Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
Microsoft Threat Intelligence recently detected and blocked a credential phishing campaign that likely used AI-generated code to obfuscate its payload and evade traditional defenses. Appearing to be aided by a large language model (LLM), the activity obfuscated its behavior within an SVG file, leveraging business terminology and a[…]
Read More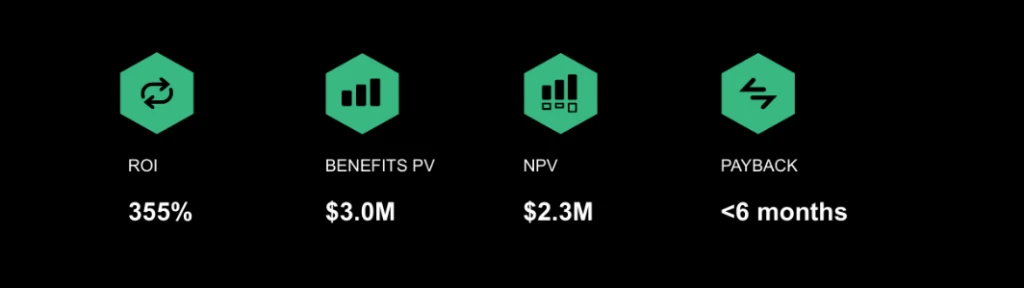
In today’s digital-first world, data is both an asset and a liability. As organizations scale