Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
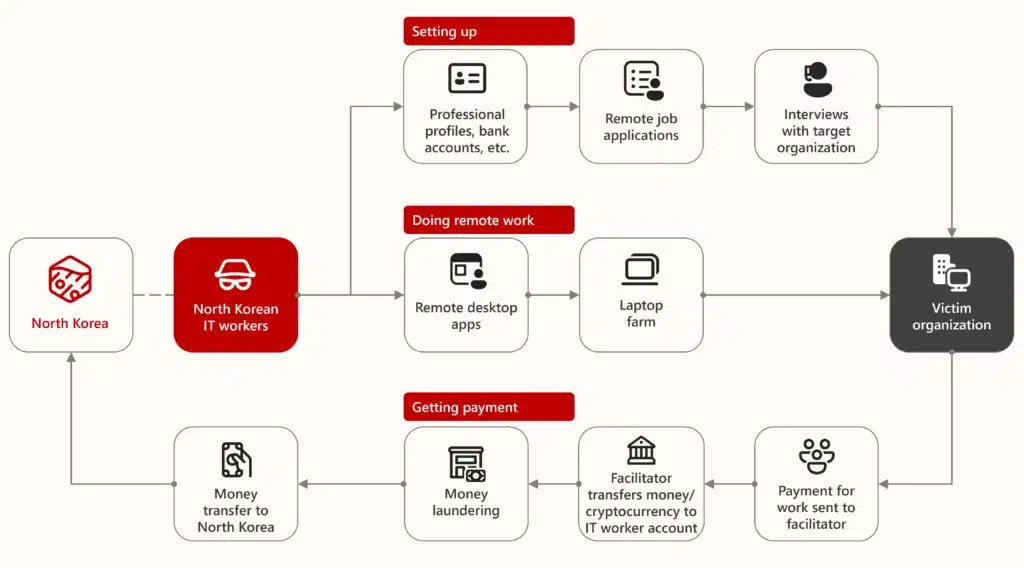
Since 2024, Microsoft Threat Intelligence has observed remote information technology (IT) workers deployed by North Korea leveraging AI to improve the scale and sophistication of their operations, steal data, and generate revenue for the Democratic People’s Republic of Korea (DPRK). Among the changes noted in the North Korean[…]
Read More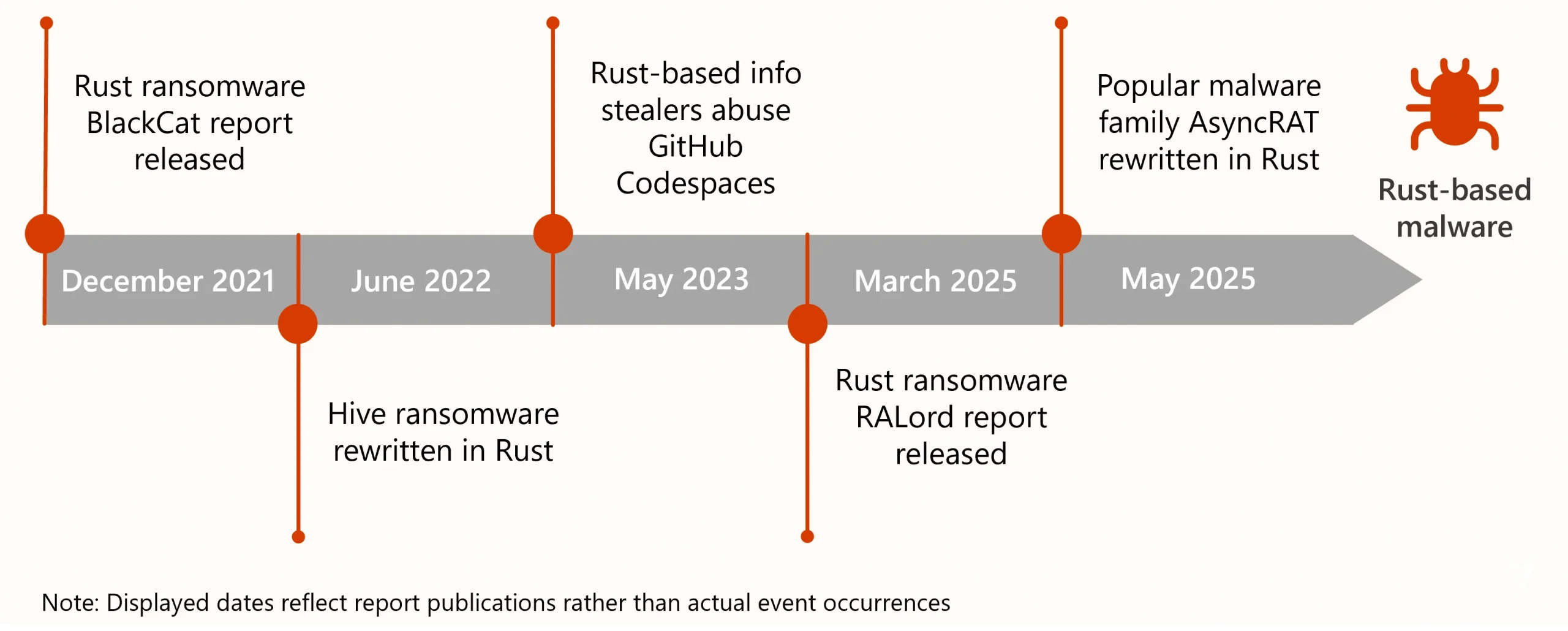
Today, Microsoft Threat Intelligence Center is excited to announce the release of RIFT, a tool designed to assist malware analysts automate the identification of attacker-written code within Rust binaries. Known for its efficiency, type safety, and robust memory safety, Rust has increasingly become a tool for creating malware,[…]
