Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- 80% of Fortune 500 use active AI Agents: Observability, governance, and security shape the new frontier 10 Febbraio 2026
- Manipulating AI memory for profit: The rise of AI Recommendation Poisoning 10 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- A one-prompt attack that breaks LLM safety alignment 9 Febbraio 2026
- Analysis of active exploitation of SolarWinds Web Help Desk 7 Febbraio 2026
The post How to achieve cloud-native endpoint management with Microsoft Intune appeared first on Microsoft Security Blog. Source: Microsoft Security
Read More
In today’s fast-paced digital landscape, enterprise organizations are grappling with an ever-expanding application backlog, with hundreds of millions of new apps expected to be built by 2028. However, there are only four million developers in the United States.1 This disparity underscores the urgent need for scalable solutions that[…]
Read More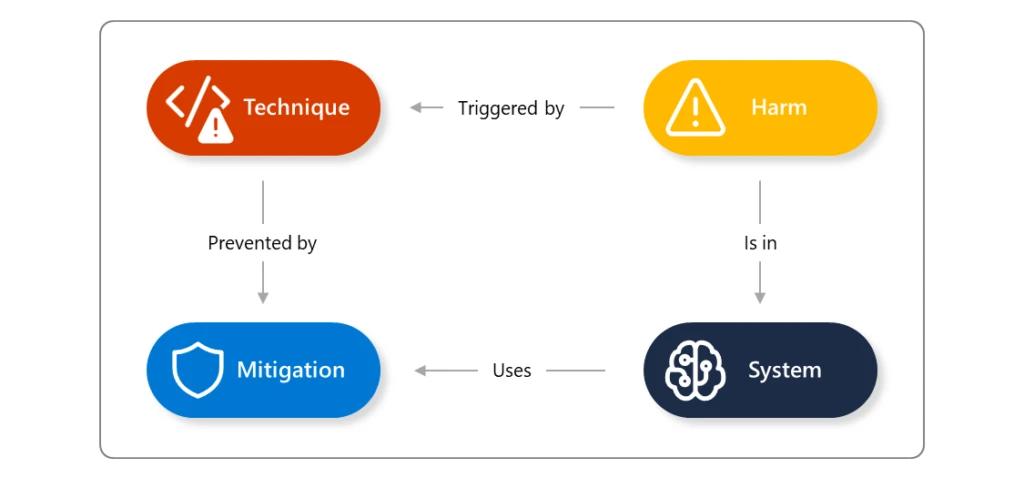
Generative AI systems are made up of multiple components that interact to provide a rich user experience between the human and the AI model(s). As part of a responsible AI approach, AI models are protected by layers of defense mechanisms to prevent the production of harmful content or[…]
Read More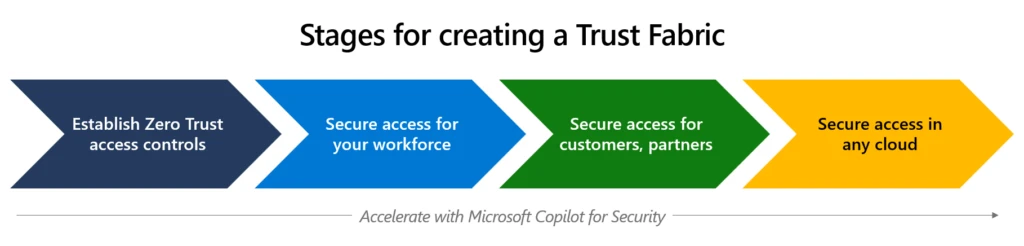
How implementing a trust fabric strengthens identity and network Read the blog At Microsoft, we’re continually evolving our solutions for protecting identities and access to meet the ever-changing security demands our customers face. In a recent post, we introduced the concept of the trust fabric. It’s a real-time[…]
Read More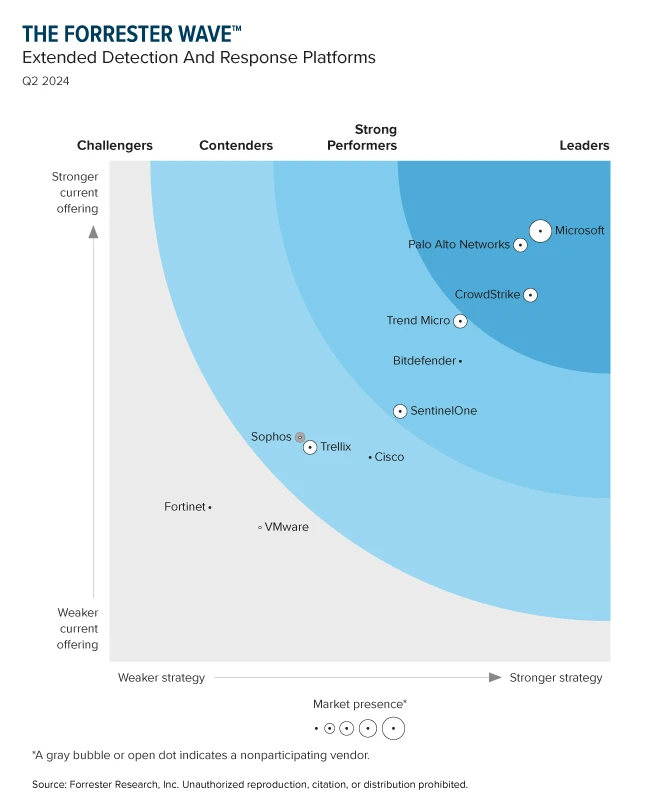
“Defenders think in lists, attackers think in graphs.”1 This remains a reality for the many organizations that operate across siloed security tools, fueling the demand on security operations (SOC) teams, as advanced cyberattacks continue to increase in frequency and speed. That’s where extended detection and response (XDR) solutions[…]
