Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
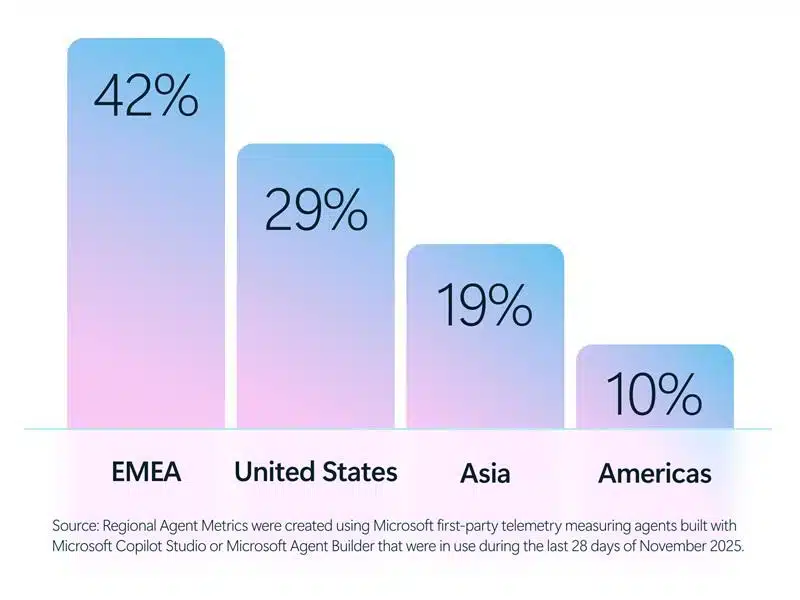
- 80% of Fortune 500 use active AI Agents: Observability, governance, and security shape the new frontier 10 Febbraio 2026
- Manipulating AI memory for profit: The rise of AI Recommendation Poisoning 10 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- A one-prompt attack that breaks LLM safety alignment 9 Febbraio 2026
- Analysis of active exploitation of SolarWinds Web Help Desk 7 Febbraio 2026
Today, Microsoft is releasing the new Cyber Pulse report to provide leaders with straightforward, practical insights and guidance on new cybersecurity risks. One of today’s most pressing concerns is the governance of AI and autonomous agents. AI agents are scaling faster than some companies can see them—and that[…]
Read More
That helpful “Summarize with AI” button? It might be secretly manipulating what your AI recommends. Microsoft security researchers have discovered a growing trend of AI memory poisoning attacks used for promotional purposes, a technique we call AI Recommendation Poisoning. Companies are embedding hidden instructions in “Summarize with AI” buttons that,[…]
Read More
Large language models (LLMs) and diffusion models now power a wide range of applications, from document assistance to text-to-image generation, and users increasingly expect these systems to be safety-aligned by default. Yet safety alignment is only as robust as its weakest failure mode. Despite extensive work on safety post-training, it[…]
Read More
The Microsoft Defender Research Team observed a multi‑stage intrusion where threat actors exploited internet‑exposed SolarWinds Web Help Desk (WHD) instances to get an initial foothold and then laterally moved towards other high-value assets within the organization. However, we have not yet confirmed whether the attacks are related to the[…]
Read More
In January 2026, Microsoft Defender Experts identified a new evolution in the ongoing ClickFix campaign. This updated tactic deliberately crashes victims’ browsers and then attempts to lure users into executing malicious commands under the pretext of restoring normal functionality. This variant represents a notable escalation in ClickFix tradecraft,[…]
Read More
Today, we’re excited to announce that the new usage page in the Power Platform admin center (PPAC) is available in public preview! This release delivers a modern, centralized way to understand how Microsoft Power Apps, Power Automate, and Copilot Studio are being used across your organization, empowering administrators[…]
Read More
What if your AI agents truly understood your business—your data, your workflows, your goals—and IT could still govern them at scale? That’s the promise of Adaptive Intelligence, and it’s now within reach. In our recent Ignite session, Jason Huang and I walked through exactly how to build enterprise-grade agents[…]
Read MoreToday, organizations are being measured by how quickly they can innovate. Whether it’s launching new digital experiences, streamlining operations, or responding to customer needs in real time, the ability to move fast has always been a competitive differentiator. And it only grew on importance in the agentic era.[…]
Read MoreWhen building advanced, data‑driven sites on Power Pages, developers often encounter limitations and fragility in standard DOM manipulation. Relying on jQuery selectors to hide fields or move elements is prone to breaking when the underlying HTML structure changes. Furthermore, performing Web API operations (CRUD) often requires repetitive boilerplate[…]
Read More
While patchwork tools slow defenders down and impact visibility into potential cyberthreats, they’re an unfortunate reality for many organizations. As digital risk accelerates and attack surfaces multiply, security leaders are doing their best to stitch together point solutions while trying to avoid blind spots that cyberattackers can exploit.[…]
Read More