their use of cloud platforms, AI, and remote collaboration tools, the complexity of managing data security, data privacy, and regulatory compliance grows exponentially. For organizations, the challenge is no longer just about preventing[…]
Read More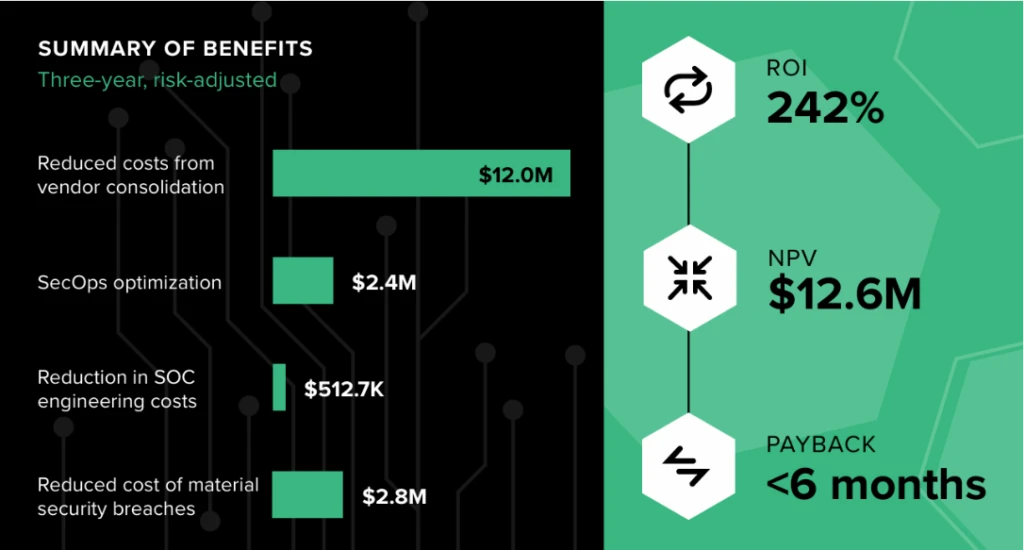
The latest Forrester Total Economic Impact™ (TEI) study reveals a 242% return on investment (ROI) over three years for organizations that chose Microsoft Defender. It helps security leaders consolidate tools, reduce overhead, and empower their security