Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025

The Deputy CISO blog series is where Microsoft Deputy Chief Information Security Officers (CISOs) share their thoughts on what is most important in their respective domains. In this series, you will get practical advice, tactics to start (and stop) deploying, forward-looking commentary on where the industry is going, and more. In[…]
Read More
The Deputy CISO blog series is where Microsoft Deputy Chief Information Security Officers (CISOs) share their thoughts on what is most important in their respective domains. In this series, you will get practical advice, tactics to start (and stop) deploying, forward-looking commentary on where the industry is going, and more. In[…]
Read More
Today’s cyberthreat landscape demands more than technical expertise: it requires a unified response team of technical responders, insurers, brokers, and legal counsel. This integrated approach is key to building long-term cyber resilience to help your organization anticipate, withstand, recover from, and adapt to cyberattacks. It’s not just about strong defenses, but how quickly and effectively you respond to an[…]
Read More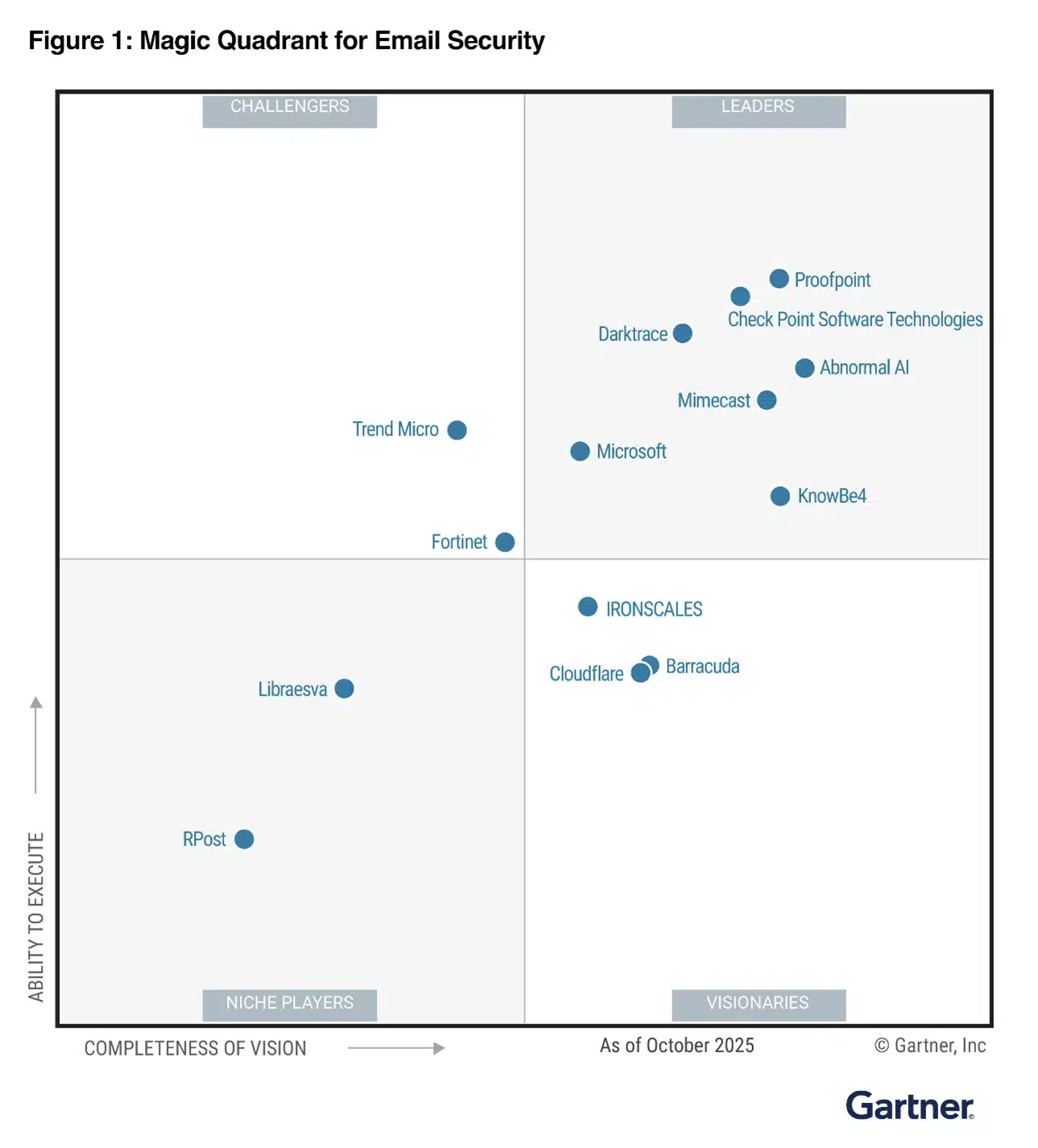
We’re honored to share that Microsoft has been named a Leader in the 2025 Gartner® Magic Quadrant™ for Email Security. We believe this recognition highlights the value of Microsoft Defender for Office 365’s innovative capabilities in addressing today’s complex email security challenges. Protect against the latest email security[…]
