Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
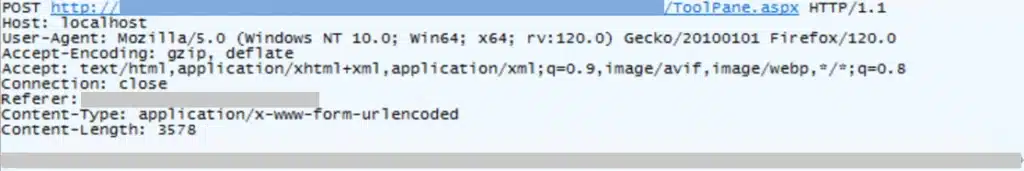
On July 19, 2025, Microsoft Security Response Center (MSRC) published a blog addressing active attacks against on-premises SharePoint servers that exploit CVE-2025-49706, a spoofing vulnerability, and CVE-2025-49704, a remote code execution vulnerability. These vulnerabilities affect on-premises SharePoint servers only and do not affect SharePoint Online in Microsoft 365.[…]
Read More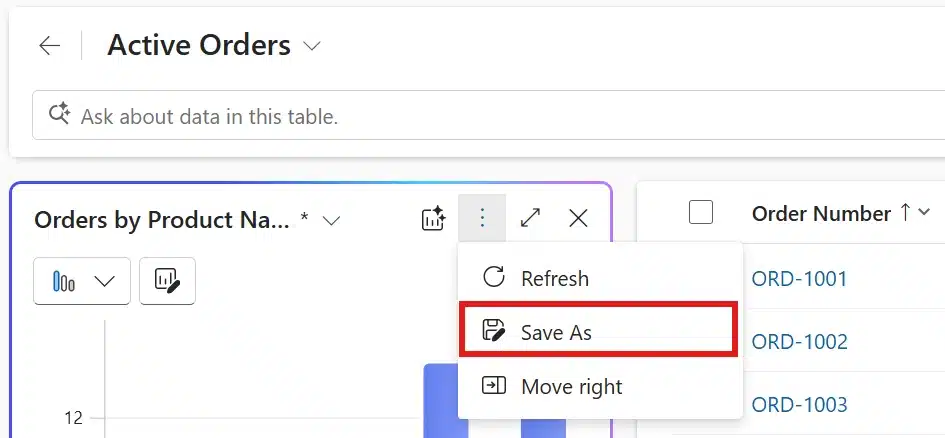
Understanding your business data shouldn’t be a one-time effort, it should be part of your everyday decision-making flow. With Visualize