operations (SecOps) teams with operational efficiencies powered by AI and automation. In total, the study found Microsoft Defender delivers $17.8 million in benefits and paid for itself[…]
Read More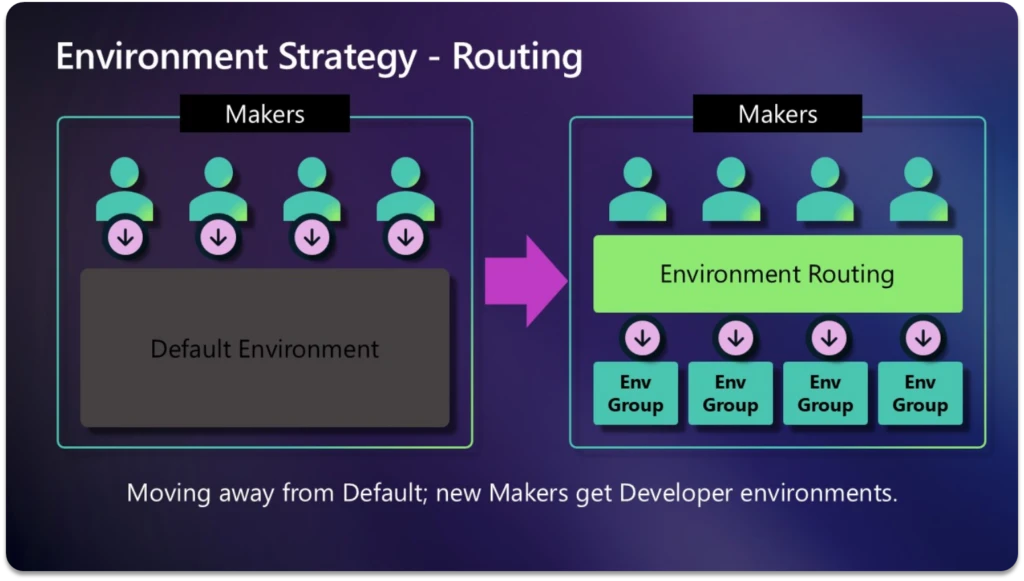
Personal Developer Environments (PDEs) are reshaping how organizations adopt Power Platform capabilities – like Copilot Studio agents, Power Apps, and Power Automate flows – by enabling secure, governed innovation. Microsoft IT (MSIT), our internal IT team, has transitioned our makers from building in the shared Default environment to[…]
