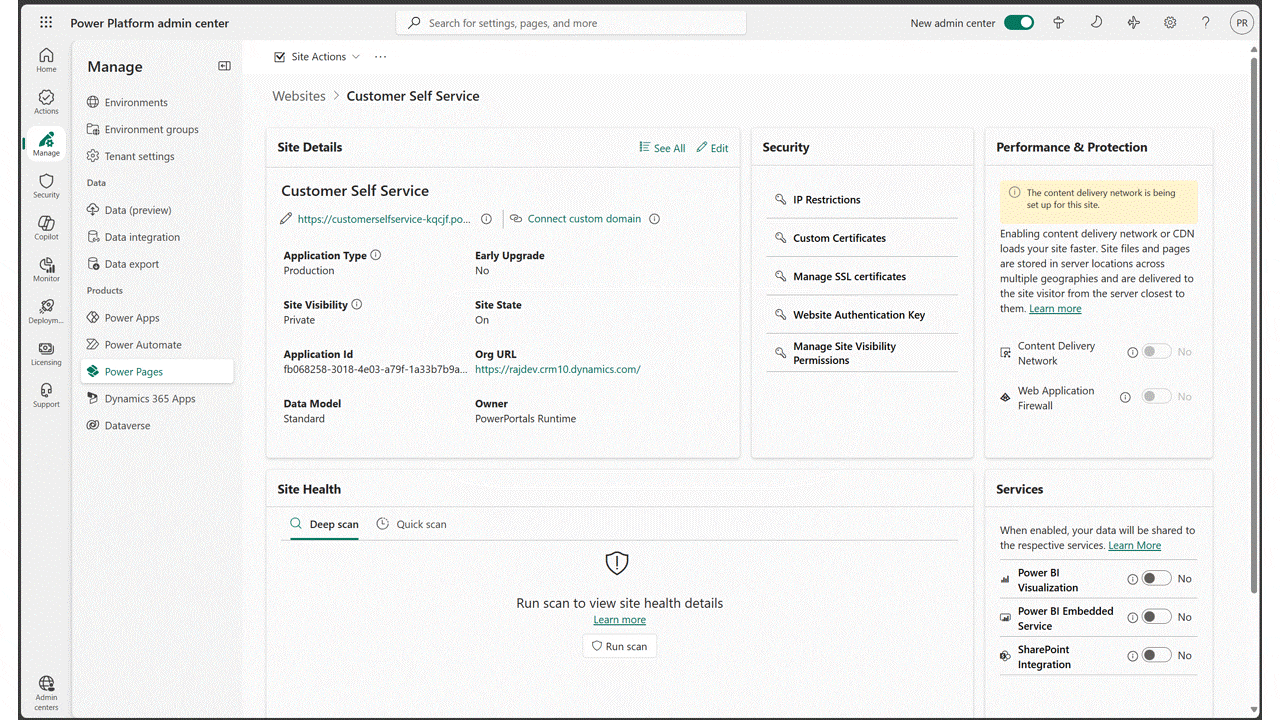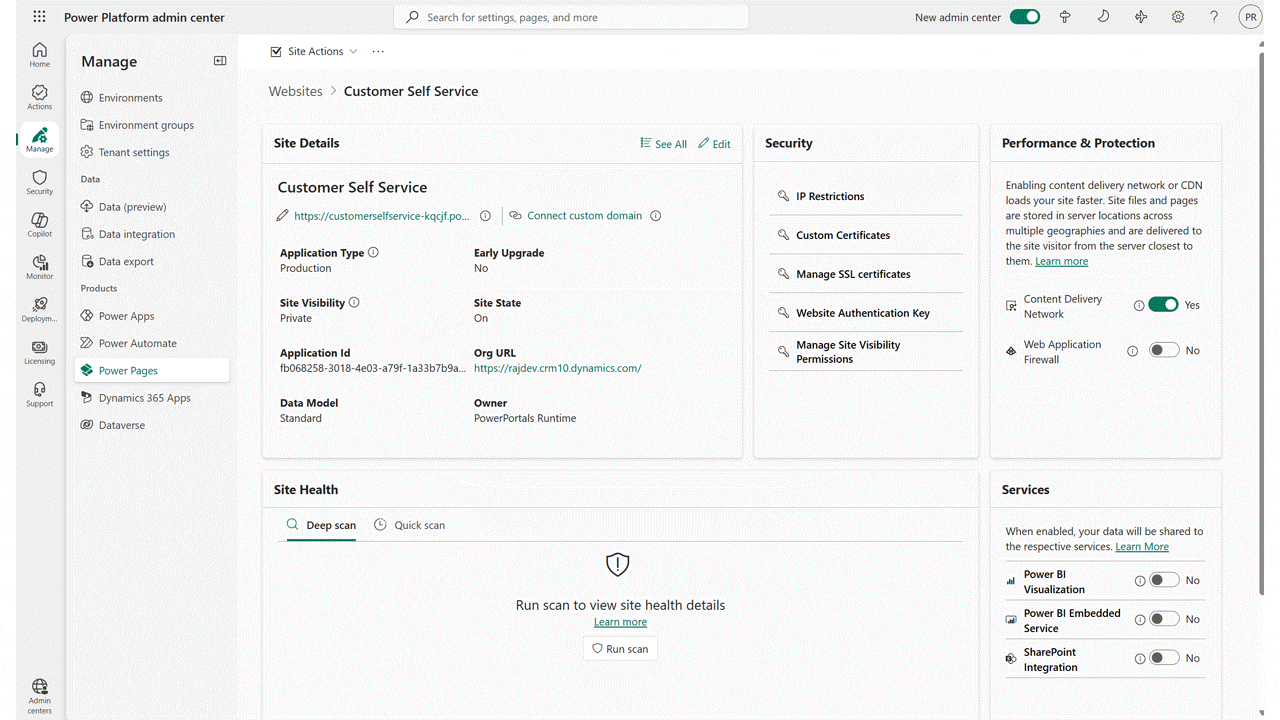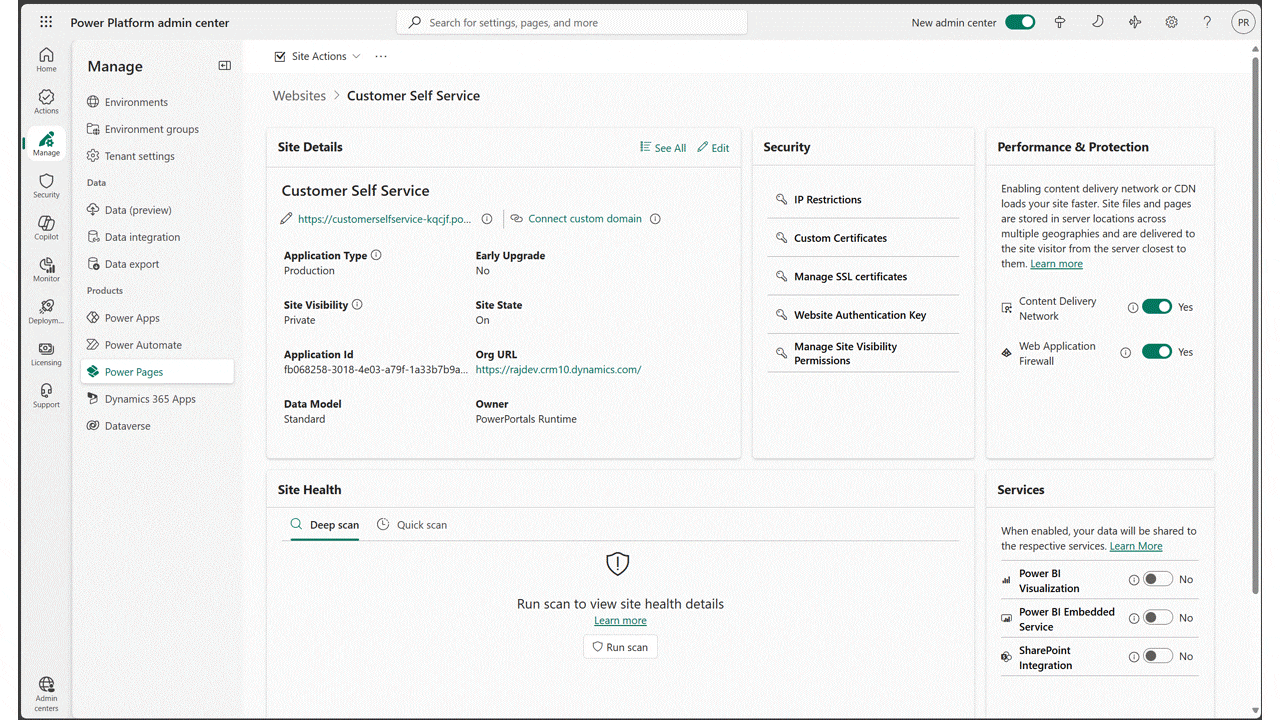
We’re excited to announce that Content Delivery Network and Web Application Firewall features are now available in the US Government Cloud for Power Pages. Content Delivery Network (CDN) CDN for Power Pages helps significantly improve website performance by delivering web content from servers closer to your site users.[…]
Read More
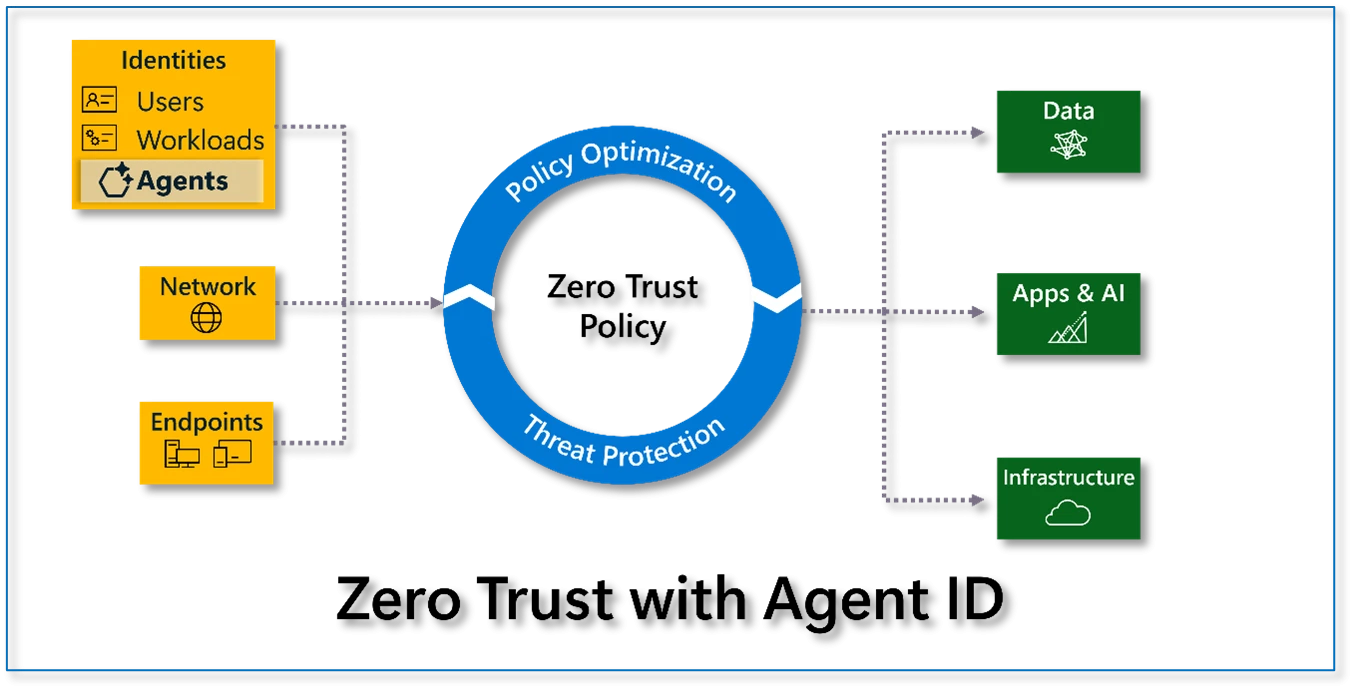
In this blog, you’ll learn more about how the Microsoft Secure Future Initiative (SFI)—a real-world case study on Zero Trust—aligns with Zero Trust