Read More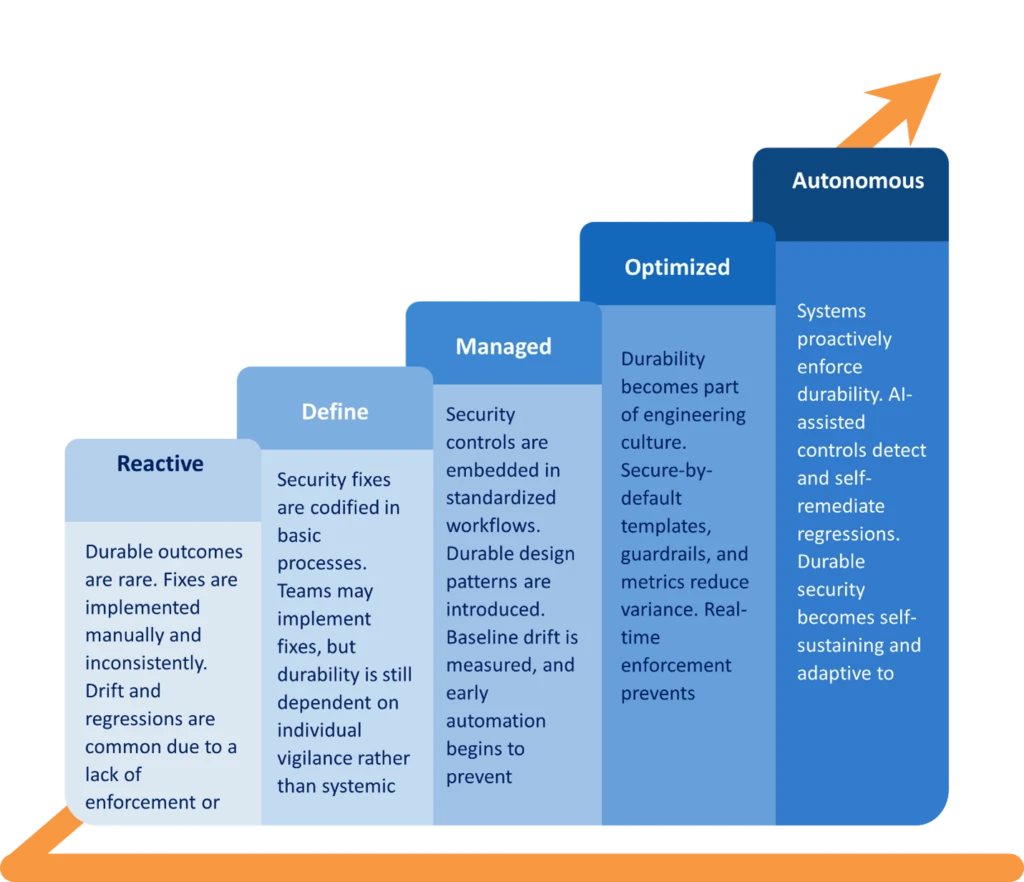
In this blog you will hear directly from Microsoft’s Deputy Chief Information Security Officer (CISO) for Azure and operating systems, Mark Russinovich, about how Microsoft operationalized security durability at scale. This blog is part of an ongoing series where our Deputy CISOs share their thoughts on what is[…]
Read More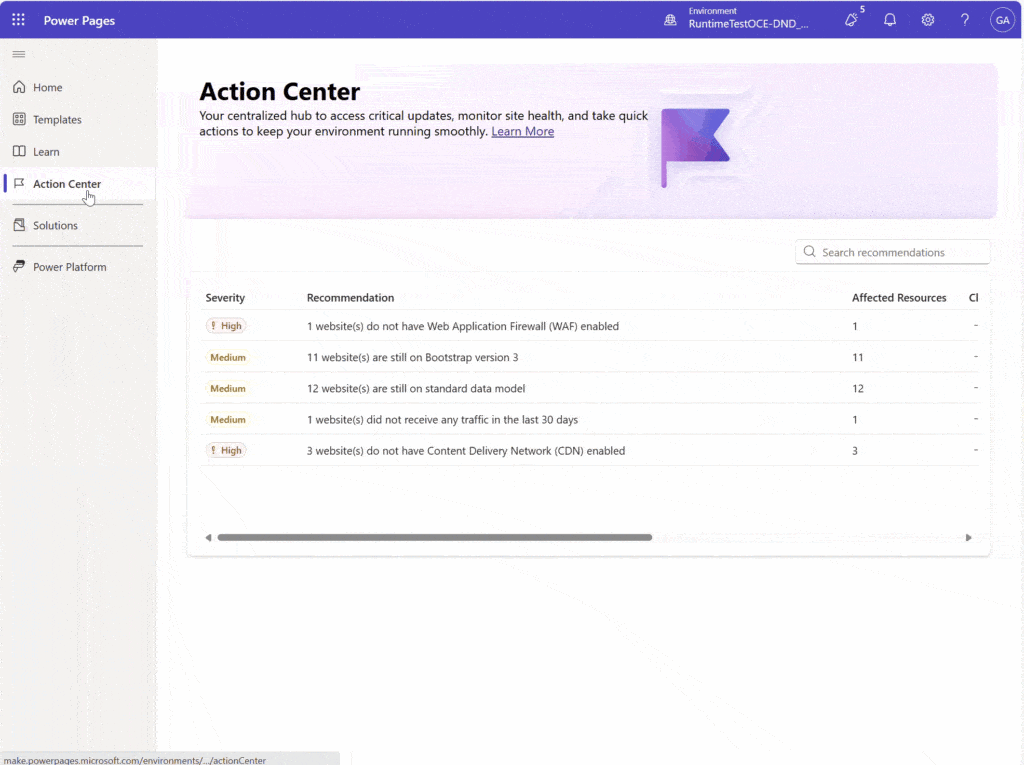
Managing multiple websites across environments can be overwhelming, especially when trying to stay on top of expiring sites, performance gaps, and security configurations. This is where the Action Center in Power Pages Home comes in. It offers a streamlined, centralized experience to help makers and site owners take[…]