Read More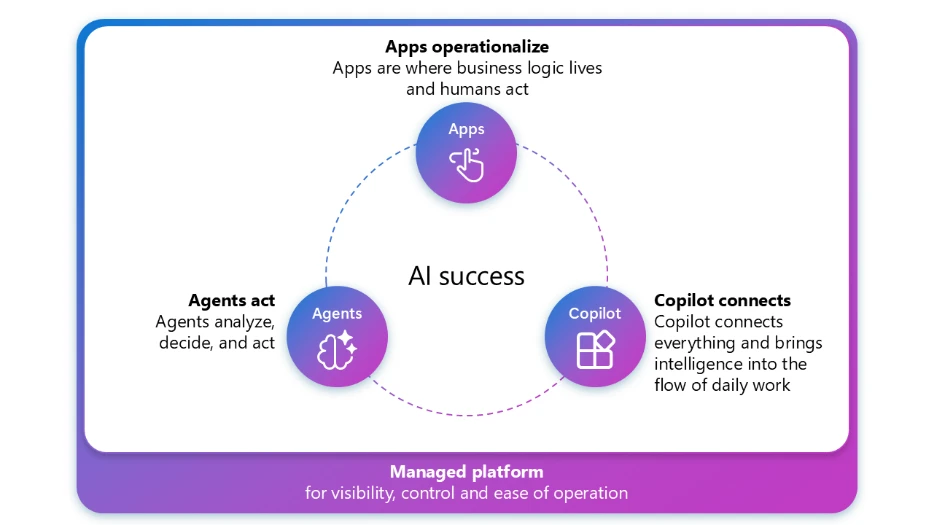
The Microsoft Power Platform community is the heart of everything we do, the driving force behind all innovation—ideas, feedback, and creativity are what make this platform thrive. We’re just six weeks away from the Power Platform Community Conference 2025 (PPCC 2025), and the excitement is already palpable. I’m sure it’s not just the heat from the wings in my interview—it’s the anticipation[…]
Read More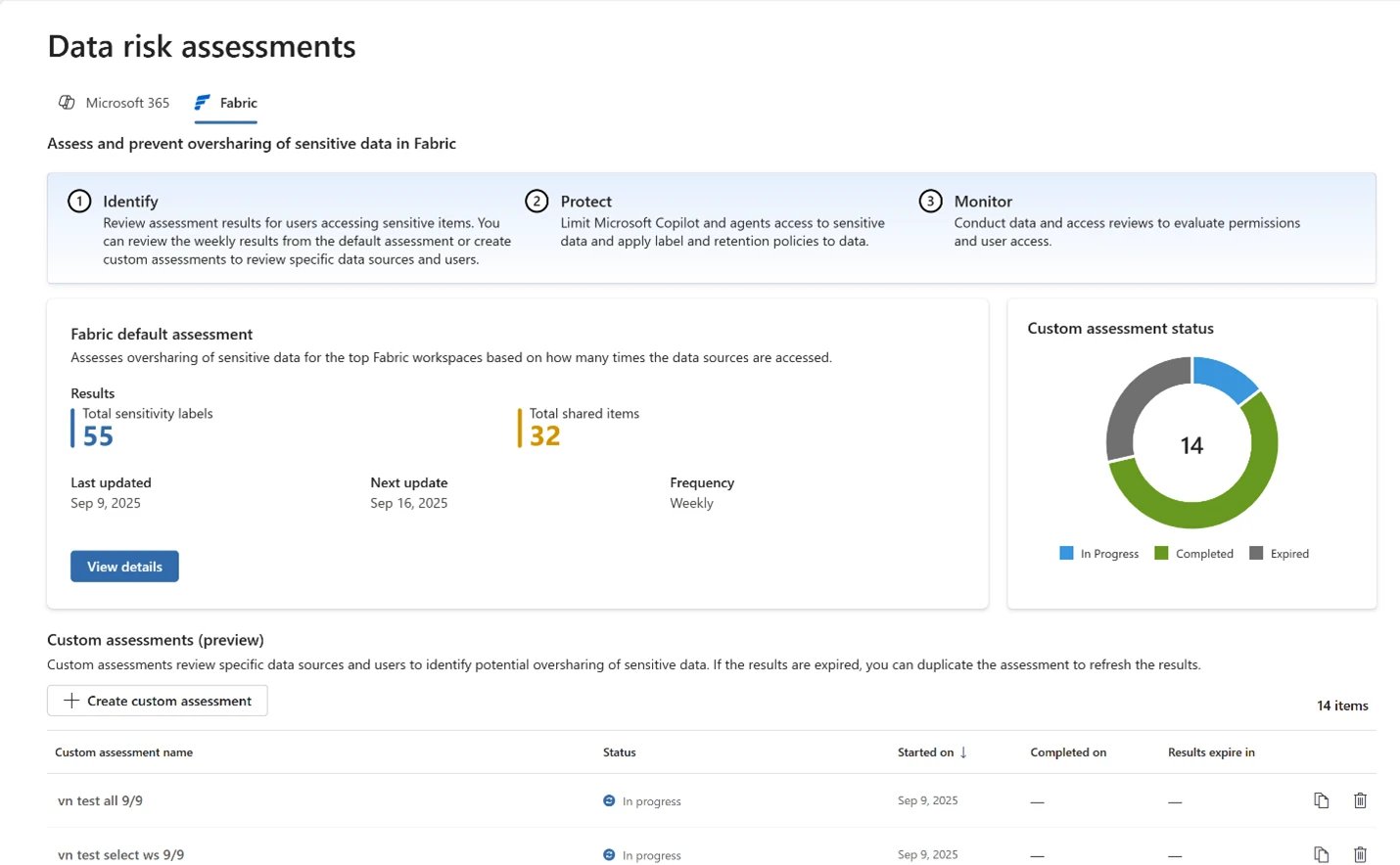