strategies. We’ll share key updates from the April 2025 SFI progress report and practical Zero Trust guidance to help you strengthen your organization’s security posture.[…]
Read More
As we gear up for Microsoft Build 2025, excitement is building around the latest advancements in agent governance, security, and management. This year, we’re bringing you groundbreaking insights and tools to enhance your experience with Microsoft Copilot and ensure robust governance and security for your AI agents. Join[…]
Read More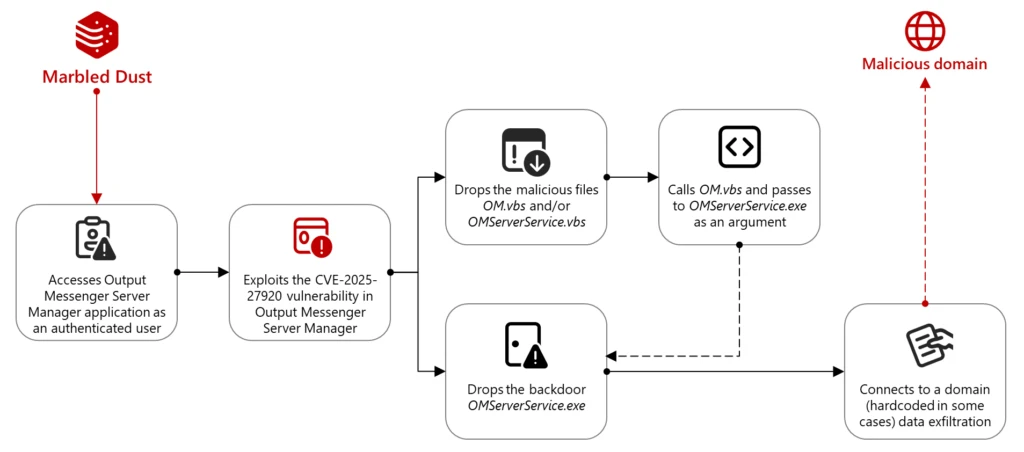
