Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [In preview] Public Preview: Azure Front Door Premium now supports Azure Private Link origins in UAE North 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- [Launched] Generally Available: Azure Databricks Supervisor Agent 10 Febbraio 2026
- 80% of Fortune 500 use active AI Agents: Observability, governance, and security shape the new frontier 10 Febbraio 2026
- Manipulating AI memory for profit: The rise of AI Recommendation Poisoning 10 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- [In preview] Public Preview: Application Gateway for Containers – AKS managed add-on 9 Febbraio 2026
- A one-prompt attack that breaks LLM safety alignment 9 Febbraio 2026
- Analysis of active exploitation of SolarWinds Web Help Desk 7 Febbraio 2026

We are excited to share the latest developments in Customer Managed Key (CMK) management for Power Platform Environments. As data security evolves, organizations must keep up with best practices and technology to protect sensitive information. Customer Managed Key (CMK) solutions give organizations direct control over encryption keys, strengthening[…]
Read MoreEver had a critical app crash at the worst possible moment, or a vital flow suddenly stop sending emails? With Monitor, you don’t have to wait for end-users to complain. Now generally available and enabled by default, no setup required, Monitor gives makers and admins real-time visibility, powerful metrics, and[…]
Read MoreDataverse Knowledge takes center stage in Microsoft Copilot Studio’s latest update—with support for multi-line text and file columns, plus improved answer consistency. These enhancements make agents built in Copilot Studio more intuitive, insightful, and reliable—helping users uncover business-critical information even when it’s buried in long notes or attachments. […]
Read More
Generative pages aims to redefine how makers build with Microsoft Power Apps—bringing the power of vibe coding to enterprise development in model-driven apps. With just a few prompts, makers can generate rich, responsive pages backed by real React and TypeScript code, all while maintaining enterprise-grade governance and reliability.[…]