Read MoreThe cloud-native application protection platform (CNAPP) market continues to evolve rapidly as organizations look to secure increasingly complex cloud environments. In the recently published 2025 IDC MarketScape for Worldwide CNAPP, Microsoft has been recognized as a Leader, reaffirming its commitment to delivering comprehensive, AI-powered, and integrated security solutions[…]
Read More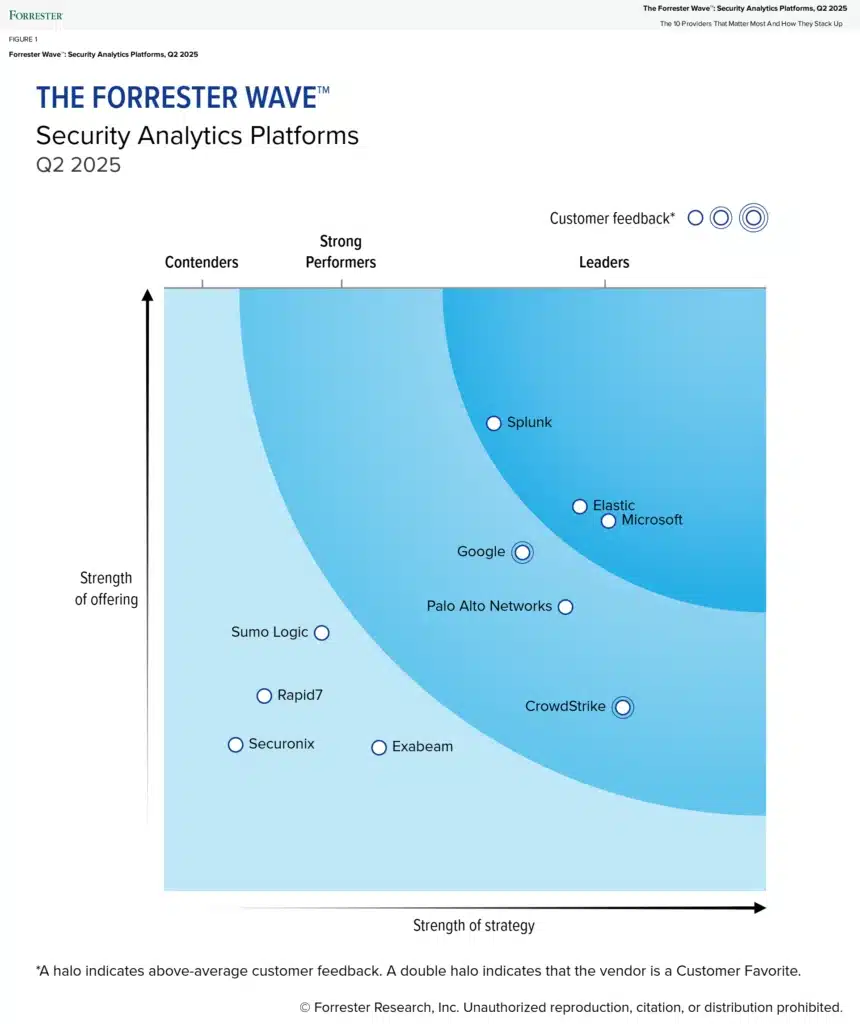
What is a security operations center? Learn more ↗ Microsoft is proud to be named a Leader in The Forrester Wave™: Security Analytics Platforms, Q2 2025—which we believe reflects our deep investment in innovation and commitment to support security operations centers (SOCs)’s critical mission. This strong result underscores[…]