Since April 2024, the threat actor that Microsoft Threat Intelligence tracks as Marbled Dust has been observed exploiting user accounts that have not applied fixes to a zero-day vulnerability (CVE-2025-27920) in the messaging app Output Messenger, a multiplatform chat software. These exploits have resulted in collection of related[…]
Read More
Microsoft launched its Cybersecurity Governance Council in 2024, and with it, named a group of deputy chief information security officers that ensure comprehensive oversight of the company’s cybersecurity risk, defense, and compliance. These leaders work in tandem with product and engineering leaders across the company to create accountability[…]
Read MoreBeing the victim of a scam can be devastating. Unfortunately, the number of people who can attest to the truth of this statement, either because they themselves have been scammed or because it has happened to someone they know, is growing. The Global Anti-Scam Alliance (GASA) reports that[…]
Read More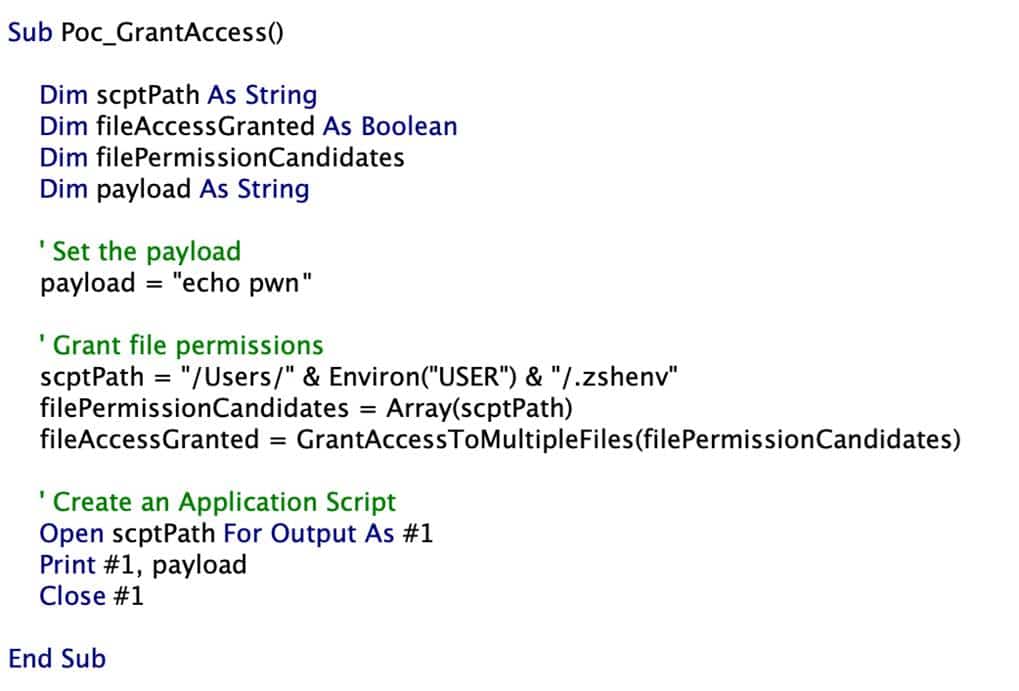
In April 2024, Microsoft uncovered a vulnerability in macOS that could allow specially crafted codes to escape the App Sandbox and run unrestricted on the system. An attacker could create an exploit to escape the App Sandbox without user interaction required for any sandboxed app using security-scoped bookmarks.[…]
Read More