with Copilot, we introduced a faster way to uncover insights using AI-generated charts. Now, we’re taking it a step further. You can save the AI-generated visualizations directly within[…]
Read More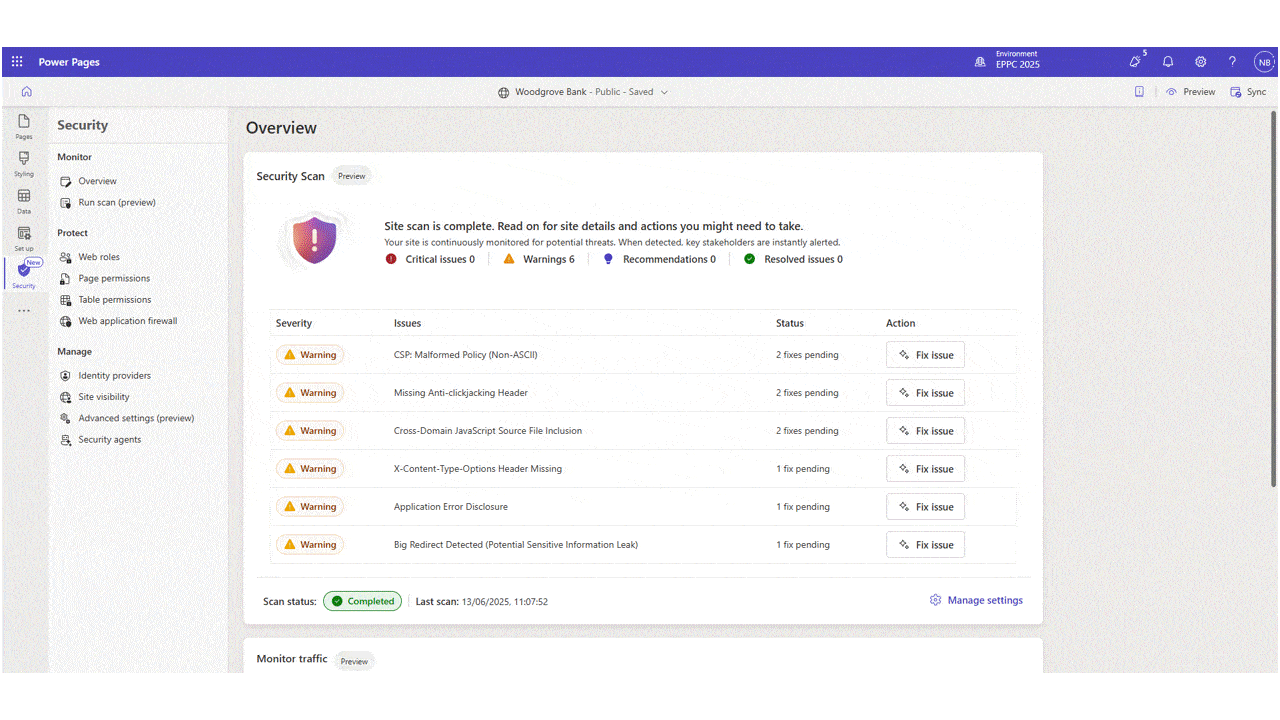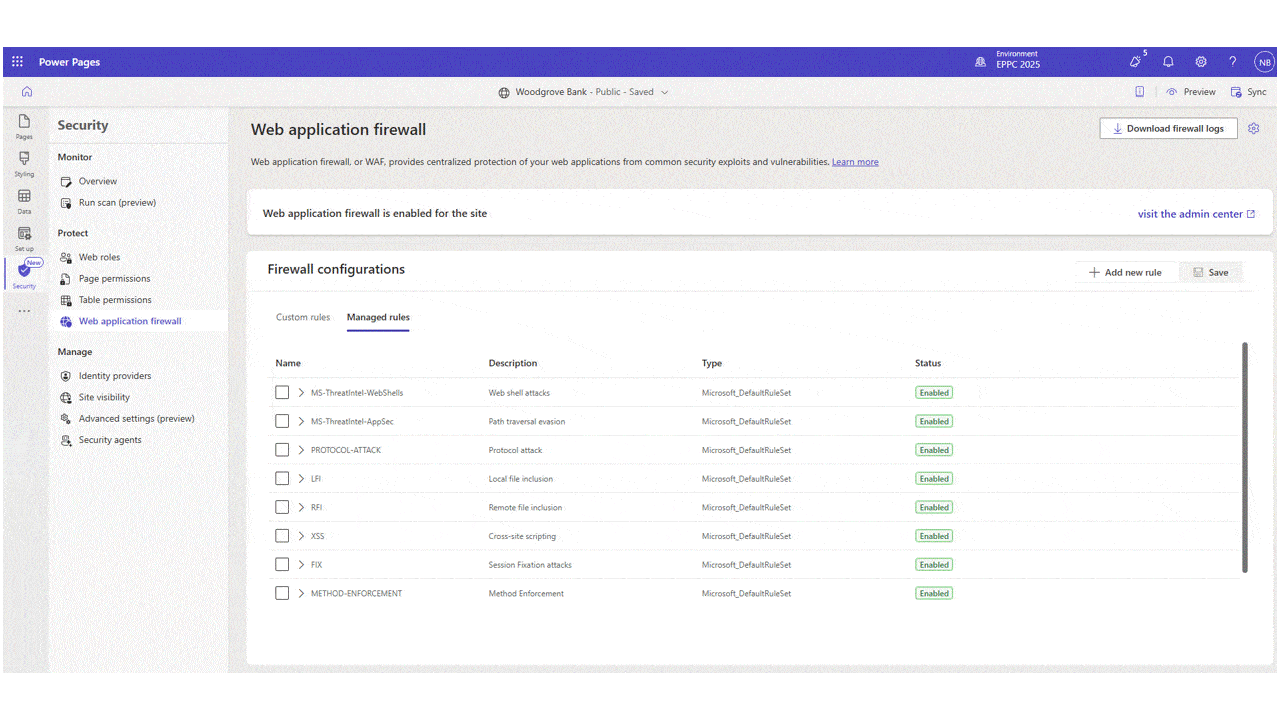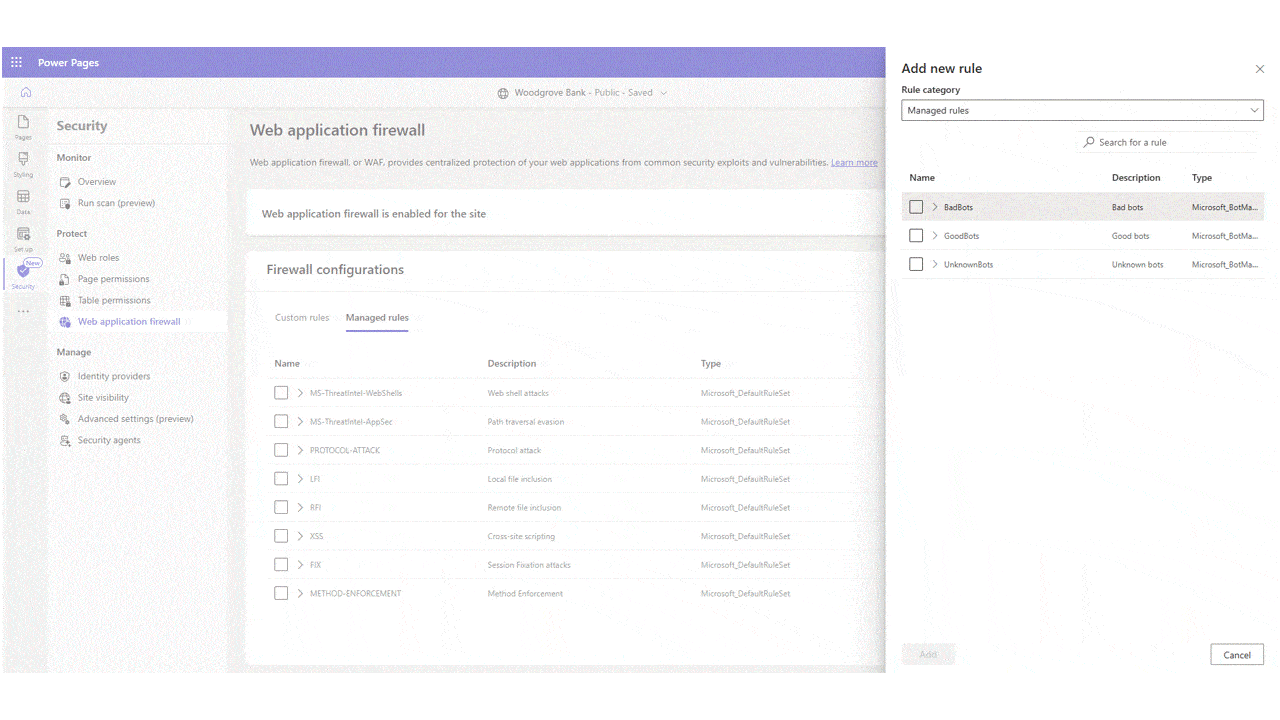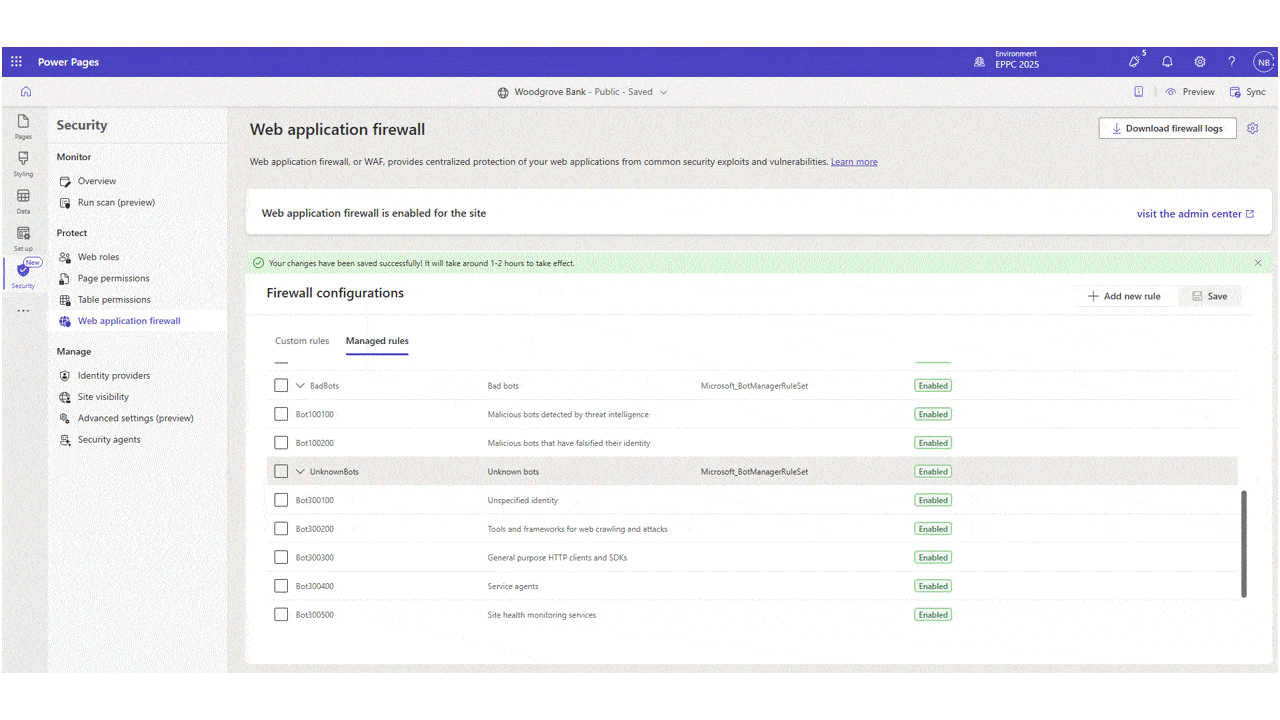
As part of our ongoing commitment to elevate securing Power Pages, we’re excited to announce the release of Azure managed Bot Protection rule designed to help safeguard sites against automated threats like credential stuffing, spam, and scraping attacks. Bot Protection Rule The Bot Protection rule adds a layer[…]