Read More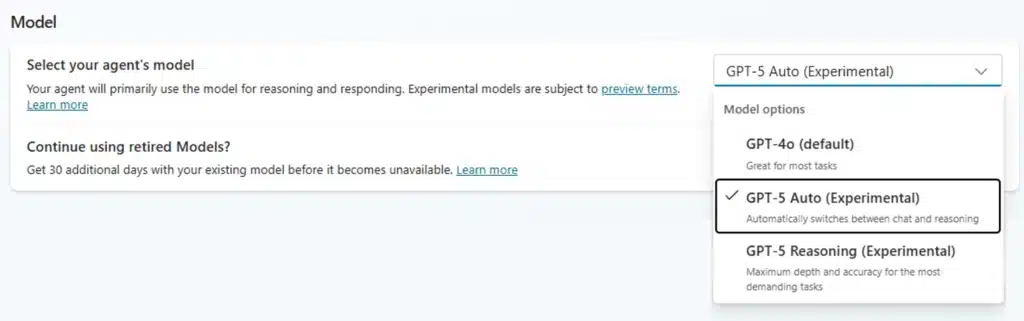
Starting today, Microsoft Copilot Studio users will have access to GPT-5, OpenAI’s best generative AI system that was introduced this morning. With this release, we are also introducing support in Copilot Studio for you to choose your agent’s model for generative answers and orchestration from a curated set optimized by[…]
Read MoreIntelligent triage for a more agile, autonomous SOCAt Microsoft Secure 2025, we introduced a new wave of innovations across Microsoft Defender aimed at redefining what AI can do for security operations. At the center of these announcements was the launch of 11 Security Copilot agents, each purpose-built to[…]
Read More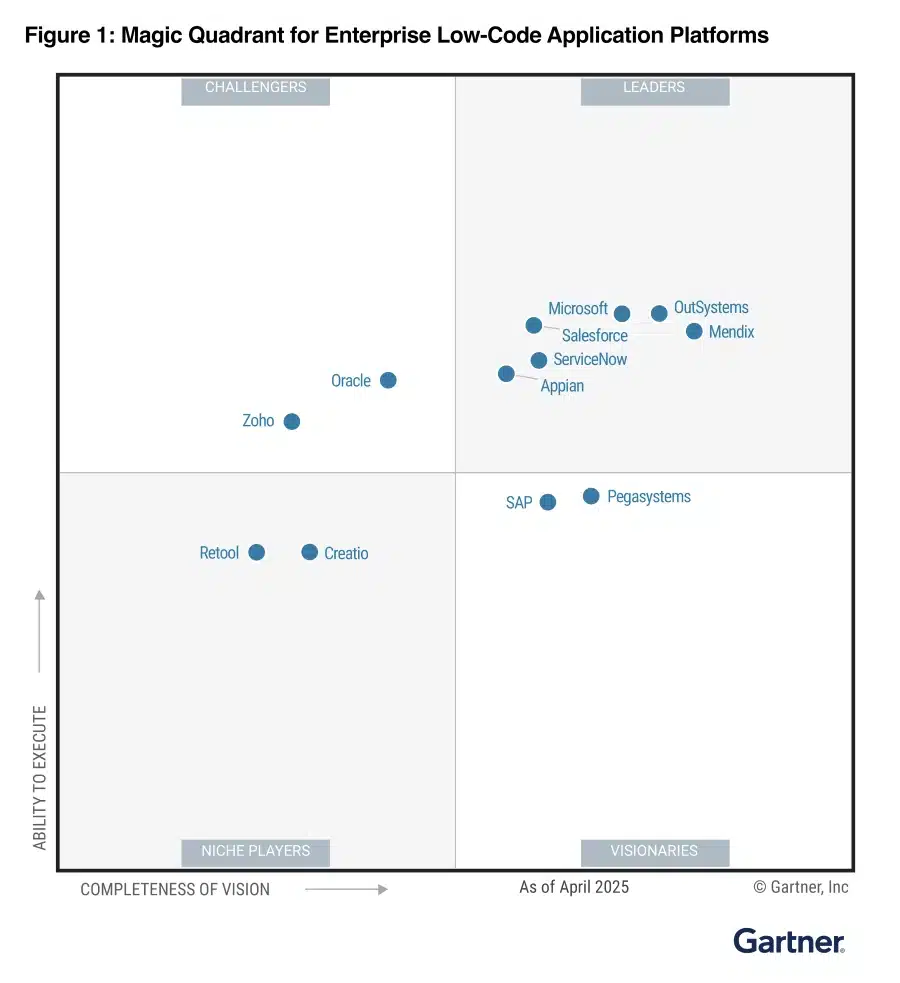
We’re proud to share that Microsoft has again been named a Leader in the 2025 Gartner® Magic Quadrant™ for Enterprise Low-Code Application Platforms (LCAP). This is the seventh consecutive time we have been named a Leader in this Magic Quadrant™. We’re honored by this recognition in a market[…]
Read More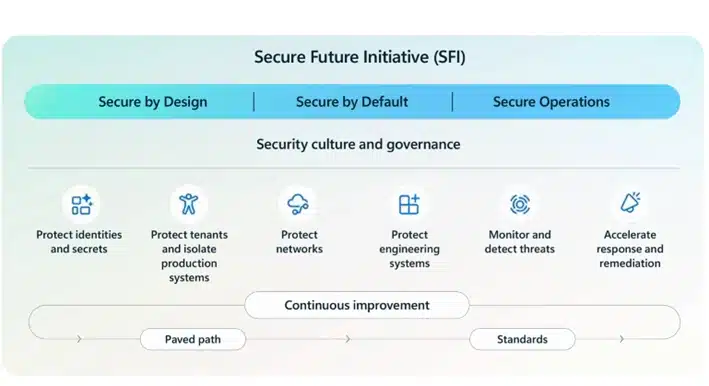
We’re excited to launch Microsoft Secure Future Initiative (SFI) patterns and practices: a new library of actionable guidance designed to help organizations implement security measures at scale. This launch marks the next step in our journey to make our SFI learnings practical for our customers, partners, and broader[…]
Read MoreDefender Experts now offers 24/7, expert-driven protection for cloud workloads, beginning with hybrid and multicloud servers in Microsoft Defender for Cloud. Additionally, third-party network signals can be used in Microsoft Defender Experts for XDR to enhance incidents for faster and more accurate detection and response. Co-authors: Henry Yan,[…]
Read More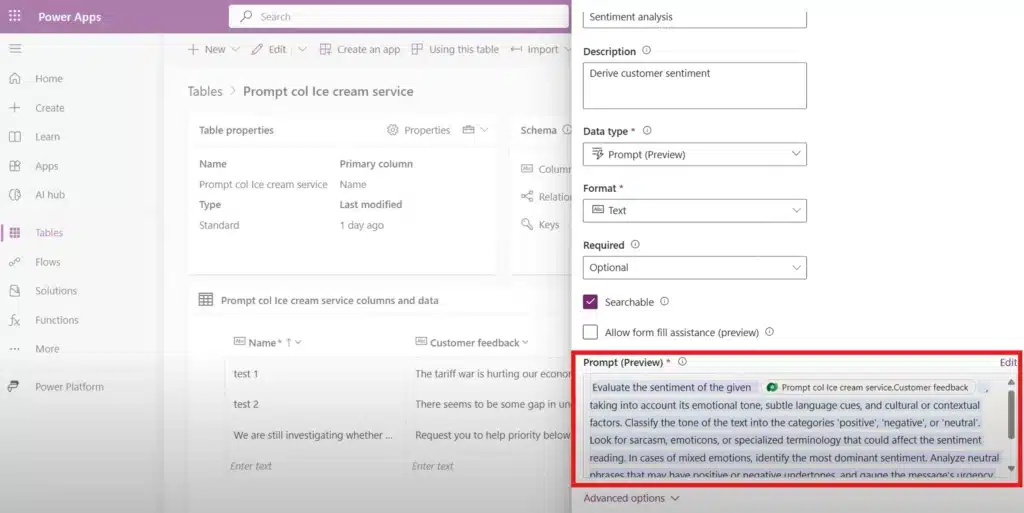
Microsoft Dataverse continues to evolve as a foundational platform for building intelligent, secure, and scalable business solutions. We are excited to announce the public preview of Prompt Columns, a new way to embed generative AI directly into your Dataverse tables. This capability will enable dynamic business logic, context-aware[…]
Read More