Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
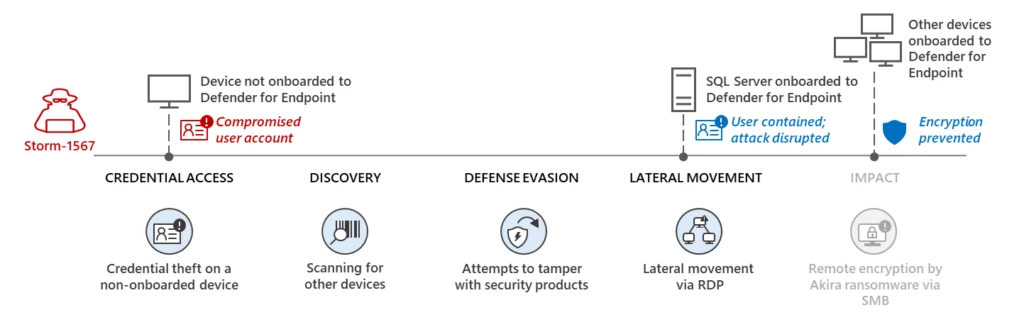
Our experience and insights from real-world incidents tell us that the swift containment of compromised user accounts is key to disrupting hands-on-keyboard attacks, especially those that involve human-operated ransomware. In these attacks, lateral movement follows initial access as the next critical stage for attackers to advance their objective[…]
Read More
Defenders need every edge they can get in the fight against ransomware. Today, we’re pleased to announce that Microsoft Defender for Endpoint customers will now be able automatically to disrupt human-operated attacks like ransomware early in the kill chain without needing to deploy any other capabilities. Now, organizations[…]
Read More
Since we first introduced Microsoft Security Experts in May 2022, we’ve worked hard to expand our new security services category. In the past 16 months, we’ve launched new services, expanded our capabilities, and introduced new ways to buy. Our customers face an unprecedented number of security threats that[…]
Read More
AI is here, and it’s ready to support work. On complex challenges like analyzing troves of data, speeding up time-consuming tasks, or helping customers help themselves—the newest AI sets up organizations for operational excellence by allowing employees to quickly create solutions for complicated problems on their own. That’s[…]
Read More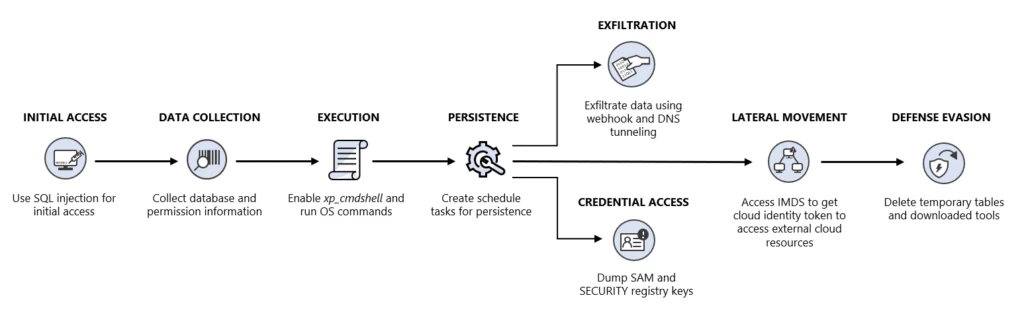
Microsoft security researchers recently identified a campaign where attackers attempted to move laterally to a cloud environment through a SQL Server instance. This attack technique demonstrates an approach we’ve seen in other cloud services such as VMs and Kubernetes cluster, but not in SQL Server. The attackers initially[…]
Read More
Welcome to the second Microsoft Power Platform Conference! Since the first conference, there has been a seismic shift in how we build low-code solutions. With Power Platform Copilot, we are now in the era of AI-assisted low-code development. As such, this year’s conference is focused on helping the[…]
Read More
This year marks the twentieth anniversary of Cybersecurity Awareness Month, when we partner with the National Cybersecurity Alliance, the United States Cybersecurity and Infrastructure Security Agency (CISA), and organizations around the world to amplify the importance of cybersecurity best practices and how to be cybersmart. Initially, this moment[…]
Read More
During the past few years, we’ve managed a lot of change and disruption in our security work, in our lives, and in society at large. This year we’re excited to welcome back security leaders, aspiring leaders, and IT professionals—in person—to Microsoft Ignite from November 14 to 17, 2023,[…]
Read More
While attacks are getting more sophisticated, so are our defenses. With recent innovations like secured-core PCs that are 60 percent more resilient to malware than non-secured-core PCs,1 and the Microsoft Pluton Security Processor that adds more protection by isolating sensitive data like credentials and encryption keys, Windows 11[…]
Read MoreToday marks an exciting milestone in Microsoft’s AI journey. This morning, at an event in New York City, we made several major announcements to empower people across work and life—you can read more about Microsoft Bing and Edge with Copilot, what’s new from Microsoft 365 Copilot and Bing[…]
Read More