Read More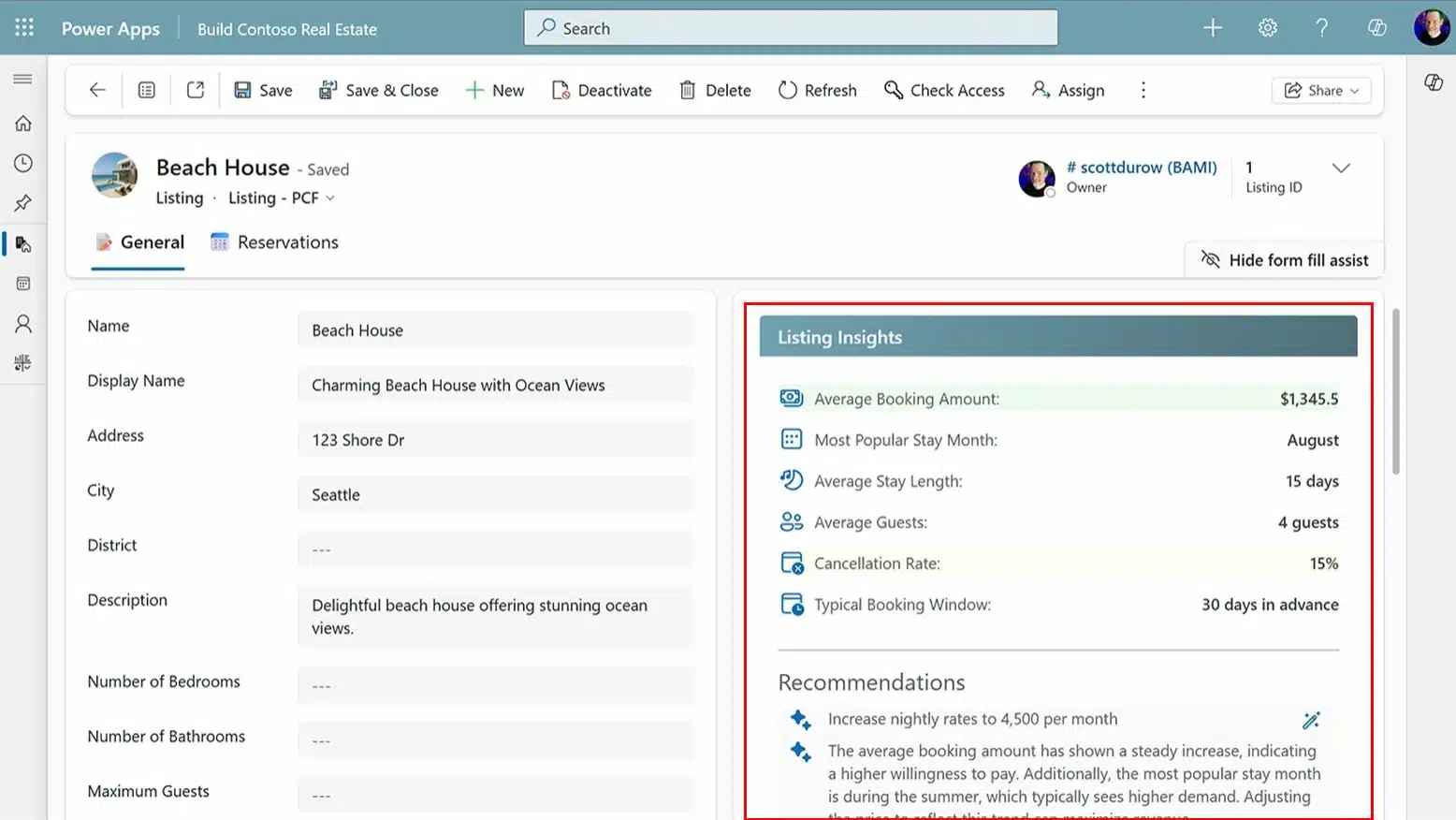
We’re excited to announce the public preview of two powerful new capabilities in Microsoft Power Apps: Agent APIs and Agent response component. These features were shown in the Microsoft Build session Extend your Copilot Agent in Power Apps with Copilot Studio and new SDK’s. With them, you unlock new ways[…]
Read More
Imagine steering a vessel through Arctic waters where 90% of iceberg mass lies hidden beneath the surface; your lookouts equipped only with telescopes and blind to the submerged threats. This parallels today’s cybersecurity landscape: According to the Microsoft Digital Defense Report 2024, nearly 80% organizations have attack paths[…]
