Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025

In a world where the digital frontier is expanding and cyberattacks are becoming more sophisticated with speed and scale, the guardians of our virtual realms have never been in greater demand.1 It’s important to leverage this year’s Cybersecurity Awareness Month to celebrate the people who keep us safe[…]
Read More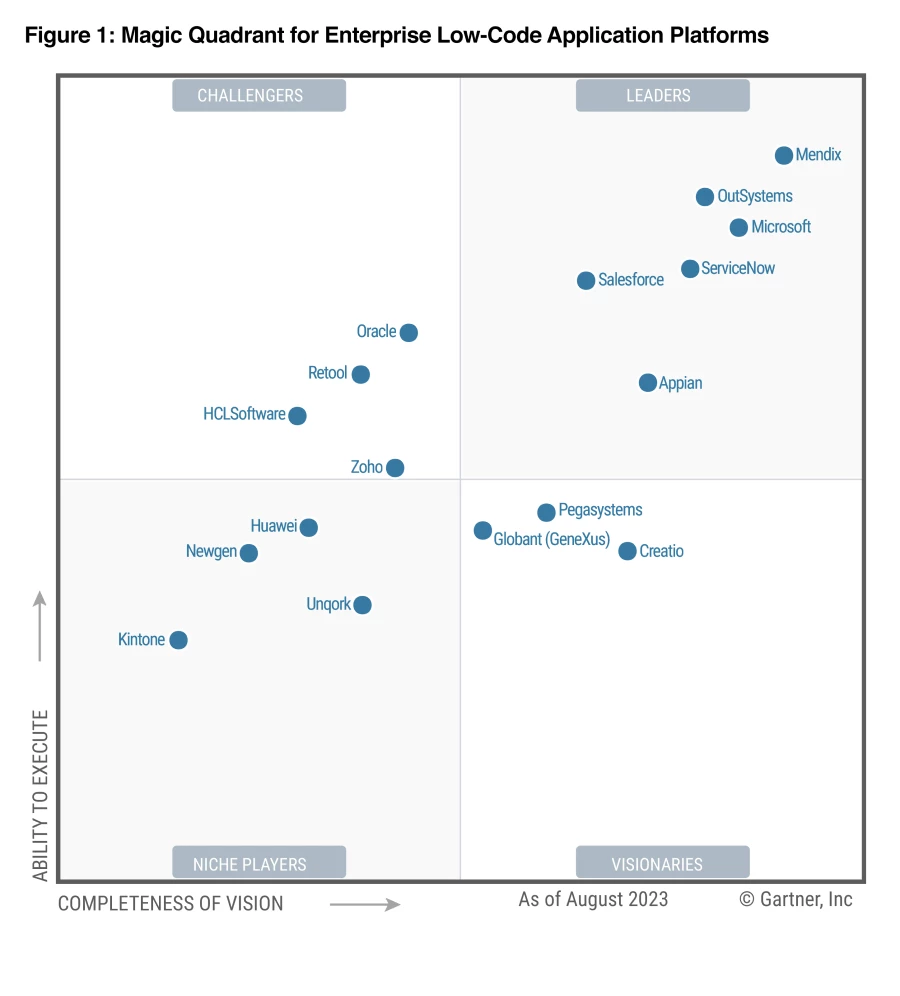
Source: Gartner (August 2023)* We are thrilled to announce that for the fifth time in a row, Microsoft has been named a Leader in the 2023 Gartner® Magic Quadrant™ for Enterprise Low-Code Application Platforms**. Microsoft Power Apps is enabling developers of all kinds to innovate and create solutions[…]
Read More
Today Microsoft Incident Response is excited to announce a new collaboration with PwC to expand our joint incident response and recovery capability. In this global alliance, Microsoft begins the initial containment and investigation, bringing a deep understanding of a company’s infrastructure to help evict the bad actors faster and[…]
Read More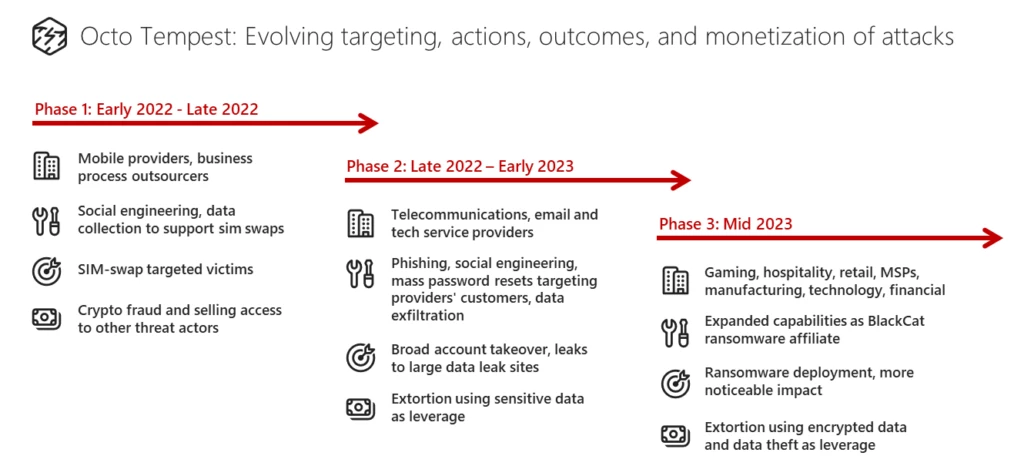