The Microsoft Fabric and Purview teams are thrilled to participate in the European Microsoft Fabric Community Conference September 15-18, 2025, in Vienna, Austria. This event is Microsoft’s largest tech conference in Europe, where data professionals gather to connect and share insights on data, security, governance, and AI transformation.[…]
Read More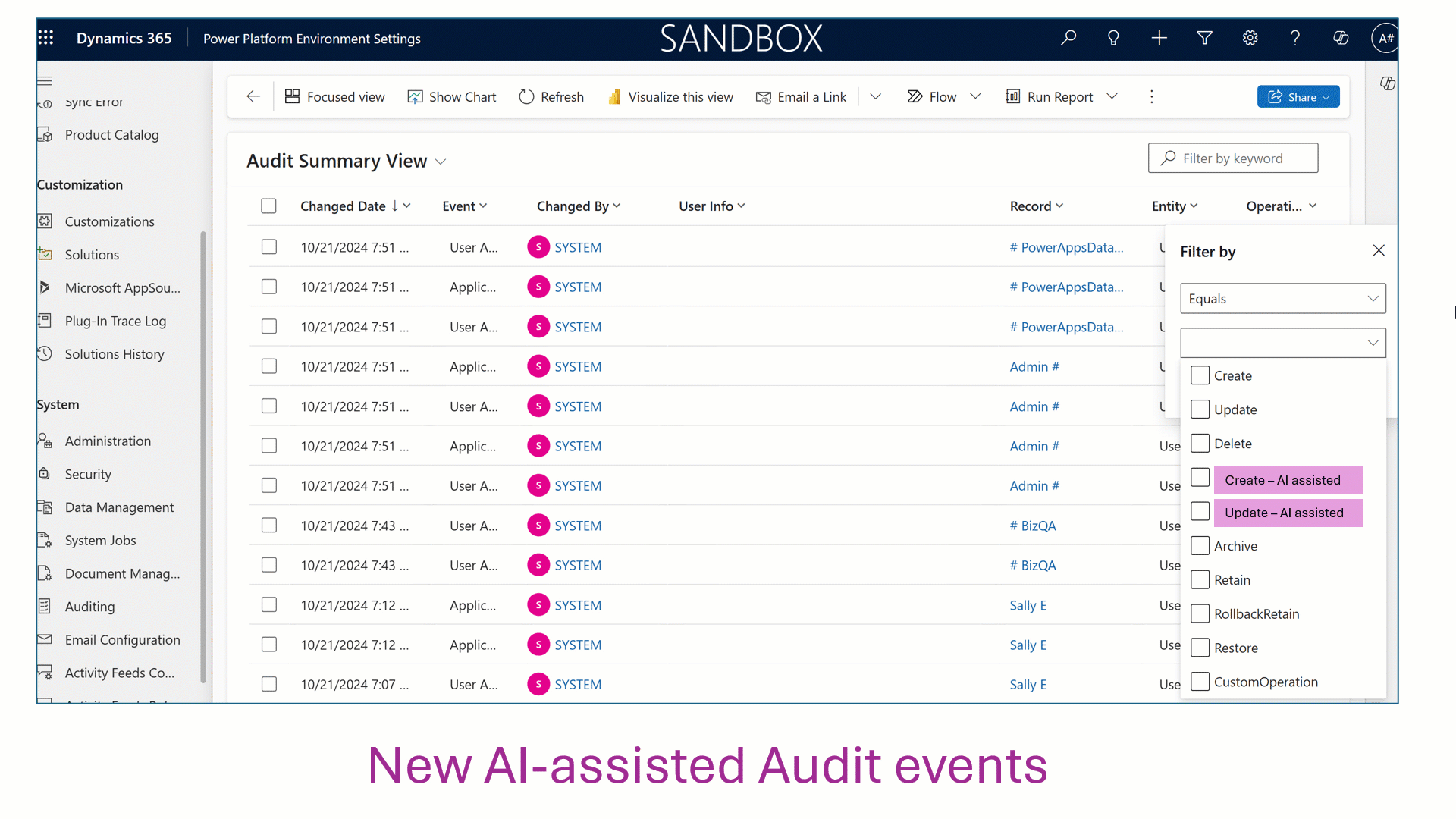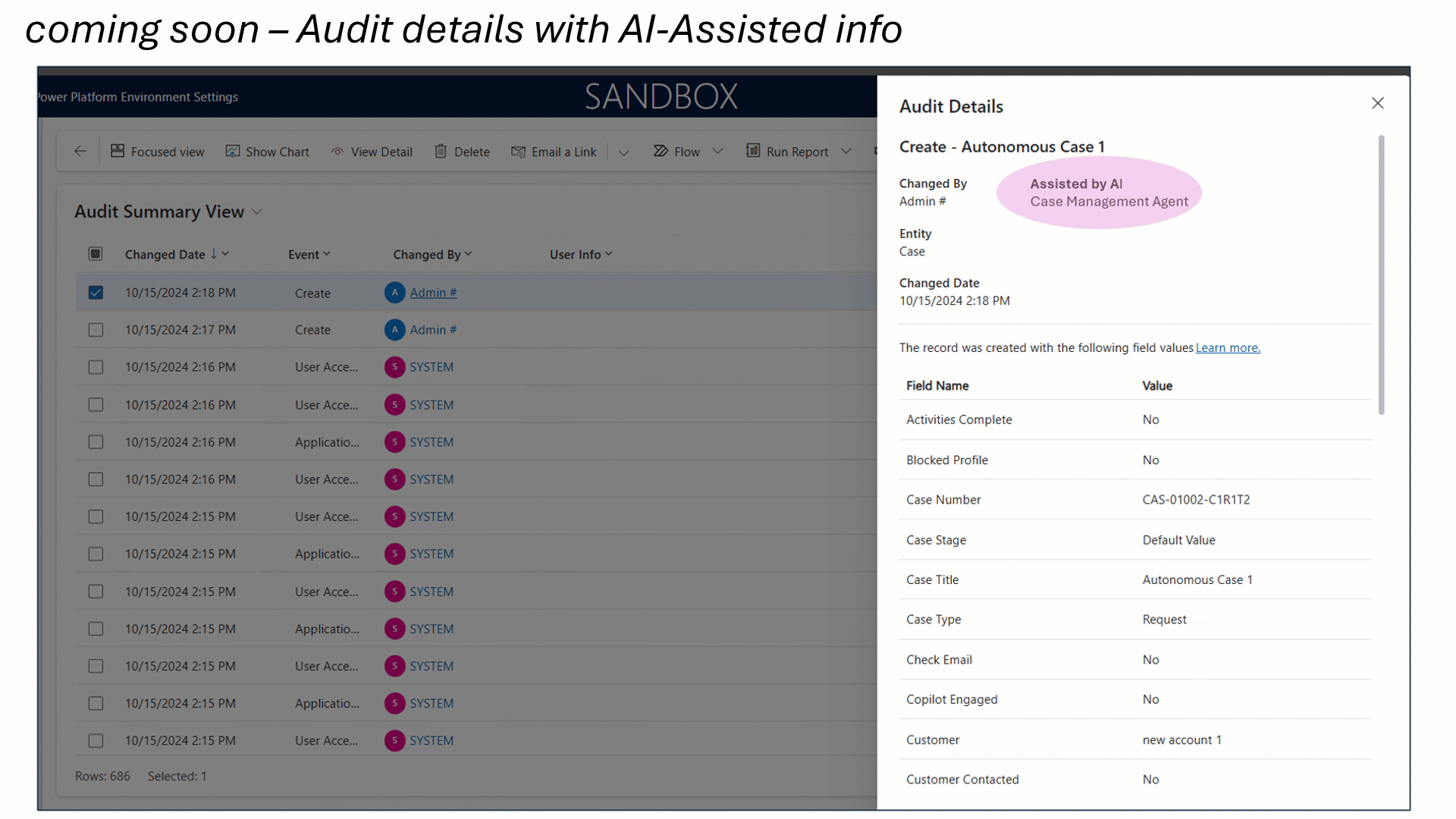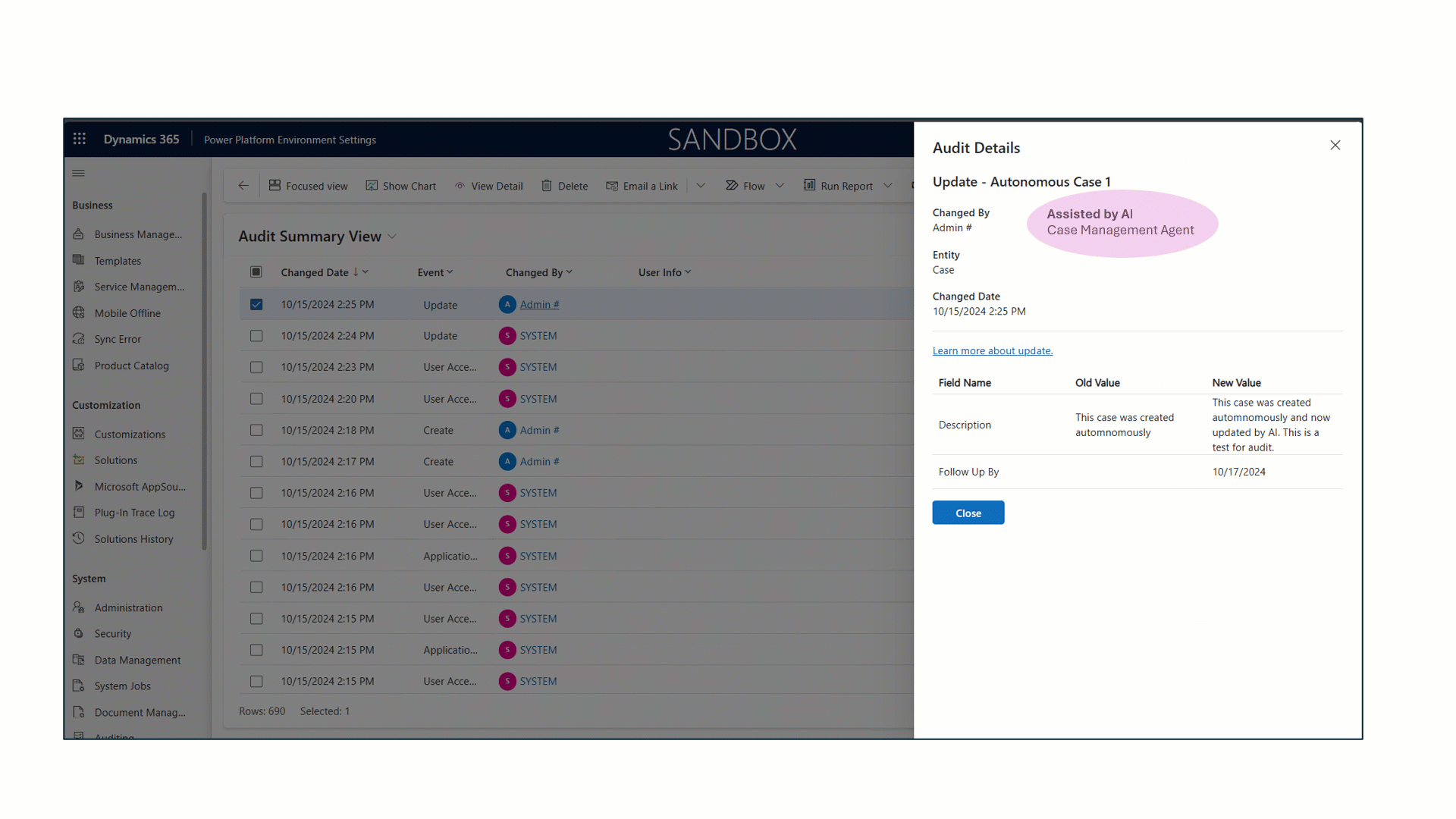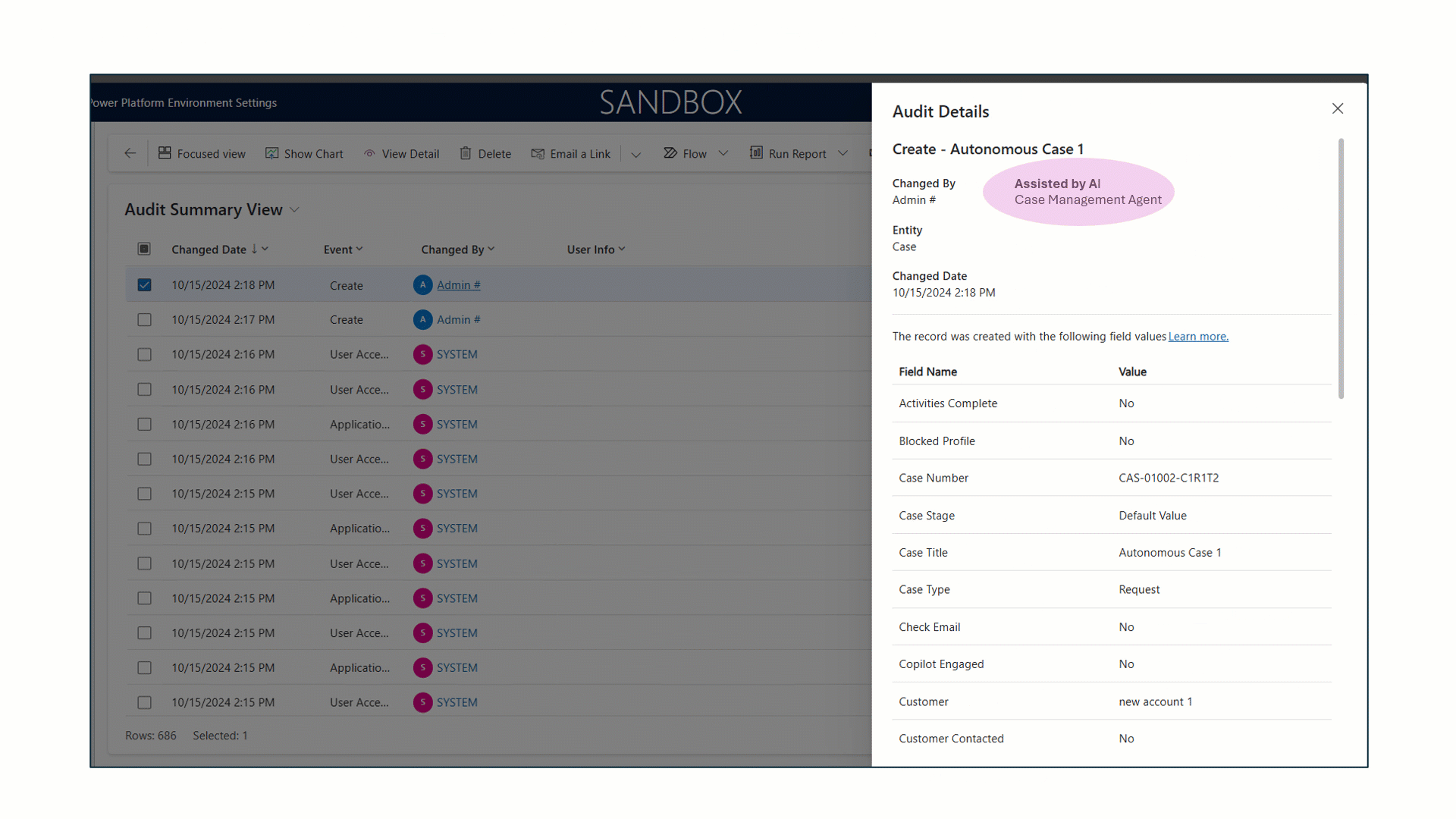