Read More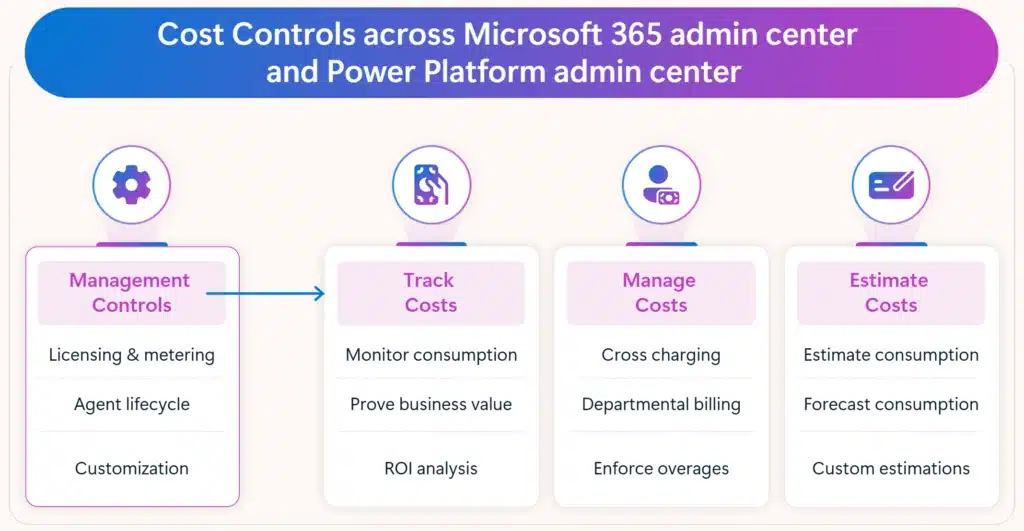
As organizations accelerate their adoption of agents to automate tasks, enhance productivity, and deliver new customer experiences, they often face a critical new challenge: unpredictable costs. While consumption-based billing models like pay-as-you-go (PAYG) and prepaid message packs offer flexibility and agility, they can also introduce unexpected charges, budget[…]
Read MoreToday, we’re taking another big leap forward in applying AI to the future of app development: you can now work with agents to generate code directly in Microsoft Power Apps. This brings the speed and flexibility of vibe coding together with the connectivity, security, and scale of a[…]