Read More
Since late 2023, Microsoft has observed an increase in reports of attacks focusing on internet-exposed, poorly secured operational technology (OT) devices. Internet-exposed OT equipment in water and wastewater systems (WWS) in the US were targeted in multiple attacks over the past months by different nation-backed actors, including attacks[…]
Read More
Multicloud computing has become the foundation for digital businesses, with 86% of organizations having already adopted a multicloud approach.1 However, for all its benefits around increased agility, flexibility, and choice, we also see unique challenges with multicloud—including the need to manage security, identity, and compliance across different cloud[…]
Read More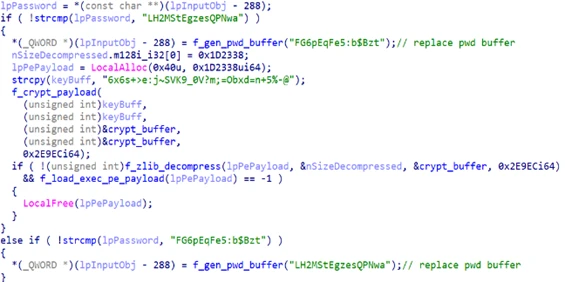
Microsoft has identified a new North Korean threat actor, now tracked as Moonstone Sleet (formerly Storm-1789), that uses both a combination of many tried-and-true techniques used by other North Korean threat actors and unique attack methodologies to target companies for its financial and cyberespionage objectives. Moonstone Sleet is[…]
Read More
In the ever-evolving landscape of cyberthreats, staying ahead of malicious actors is a constant challenge. Microsoft Threat Intelligence has observed that gift cards are attractive targets for fraud and social engineering practices. Unlike credit or debit cards, there’s no customer name or bank account attached to them, which[…]
Read More
Microsoft Copilot is designed to enhance business productivity by leveraging AI to streamline routine tasks, allowing users to concentrate on strategic and creative endeavors. It boosts organizational efficiency by automating repetitive tasks, freeing up time for the workforce, and enriching solution capabilities with integrated experiences in Microsoft Power[…]
Read More