Read More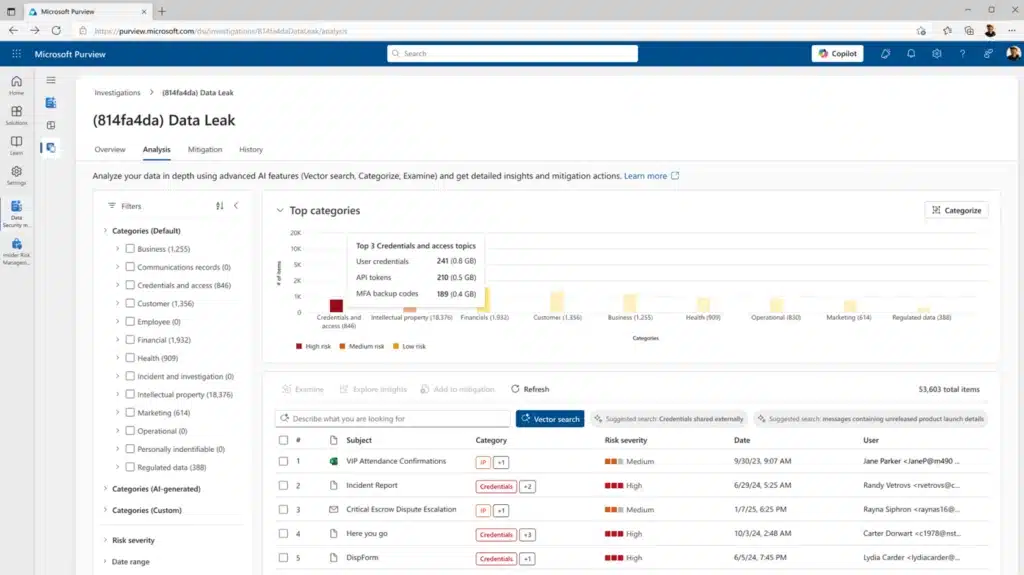
Seventy-four percent of organizations surveyed experienced at least one data security incident with their business data exposed in the previous year as reported in Microsoft’s Data Security Index: Trends, insights, and strategies to secure data report. Despite the best people, process and technology we can apply to prevent it,[…]
Read More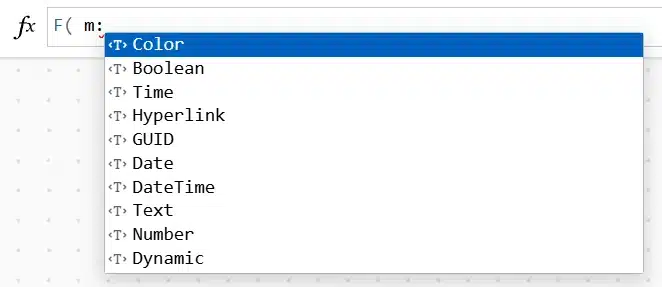
Taking another big step forward, Enhanced Component Properties (ECP) are now generally available (GA) and ready for your production workloads! ECPs are a great way to modularize and reuse your logic across an app, with the added bonus that ECPs can be shared across apps through a component[…]
Read More