As organizations advance in the digital era, strong data governance is essential. With AI-driven operations and growing business demands, greater transparency and oversight are required. Microsoft Dataverse, central to Power Platform solutions, now offers enhanced auditing features—including AI-assisted agent events, user label tracking, privacy compliance, retention policies, and[…]
Read More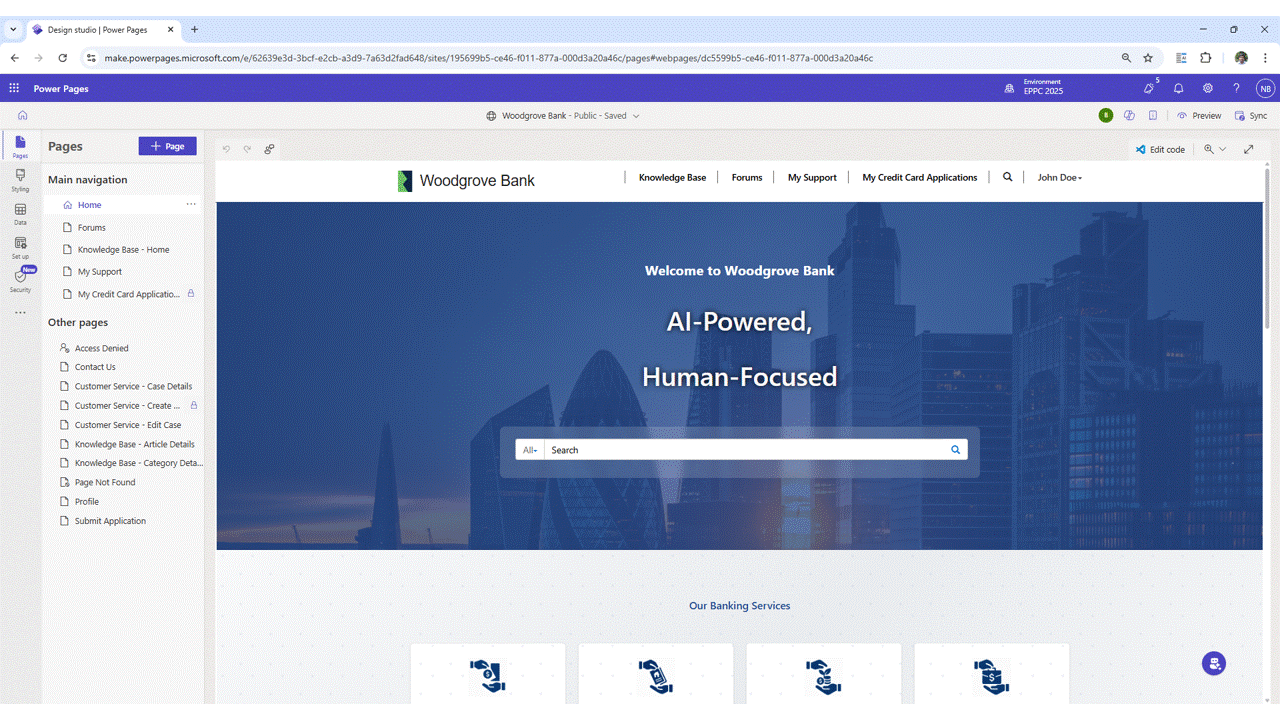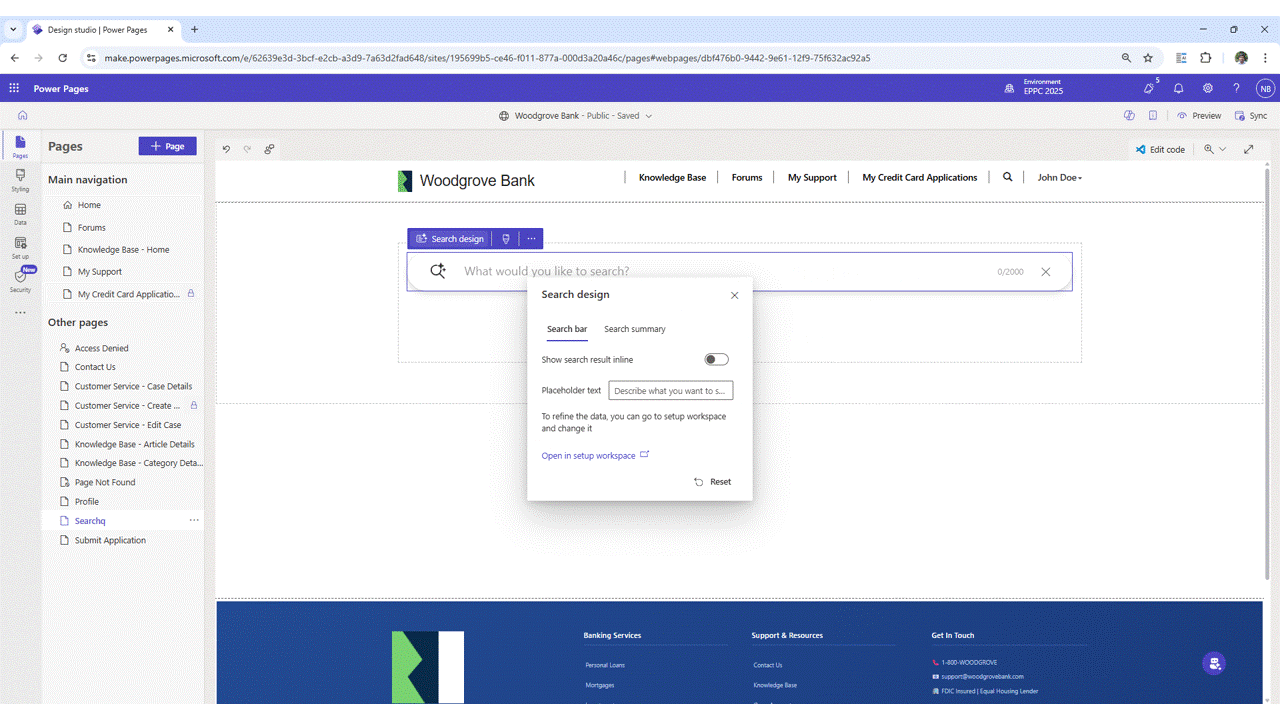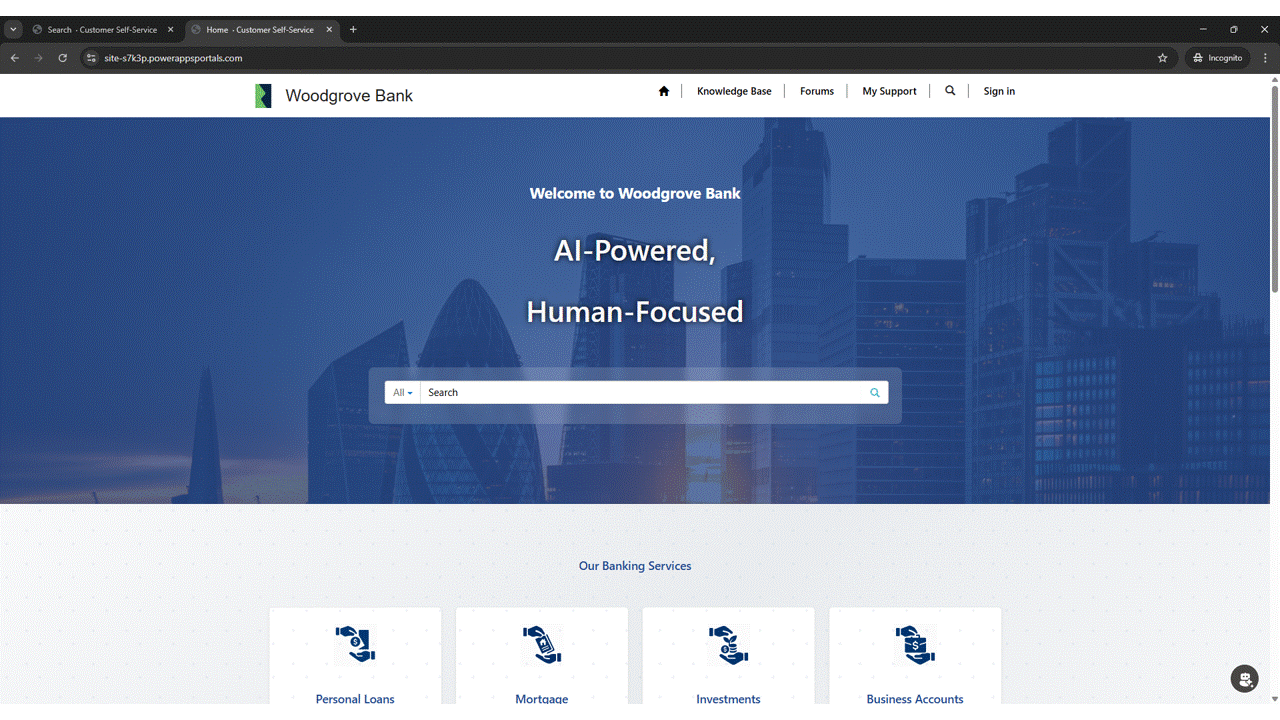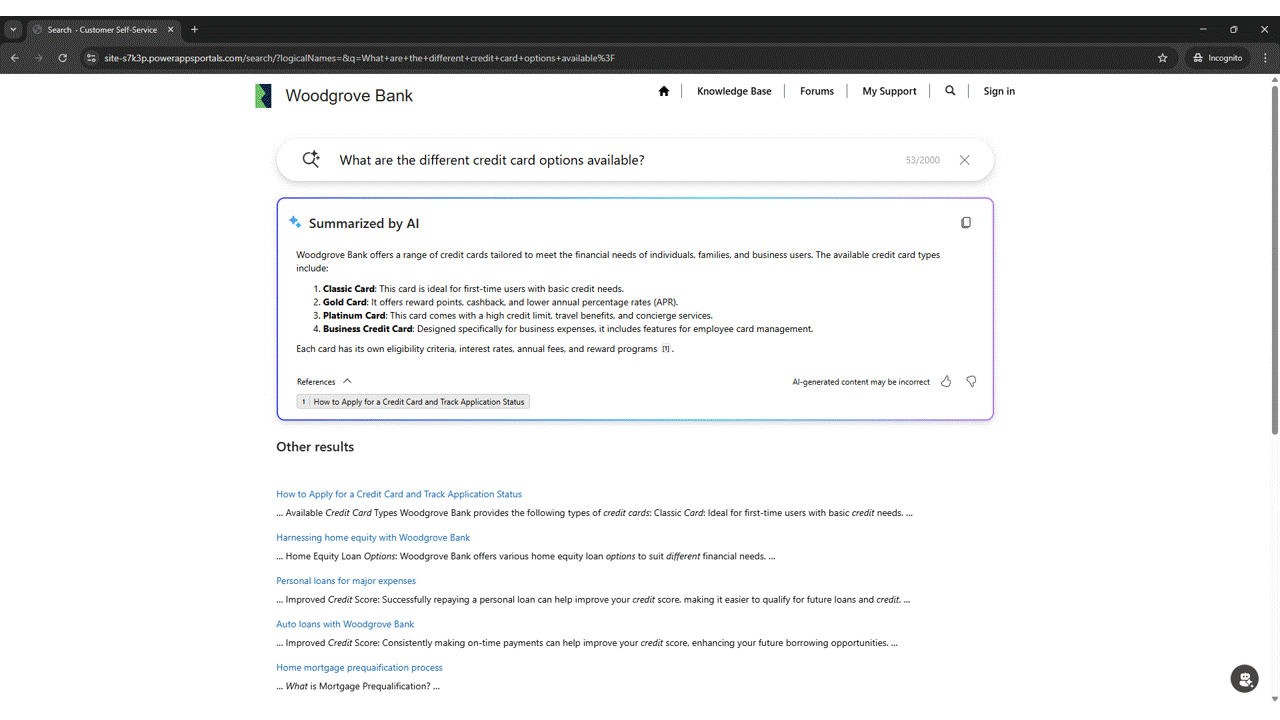