Read MoreMicrosoft will be at Black Hat USA 2025, August 5–7 in Las Vegas, and we’re bringing you a unified, practitioner-driven experience built around real-world insights, threat intelligence, incident response, and hands-on AI expertise.We believe security teams are strongest when intelligence, tools, and deep expertise come together. At Microsoft,[…]
Read More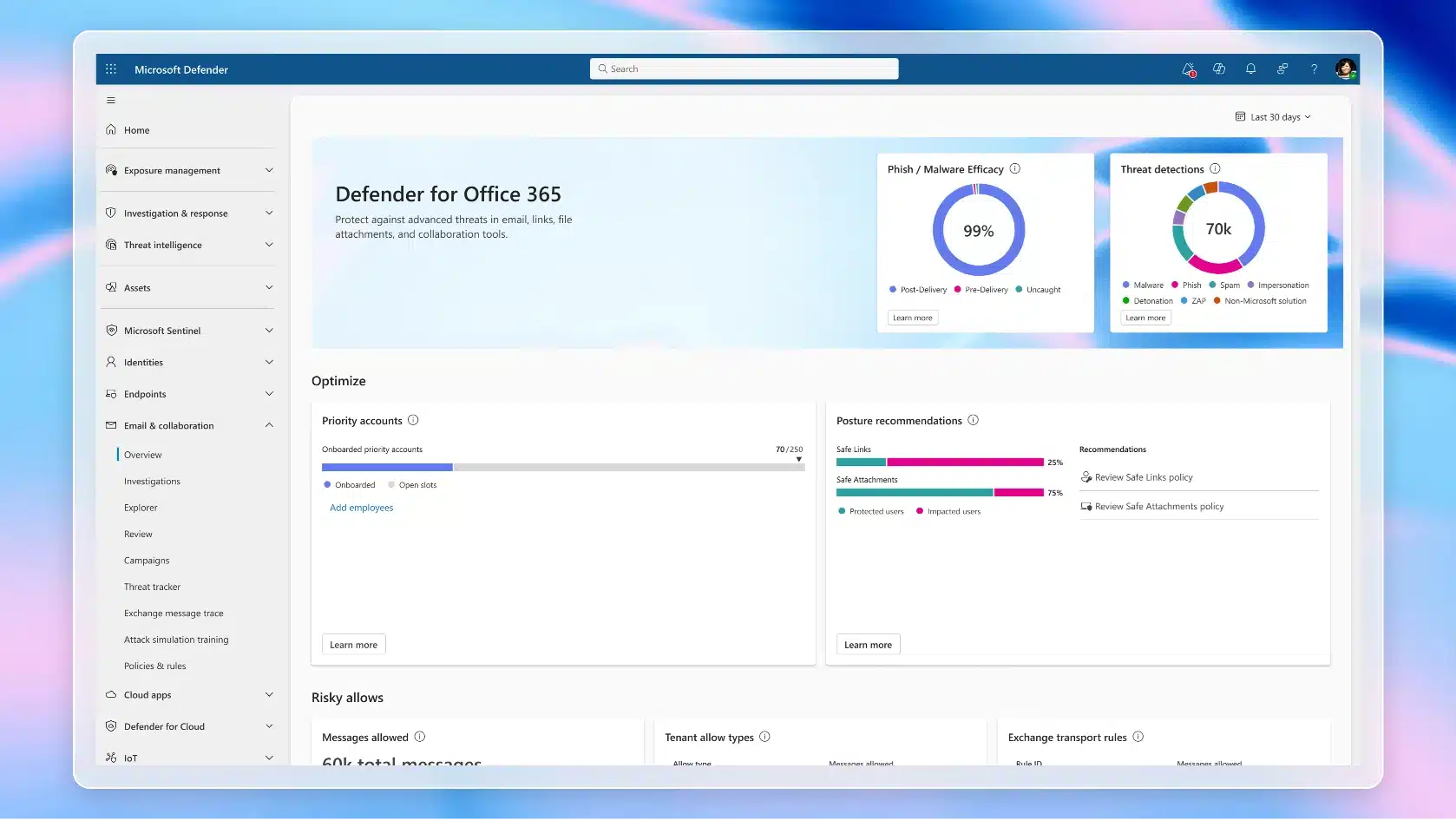
In today’s world, cyberattackers are relentless. They are often well-resourced, highly sophisticated, and constantly innovating, which means the effectiveness of cybersecurity