Read More
Business as we know it is changing. Competitive advantage is shifting toward organizations that can harness AI to fundamentally changing the patterns of how work gets done. This enables frontier firms to innovate faster, reduce friction in execution, and dynamically respond to changing conditions in real time. We[…]
Read More
Business as we know it is changing. Competitive advantage is shifting toward organizations that can harness AI to fundamentally changing the patterns of how work gets done. This enables frontier firms to innovate faster, reduce friction in execution, and dynamically respond to changing conditions in real time. We[…]
Read More
The Deputy CISO blog series is where Microsoft Deputy Chief Information Security Officers (CISOs) share their thoughts on what is most important in their respective domains. In this series, you will get practical advice, tactics to start (and stop) deploying, forward-looking commentary on where the industry is going, and more. In this[…]
Read More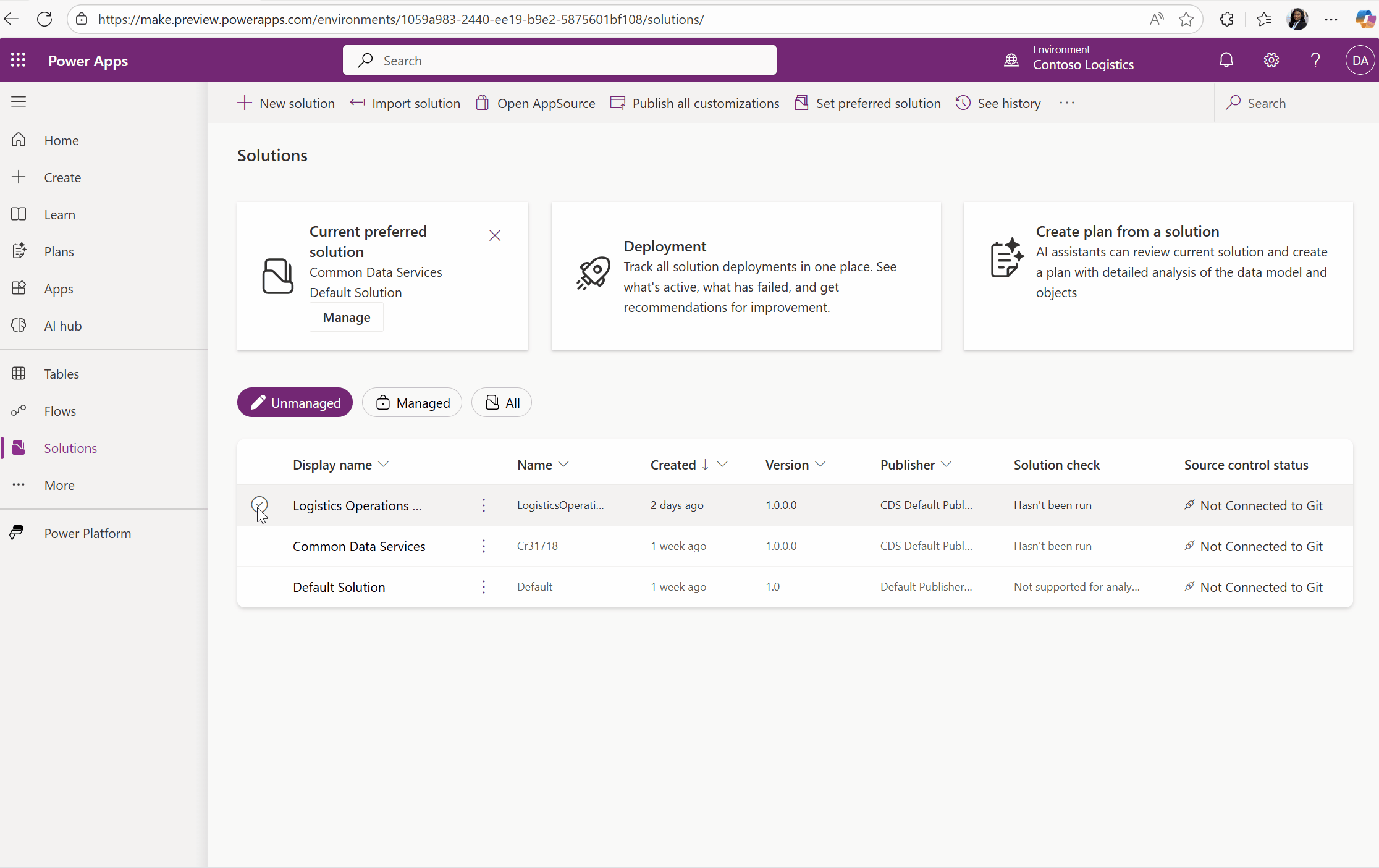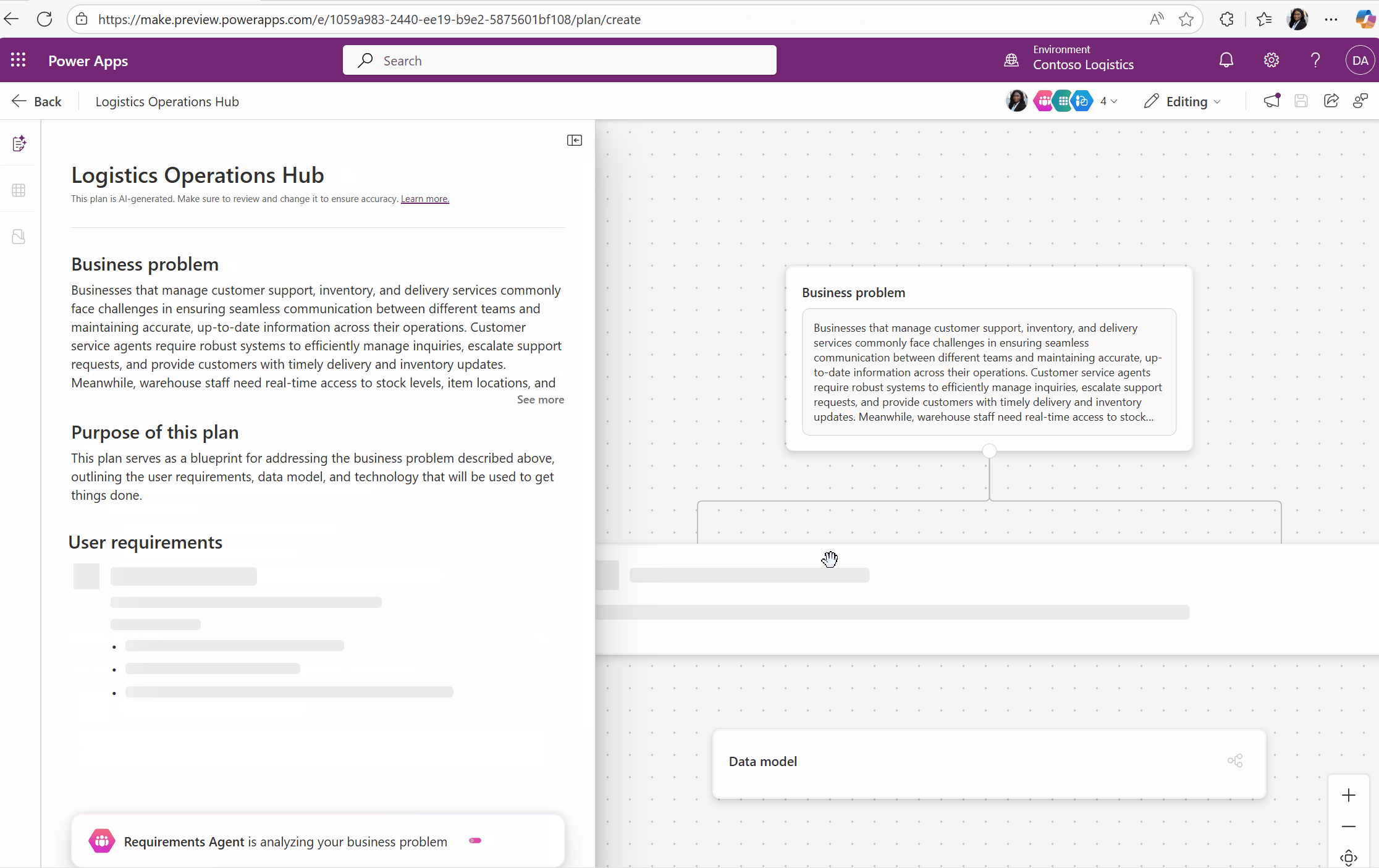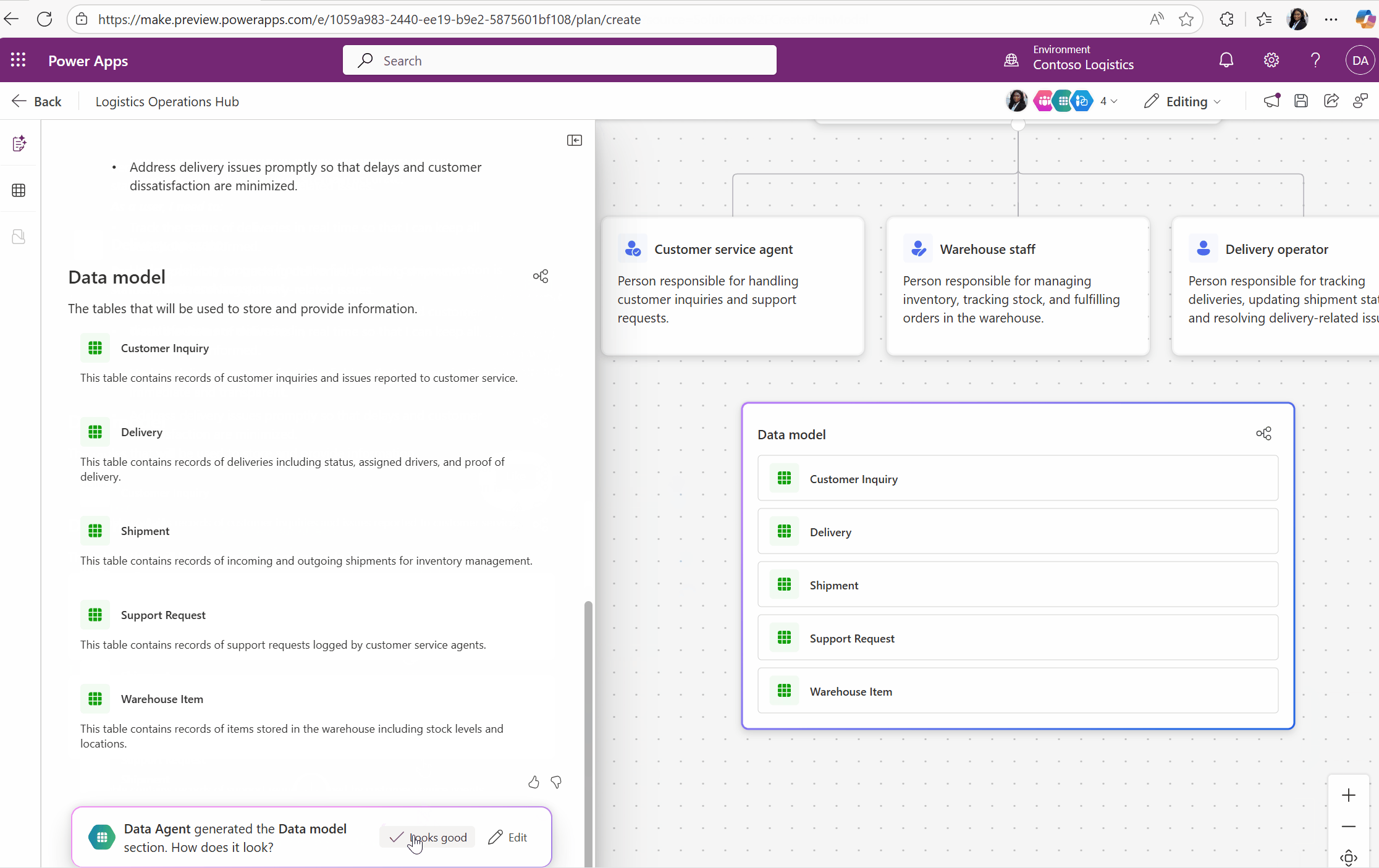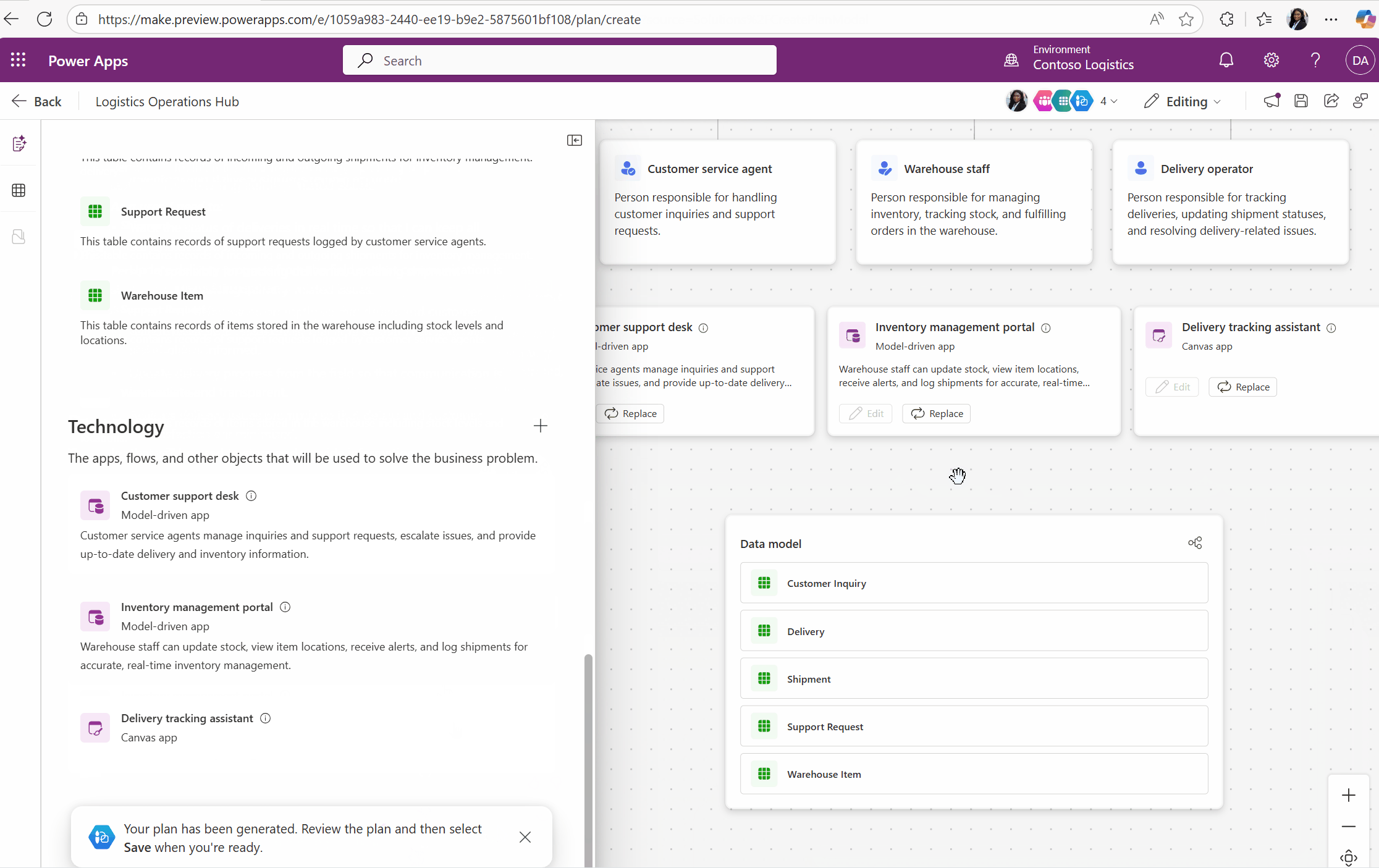
Building solutions in Power Apps is all about speed, flexibility, and innovation. But what happens when you need to revisit an existing solution—maybe to enhance it, document it, or share its design with stakeholders? Traditionally, this meant manually analyzing apps, tables, and flows to piece together the bigger[…]
Read MoreEmpowering Data Scientists and Developers to unlock Advanced Analytics, Automation, and Innovation With the open-source Dataverse SDK for Python (announced in Public Preview at Microsoft Ignite 2025), you can fully harness the power of Dataverse business data. This toolkit enables advanced analytics, streamlines automation, and fuels innovation by[…]
Read More
We are witnessing something unprecedented in cybersecurity: the democratization of advanced cyberattack capabilities. What once required nation-state resources (sophisticated social engineering, polymorphic malware, coordinated infrastructure) now fits in a prompt window. AI is no longer a futuristic concept but a present-day reality—fundamentally reshaping the rules of both offense[…]
Read More