We are pleased to announce the General Availability (GA) of Power Pages Search with Generative AI Summarization. This capability enhances the search experience on Power Pages sites by combining traditional search with AI-generated summaries, helping site visitors find information more efficiently and in the language that they are[…]
Read MoreAs cyberattacks become increasingly frequent, sophisticated, and damaging, safeguarding your digital assets has never been more critical, and at Microsoft, your security is our top priority. Microsoft research shows that multi-factor authentication (MFA) can block more than 99.2% of account compromise attacks, making it one of the most effective security[…]
Read More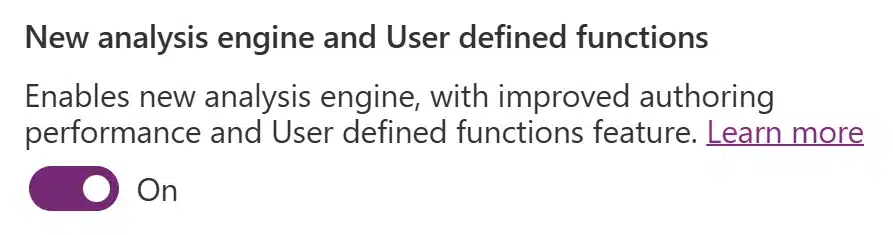
We are thrilled to announce that User defined functions (UDFs) in Power Apps have reached general availability! They are now ready for your production workloads. Thank you to everyone who provided valuable feedback on this feature and helped us reach this milestone! With version 2508.3 the UDF preview[…]
Read More