Microsoft has been tracking activity related to the financially motivated threat actor Octo Tempest, whose evolving campaigns represent a growing concern for organizations across multiple industries. Octo Tempest leverages broad social engineering campaigns to compromise organizations across the globe with the goal of financial extortion. With their extensive[…]
Read More
A whopping 74 percent of organizations recently surveyed experienced at least one data security incident with their business data exposed in the previous year. That’s just one of our interesting insights from Microsoft’s new Data Security Index: Trends, insights, and strategies to secure data report, released today. […]
Read More
Today, at the Microsoft Business Applications Launch Event, we kicked off the 2023 release wave 2 for Microsoft Dynamics 365 and Microsoft Power Platform, a six-month rollout of new and enhanced capabilities scheduled for release between October 2023 and March 2024. This release wave introduces hundreds of new[…]
Read More
We are excited to share that Microsoft has been named a Leader in The Forrester Wave™: Endpoint Security, Q4 2023. Microsoft received the highest possible scores in the strategy category for the vision and roadmap criteria. Forrester notes, “Microsoft’s outstanding roadmap for endpoint security includes expanding [Microsoft Defender[…]
Read More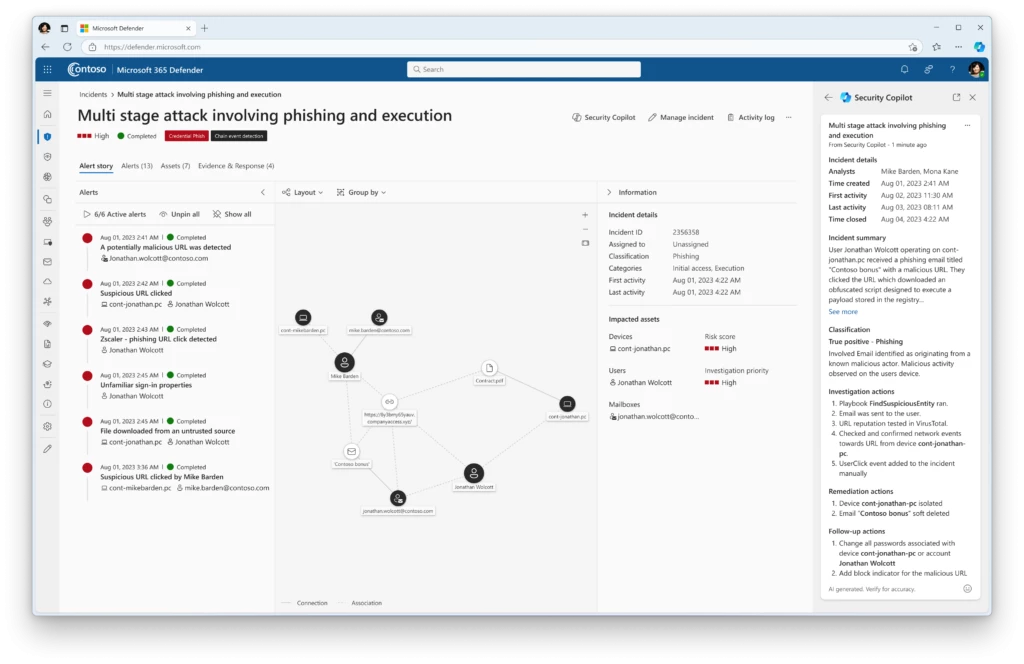
The era of AI brings unprecedented opportunities for us, and at the same time we are also facing an unprecedented surge in cyberthreats, coupled with a global shortage of security experts. Security and safety is the defining challenge of our times and protecting organizations from cybercrime has only[…]
Read More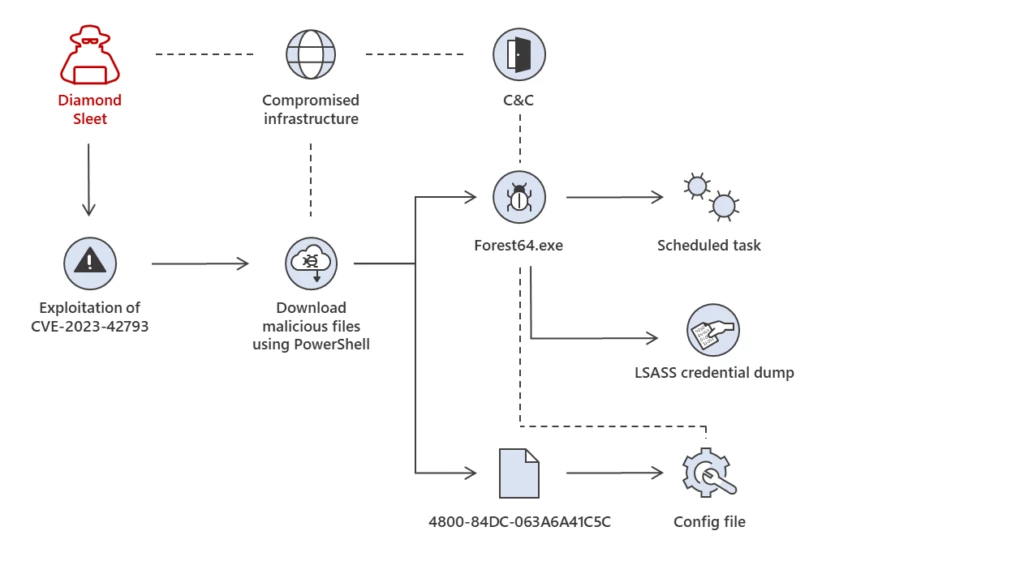
Since early October 2023, Microsoft has observed two North Korean nation-state threat actors – Diamond Sleet and Onyx Sleet – exploiting CVE-2023-42793, a remote-code execution vulnerability affecting multiple versions of JetBrains TeamCity server. TeamCity is a continuous integration/continuous deployment (CI/CD) application used by organizations for DevOps and other[…]
Read More
Since our announcement in July 2023, we have made significant efforts to enhance the access to Microsoft Purview’s audit logging.1 This ongoing work expands accessibility and flexibility to cloud security logs, which began rolling out to customers around the world in September 2023. Our decision to update the[…]
Read More