solutions must be continuously evaluated, not assumed. Yet, despite the critical role email security plays in protecting organizations, there is limited transparency and standardization in how email[…]
Read MoreSince 2022, the number of human-operated ransomware-linked encounters by organizations surged by 2.75x. Yet, Microsoft Defender for Endpoint has outpaced this rise, reducing the number of successful attacks by 3x, proving its power to turn the tide against evolving cyberthreats.1 Defender for Endpoint’s ability to disrupt ransomware at[…]
Read More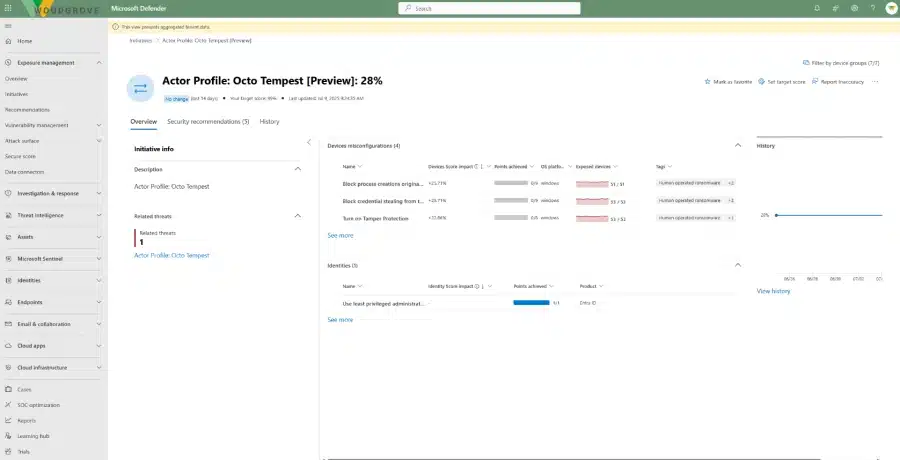
In recent weeks, Microsoft has observed Octo Tempest, also known as Scattered Spider, impacting the airlines sector, following previous activity impacting retail, food services, hospitality organizations, and insurance between April and July 2025. This aligns with Octo Tempest’s typical patterns of concentrating on one industry for several weeks[…]
Read MoreWe’re entering the age of AI agents, a transformative moment reshaping the landscape of business applications and platforms. AI agents aren’t just making incremental improvements, they’re helping to redefine productivity and can fundamentally change how work gets done. Published today, the 2025 release wave 2 for Microsoft Dynamics[…]
Read More